Kit de exploração do pôr do sol foi detectado em campanhas de malvertising ativas em setembro passado. Naquela época, o kit de exploração estava entregando o ransomware CryLocker, juntamente com o RIG EK. Infelizmente, pesquisadores de segurança da TrendMicro descobriram que o Sundown foi atualizado recentemente, o que significa que um aumento nos ataques de ransomware e malware deve ser esperado. Considerando a natureza da ferramenta de hack, ele pode continuar a ser implantado na distribuição de ransomware e malware. Na última campanha, pesquisadores detectaram chthonic Trojan bancário sendo a carga útil da operação.
relacionado: Locky Ransomware faz amizade com o Bizarro Sundown Exploit Kit
Kit de exploração do pôr do sol última atividade foi detectada em dezembro 27, 2016, onde os invasores usaram imagens PNG para armazenar as informações coletadas e o código de exploração. Nos ataques de setembro com a carga útil sendo o ransomware CryLocker, Os arquivos PNG também foram usados para empacotar as informações coletadas do usuário. As imagens foram então enviadas para um álbum Imgur para que os cibercriminosos pudessem evitar a detecção.
Recursos de esteganografia do Sundown Exploit Kit
Pesquisadores da TrendMicro relataram que o kit de exploração foi atualizado recentemente com técnicas de esteganografia. Como um resultado, os arquivos PNG agora são usados não apenas para armazenar informações coletadas, mas também para ocultar o código de exploração:
Em dezembro 27, 2016, notamos que o Sundown foi atualizado para usar técnicas semelhantes. Os arquivos PNG não foram usados apenas para armazenar informações coletadas; os designers de malware agora usavam esteganografia para ocultar seu código de exploração.
O que é esteganografia? É uma técnica avançada implantada para ocultar código malicioso em uma imagem para contornar a detecção baseada em assinatura. É uma técnica popular vista em ataques de malvertising baseados em kits de exploração. A campanha de publicidade maliciosa GooNky é um bom exemplo, pois usou várias táticas para ocultar o tráfego, como mover parte do código malicioso em imagens para escapar da detecção.
Neste novo Kit de exploração do pôr do sol Por exemplo, os invasores realmente não ocultaram os dados na imagem em si – eles anexaram o código malicioso no final do arquivo, pesquisadores explicam.
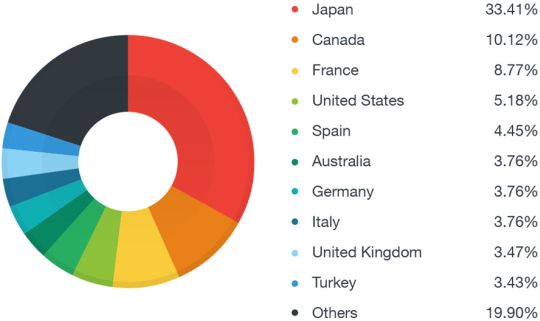
O EK atualizado foi visto em malvertising campanhas de distribuição de malware no Japão, Canadá, e França, com usuários japoneses representando mais de 30 por cento de todas as metas. Veja imagem abaixo (por TrendMicro):
Nesta versão atualizada, o malvertisement do kit de exploração cria um iframe oculto que se conecta automaticamente à página de destino do Sundown. A página irá recuperar e baixar uma imagem PNG branca.
CVE-2015-2419 Alavancado nos últimos ataques do kit Sundown Exploit
Os pesquisadores também descobriram que o código de exploração dentro da imagem PNG também incluía um código de exploração direcionado ao CVE-2015-2419 vulnerabilidade.
CVE-2015-2419 Descrição
JScript 9 no Microsoft Internet Explorer 10 e 11 permite que atacantes remotos executem código arbitrário ou causem uma negação de serviço (corrupção de memória) por meio de um site elaborado, aka “Vulnerabilidade de corrupção de memória JScript9.”
além do que, além do mais, uma exploração Flash para CVE-2016-4117 também foi recuperada pelo código de exploração. A própria página de destino inclui uma exploração direcionada a outro Internet Explorer (IE) vulnerabilidade, CVE-2016-0189, nota pesquisadores.
Curiosamente, todas as explorações mencionadas acima foram corrigidas e usadas por outros kits de exploração em todo o 2016.
relacionado: Topo 3 Vulnerabilidades Usado em 2016 Exploit Ataques Kit
Proteção contra Sundown Exploit Kit e outros EKs
Os kits de exploração têm sido usados em escala industrial. Eles são kits de ferramentas automatizados que fazem a varredura do navegador de um usuário, e analisá-lo em busca de falhas antes de entregar a carga maliciosa. Isso significa que seu navegador deve estar sempre totalmente corrigido - nunca estime a importância das atualizações de segurança. Os usuários devem instalar correções de segurança imediatamente para todos os seus softwares - assim que os patches forem lançados.
No caso de um patch ainda não ter sido lançado, um ataque baseado nesta vulnerabilidade ainda pode ser desviado por um software antimalware atualizado. A maioria desses programas detectará e interceptará os exploits que tentam tirar vantagem de uma falha.
digitalizador Spy Hunter só irá detectar a ameaça. Se você quiser a ameaça de ser removido automaticamente, você precisa comprar a versão completa da ferramenta anti-malware.Saiba Mais Sobre SpyHunter Anti-Malware Ferramenta / Como desinstalar o SpyHunter