Nichts verkörpert die Entwicklung der digitalen Verbrechen ganz wie Crimeware-as-a-Service. Jahre zuvor, schlechte Schauspieler preyed auf ahnungslose Nutzer von vor allem auf ihre technischen Geschick unter Berufung. Sicher, sie konnten ihre Techniken im IRC-Foren teilen, Letztendlich war es jedoch Sache des einzelnen Angreifers, seine Schadprogramme zu codieren und zu debuggen. Niemand würde es für sie tun.
Heute, Malware-Entwickler sind immer noch da draußen. Aber nicht jeder Angreifer ist ein Programmierer. Es gibt einige schlechte Schauspieler mit geringem technischen Fachwissen. Diese Personen würden viel lieber helfen, das Programm eines anderen zu verbreiten… nur solange sie einen Teil der Beute ihrer Angriffskampagnen behalten können.
Diese Präferenz hat zu Crimeware-as-a-Service geführt, Ein Modell, unter dem jeder eine Lizenz für ein digitales Angriffstool erwerben kann. Diese Programme verfügen häufig über eine Weboberfläche, über die Partner ihre Kampagnen anpassen können’ Ziele und Vorwände. Am Ende jeder Lizenzperiode, Die Lizenznehmer dürfen einen Teil des Gewinns behalten, Ein Bruchteil geht auch an den ursprünglichen Entwickler. Einige Lizenzen verfallen nach kurzer Zeit 30 Tage. Andere halten ein Leben lang.
Betrug als Dienstleistung
Die Sicherheitsgemeinschaft hat Crimeware-as-a-Service in Form von gesehen Ransomware und Remote Access Trojaner (RATs). Es ist jetzt auf eine weitere Iteration des Underground-Affiliate-Modells gestoßen: Betrug in einer Box.
Scam in a Box bezieht sich auf einen Dienst, über den Kriminelle mit geringem technischem Fachwissen die Infrastruktur erwerben können, Fehlerbehebung, und Wartung notwendig, um einen überzeugenden Betrug online zu verüben. Beispielsweise, Ein Dienst namens Inboundpopaps gibt an, dass er bietet “Anwendungen,” “Registrierungsreiniger,” und “Antiviren-Pakete.” eingehende Anrufe zu erhöhen.
Das lange und kurze davon? William Tsing von Malwarebytes erklärt:
Schön geschnitten und trocken. „Wir stellen schädliche Software für betrügerische Zwecke zur Verfügung.’ Beachten Sie auch das Eingeständnis, dass PUPs und Betrug durch den technischen Support Hand in Hand gehen. Weitere Informationen zu dieser Verbindung, siehe Pieters Beitrag hier. Inboundpopaps ist wesentlich schlauer als die meisten Betrügereien auf dem Markt, und versucht sogar, den Verkehr auf real zu beschränken, zahlende Kunden.
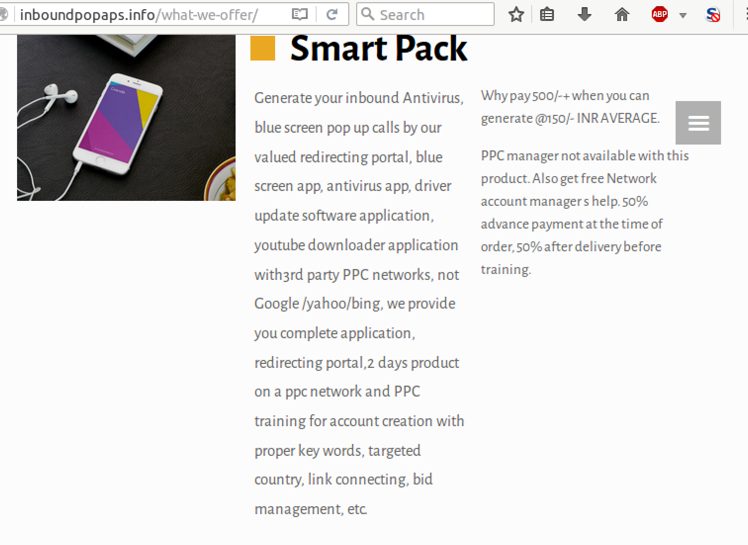
Inboundpopaps bietet Käufern verschiedene Produkte an. Ein Dienst hat angerufen “Smart Pack” hilft Kriminellen, ihre eigenen zu schaffen “Antivirus, Bluescreen-Popup-Anrufe,” Mit anderen Worten, Kunden können das Angebot nutzen, um ihren eigenen Betrug mit technischem Support zu erstellen.
