 Spear Phishing-Angriffe haben sich zu einer der größten Bedrohungen Organisationen gedreht werden derzeit gegenüber. Spear Phishing-Versuche sind typisch für gezielte Angriffe, die auf finanziellen Gewinn oder Geschäftsgeheimnisse Ziel. Diesem speziellen Social-Engineering-Muster kann eine Reihe hochentwickelter Malware-Eingriffe folgen. Es ist in der Tat eine Angelegenheit, die von Unternehmen angegangen werden sollte.
Spear Phishing-Angriffe haben sich zu einer der größten Bedrohungen Organisationen gedreht werden derzeit gegenüber. Spear Phishing-Versuche sind typisch für gezielte Angriffe, die auf finanziellen Gewinn oder Geschäftsgeheimnisse Ziel. Diesem speziellen Social-Engineering-Muster kann eine Reihe hochentwickelter Malware-Eingriffe folgen. Es ist in der Tat eine Angelegenheit, die von Unternehmen angegangen werden sollte.
Laut einer aktuellen Umfrage, in der Daten von 300 Firmen (aus den USA und Großbritannien) wurde analysiert, nur 20% der Teilnehmer identifizieren die Ergebnisse von Spear Phishing und glauben, dass es sich um ein Top-Sicherheitsproblem handelt.
Was genau ist Spear Phishing??
Spear Phishing ist jeder Versuch eines E-Mail-Betrugs, der anscheinend von einer dem Empfänger bekannten Person oder Entität gesendet wird. Tatsächlich, Die E-Mail wurde von einem Angreifer gesendet. Der Zweck von Spear-Phishing-Angriffen besteht darin, finanzielle oder persönliche Daten zu stehlen, oder Zugang zu vertraulichen Informationen suchen.
Was ist der Unterschied zwischen Phishing und Spear Phishing??
Das Speerwort verdeutlicht den Unterschied. Phishing-Angriffe können als nicht zielgerichtete Angriffe wahrgenommen werden, richtet sich an eine breite Gruppe von Nutzern. Phishing beinhaltet ein Social-Engineering-System und eine Form von technischem Betrug. Es wird weiterhin eine Phishing-E-Mail gesendet, um Benutzer dazu zu verleiten, auf schädliche Links zu klicken oder schädliche Dateien herunterzuladen. Jedoch, mit Spear Phishing, Bestimmte Personen sind betroffen. Es ist bekannt, dass solche Personen Zugang zu Verschlusssachen haben, und in den meisten Fällen, Sie sind Mitarbeiter in großen Unternehmen.
Spear Phishing kann als die Entwicklung von Phishing wahrgenommen werden, als nächstes Level. Viele Speerangriffe haben überall stattgefunden 2015, und wenn Unternehmen ihre Lektion nicht lernen, Sie werden weiterhin unter enormen finanziellen Verlusten leiden.
Mehr zu gezielten Angriffen:
Trochilus-RAS-Trojaner
Cyber Space Auswirkungen 2015
Spear Phishing bei gezielten Angriffen 2015
Was die meisten gezielten Angriffe auslöst, ist normalerweise nur eine unschuldig aussehende E-Mail, die schädliche Dateien enthält. Die Statistiken beweisen es. Laut der Umfrage haben wir am Anfang erwähnt, jene 300 Unternehmen haben verloren $1.6 Millionen pro Sicherheitsvorfall.
Die Umfrage wurde von Cloudmark durchgeführt, ein in San Francisco ansässiges Unternehmen, und Vanson Bourne, ein intelligenter Marktforschungsanbieter. Was Experten entdeckt haben, ist ziemlich alarmierend. In den letzten zwei Jahren gab es viele hochkarätige schädliche Datenverletzungen, die durch eine intelligent gestaltete Spear-Phishing-E-Mail ausgelöst wurden. Die Regel gilt sowohl für finanzielle Gewinnangriffe als auch für Hacks gegen Regierungen und private Unternehmen.
Kein Unternehmen ist vor Spear Phishing sicher - Unternehmen aus verschiedenen Geschäftsbereichen sind Opfer geworden, nur weil einer ihrer Mitarbeiter einen „kleinen“ Fehler gemacht hat.
Die Umfrage ist die erste, die Unternehmensdaten speziell zum Prozentsatz der Cyberangriffe sammelt, die Spear Phishing insgesamt darstellt. Die Befragten sagten dies in der Vergangenheit 12 Monate 84 Prozent gaben an, dass ein Spear-Phishing-Angriff in ihre Sicherheitsabwehr eingedrungen war. Diese Statistiken weisen auf eine weit verbreitete Unfähigkeit hin, sich gegen diese Angriffe zu verteidigen.
Weiter, Spear-Phishing-E-Mails erwiesen sich als die häufigste Methode, mit 90% der Angriffe, die durch einen solchen Auslöser ausgelöst werden. Die zweitwahrscheinlichste Art der Penetration war Spear Phishing auf mobilen Plattformen (48%). Den dritten Platz belegen soziale Netzwerke (40%). Wechselmedien wurden von ins Visier genommen 30% von Spear-Phishing-Angriffen.
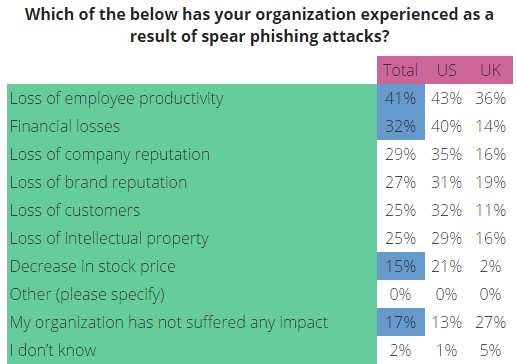
Image Source: https://blog.cloudmark.com/
Was folgt nach einer erfolgreichen Spear-Phishing-Kampagne??
Nach den Ergebnissen der Umfrage, Es folgten Spear-Phishing-Angriffe:
- Malware (34%);
- Erkennung von Authentifizierungsdaten (30%);
- Anfragen nach Unternehmensinformationen (25%);
- Betrugsattacken (9%).
Eine weitere interessante Entdeckung war, dass IT-Experten hauptsächlich von Spear Phishing betroffen waren (44%), gefolgt von Finanzpersonal (43%). Es ist nur logisch, dass diese beiden Abteilungen am meisten leiden würden - sie haben am meisten Zugang zu Daten und Geld.
Ergreifen Unternehmen Vorsichtsmaßnahmen gegen Spear Phishing??
71% der an der Umfrage teilnehmenden Unternehmen gaben an, bereits einen angemessenen Schutz gegen „Speere“ implementiert zu haben.. Außerdem, 56% der Unternehmen haben Schulungen durchgeführt, um zu verhindern, dass es in Zukunft zu Spear Phishing kommt.
Schauen Sie sich die ganze Cloudmark-Umfrage.













