A base transceiver station (BTS) is a piece of equipment that aids wireless communication between user equipment (mobile phones, WLL phones, computers with wireless connectivity) and a network, such as wireless communication technologies like GSM, CDMA, wireless local loop, Wi-Fi, WiMAX or other WAN technology. Researchers have just discovered three critical vulnerabilities in popular software running on open-source BTS. What does this all mean?
A mobile station connecting to a BTS; Image Source: Zimperium
Vulnerabilities in Multiple Open Source BTS Products Found
Researchers at Zimperium say that they have been continuously investigating the various aspects of GSM security (i.e. protocol vulnerabilities). The team has paid close attention to the most popular open source software products that run GSM networks. While this process of source auditing continued, the team stumbled upon multiple flaws found in such software. The flaws enable an attacker to compromise a BTS station and eventually take control over its transceiver module remotely.
Researchers explain that a BTS is based on software and radio equipment that allows mobile stations to connect to the GSM, UMTS, and LTE networks.
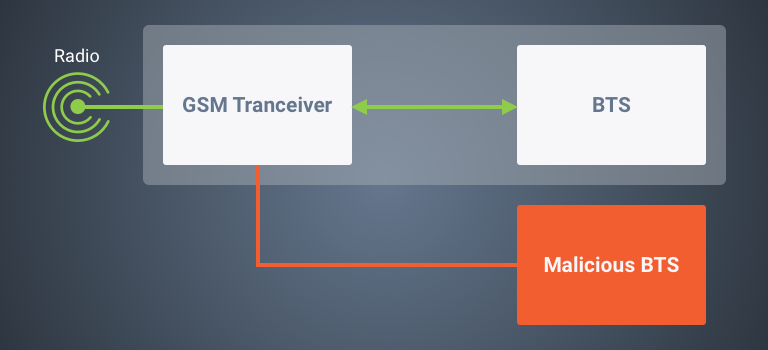
The lower level software behind any BTS is the transceiver, which is the direct interface to the radio hardware. It is responsible for frequency tuning and handling GMSK (Gaussian Minimum Shift Keying) data modulation/demodulation. In short, it digitizes the radio waves.
The team discovered that all of the most commonly available BTS software runs on the same or very identical transceiver code base. This means that all of these software pieces would be prone to the same vulnerabilities.
The worst of these vulnerabilities enable a malicious actor to gain remote control over the transceiver module. This would lead to the jeopardizing of the BTS functionalities through impersonating a parallel BTS.
To summarize, the successful exploitation of these flaws could lead to attackers gaining remote control over the base transceiver stations, hijacking GSM traffic, preventing the tower from providing service, disclosing traffic information, altering the BTS identity, etc.
BTS Vulnerabilities: Who Is Affected?
The list of affected parties includes specific versions of YateBTS (by Legba Incorporated), OpenBTS and OpenBTS-UMTS (by Range Networks), Osmo-TRX and Osmo-BTS (by OsmoCOM). It’s also highly likely that other products that share the same transceiver code base are also endangered.
Affected Products:
- YateBTS <= 5.0.0
- OpenBTS <= 4.0.0
- OpenBTS-UMTS <= 1.0.0
- Osmo-TRX/Osmo-BTS <= 0.1.10
- Other products that share the same transceiver code base.
Affected Vendors:
- Legba Incorporated (YateBTS)
- Range Networks (OpenBTS and OpenBTS-UMTS)
- OsmoCOM (Osmo-TRX and Osmo-BTS)
To sum up, researchers have classified the vulnerabilities in three groups:
Overly Exposed Service Binding, which could allow any attacker with IP connectivity to the BTS system to receive and send packets from/to the transceiver.
Remote Stack-Based Buffer Overflow, where an attacker can overflow a stack buffer by sending an oversized UDP packet to the control channel. This could lead to remote code execution (RCE) or a denial of service (DoS) condition.
Remote Unauthenticated Control, where an attacker can deny service by turning the module off, jam frequencies by tuning the TX radio to the wrong frequency, or hijack BTS identity remotely using the SETBSIC command to change the BTS identity to another one.
Mitigation Steps against the BTS Vulnerabilities
Zimperium researchers have provided a list of mitigation steps for vendors to follow and apply immediately so that their products are safe from exploits:
1. Update your BTS software when a patch is available.
2. Bind the sockets used for control and data exchange only to the local interface (127.0.0.1).
3. Firewall: Block traffic coming from external networks to ports 5701 ( control port ) and 5702 ( data port), or other ports as used by your BTS software.
4. Be sure to apply compile time mitigations (ASLR + DEP)
5. Implement an authentication system for such channels to deny an unprivileged attacker logged on the same machine, or on the same network, from communicating with BTS control ports.
6. Fix buffer handling by using correct sizes.
7. Perform additional code audits.