Smart Pack wird mit einer App geliefert, ein Umleitungsportal, und sogar Pay-per-Click (PPC) Schulung zur Verwendung geeigneter Schlüsselwörter und zur Geolokalisierung.
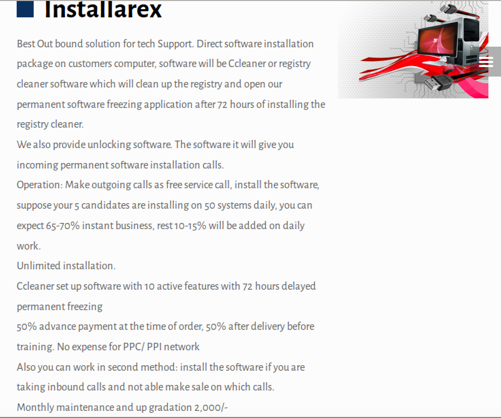
Ein weiterer Service, “Installarex,” ist eine Software, die einen Registry Cleaner nachahmt. Aber das ist es nicht wirklich. Es ist eigentlich ein Bildschirmschließfach, das aktiviert wird 72 Stunden nach der Installation.
50 Prozent der Servicekosten sind zum Zeitpunkt des Kaufs fällig, während der Rest nach der Lieferung und vor dem Training kommt. Sobald dieser Betrag bezahlt ist, Kriminelle können damit machen, was sie wollen. Das schließt ein “Installieren[ing] die Software, wenn Sie eingehende Anrufe entgegennehmen und keinen Verkauf für welche Anrufe tätigen können.”
Deutlich, Die Entwickler haben sich überlegt, wie Smart Pack, Installarex, und ihre anderen Dienste können zusammen gebündelt werden.
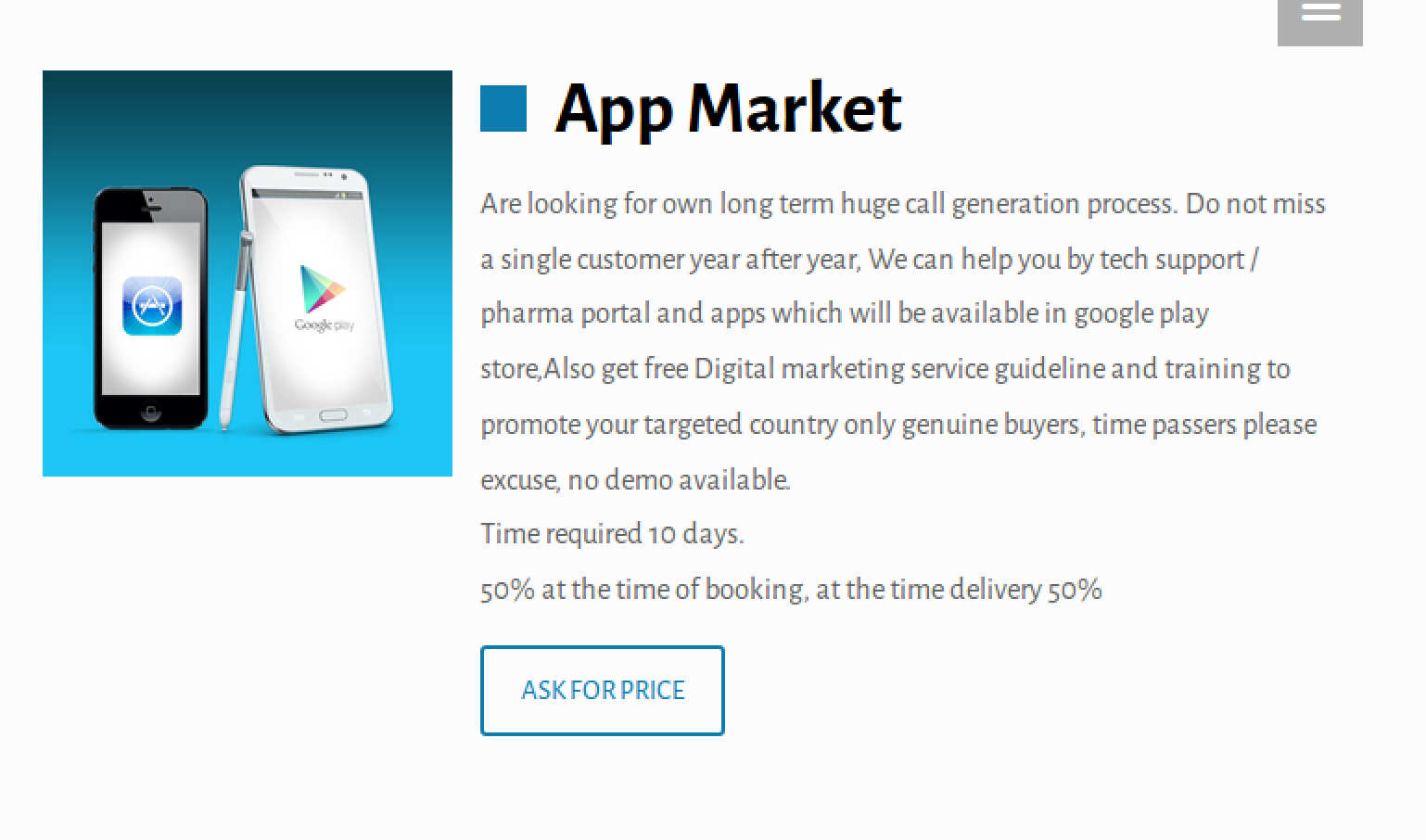
Last but not least ist App Market. Tsing belastet das Produkt:
…[Die]Wir sehen Angebote für gefälschte mobile Apps, zusammen mit Schulungen, wie man sie in verschiedene App Stores schleicht. Dies ist faszinierend, da Betrug durch mobilen technischen Support nicht