Uma estação base transceptora (BTS) é um equipamento que auxilia na comunicação sem fio entre o equipamento do usuário (celulares, Telefones WLL, computadores com conectividade sem fio) e uma rede, como tecnologias de comunicação sem fio como GSM, CDMA, loop local sem fio, Wi-Fi, WiMAX ou outra tecnologia WAN. Os pesquisadores acabaram de descobrir três vulnerabilidades críticas em software popular executado em BTS de código aberto. O que tudo isso significa?
Uma estação móvel conectada a um BTS; image Source: Zimperium
Vulnerabilidades em vários produtos BTS de código aberto encontradas
pesquisadores da Zimperium dizem que têm investigado continuamente os vários aspectos da segurança do GSM (i.e. vulnerabilidades de protocolo). A equipe prestou muita atenção aos produtos de software de código aberto mais populares que executam redes GSM. Enquanto este processo de auditoria de origem continuou, a equipe tropeçou em várias falhas encontradas em tal software. As falhas permitem que um invasor comprometa uma estação BTS e, eventualmente, assuma o controle de seu módulo transceptor remotamente.
Os pesquisadores explicam que um BTS é baseado em software e equipamento de rádio que permite que estações móveis se conectem ao GSM, UMTS, e redes LTE.
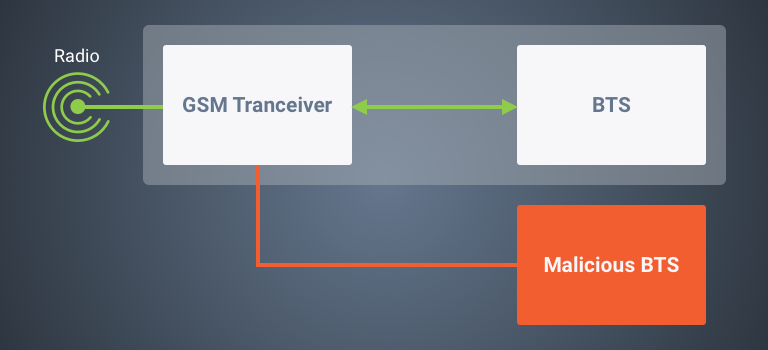
O software de nível inferior por trás de qualquer BTS é o transceptor, que é a interface direta com o hardware de rádio. É responsável pela sintonia de frequência e pelo manuseio do GMSK (Gaussian Minimum Shift Keying) modulação / desmodulação de dados. Em resumo, ele digitaliza as ondas de rádio.
A equipe descobriu que todos os softwares BTS mais comumente disponíveis são executados na mesma base de código de transceptor ou muito idêntica. Isso significa que todas essas peças de software estariam sujeitas às mesmas vulnerabilidades.
A pior dessas vulnerabilidades permite que um agente malicioso obtenha controle remoto sobre o módulo transceptor. Isso levaria ao comprometimento das funcionalidades do BTS através da representação de um BTS paralelo.
para resumir, a exploração bem-sucedida dessas falhas pode fazer com que os invasores ganhem controle remoto sobre as estações base do transceptor, sequestrando tráfego GSM, impedindo a torre de fornecer serviço, divulgando informações de tráfego, alterando a identidade BTS, etc.
Vulnerabilidades BTS: Quem é afetado?
A lista de partes afetadas inclui versões específicas de YateBTS (por Legba Incorporated), OpenBTS e OpenBTS-UMTS (por Range Networks), Osmo-TRX e Osmo-BTS (por OsmoCOM). Também é altamente provável que outros produtos que compartilham a mesma base de código do transceptor também estejam em perigo.
Produtos Afetados:
- YateBTS <= 5.0.0
- OpenBTS <= 4.0.0
- OpenBTS-UMTS <= 1.0.0
- Osmo-TRX / Osmo-BTS <= 0.1.10
- Outros produtos que compartilham a mesma base de código do transceptor.
Fornecedores Afetados:
- Legba Incorporated (YateBTS)
- Redes de alcance (OpenBTS e OpenBTS-UMTS)
- OsmoCOM (Osmo-TRX e Osmo-BTS)
Resumindo, pesquisadores classificaram as vulnerabilidades em três grupos:
Vinculação de serviço excessivamente exposta, que pode permitir que qualquer invasor com conectividade IP ao sistema BTS receba e envie pacotes de / para o transceptor.
Estouro de buffer baseado em pilha remota, onde um invasor pode estourar um buffer de pilha, enviando um pacote UDP superdimensionado para o canal de controle. Isso pode levar à execução remota de código (RCE) ou uma negação de serviço (DoS) condição.
Controle Remoto Não Autenticado, onde um invasor pode negar serviço desligando o módulo, frequências de congestionamento sintonizando o rádio TX na frequência errada, ou sequestrar a identidade do BTS remotamente usando o comando SETBSIC para alterar a identidade do BTS para outra.
Etapas de mitigação contra as vulnerabilidades de BTS
Os pesquisadores da Zimperium forneceram uma lista de etapas de mitigação para os fornecedores seguirem e aplicarem imediatamente para que seus produtos estejam protegidos contra exploits:
1. Atualize seu software BTS quando um patch está disponível.
2. Ligue os soquetes usados para controle e troca de dados apenas para a interface local (127.0.0.1).
3. Firewall: Bloqueie o tráfego proveniente de redes externas para portas 5701 ( porta de controle ) e 5702 ( porta de dados), ou outras portas usadas pelo seu software BTS.
4. Certifique-se de aplicar mitigações de tempo de compilação (ASLR + DEP)
5. Implementar um sistema de autenticação para esses canais negar um invasor sem privilégios conectado na mesma máquina, ou na mesma rede, de se comunicar com as portas de controle BTS.
6. Corrigir o manuseio do buffer usando tamanhos corretos.
7. Executar auditorias de código adicionais.