sehr häufig ist. Leider, so sehr wir es lieben würden, nach dem Preis zu fragen, Dieser Link lädt einfach die Seite neu. Der Klappentext für Windows-Schließfächer zitiert die monatliche Wartung als 2000 IND pro Monat, was ungefähr entspricht $30 USD. Angesichts dessen ist der Preis für einen der ressourcenintensiveren Betrügereien, man könnte annehmen, dass die anderen noch billiger sind.
Abschluss
Scam-in-a-Box-Lösungen wie die von Inboundpopaps machen es Kriminellen mit geringem technischem Fachwissen leicht einen Betrug verüben. Infolge, Es wäre dumm von uns zu glauben, dass Betrug bald verschwinden wird. Aus diesem Grund müssen sich Benutzer vor einigen der häufigsten Betrugsfälle schützen. Sie können dies tun, indem sie einen Werbeblocker installieren und legitime Software direkt von Anbietern herunterladen’ Websites und nicht von skizzenhaften Marktplätzen von Drittanbietern.
Anmerkung der Redaktion:
Von Zeit zu Zeit, SensorsTechForum Features Gäste Artikel von Cyber-Sicherheit und infosec Führer und Enthusiasten wie diesem Beitrag. Die Meinungen in dieser Bewertung der Beiträge zum Ausdruck, jedoch, denen der mitwirkenden Autoren sind vollständig, und nicht über die in der SensorsTechForum reflektieren.