Um novo tipo de ataque poderia permitir que um ator malicioso com uma câmera térmica de gama média a teclas de captura pressionada em um teclado padrão. A descoberta foi feita por três professores da Universidade da Califórnia. Em outras palavras, o resíduo térmico de nossos dedos nas teclas do teclado pode ser registrado por um hacker que pode usá-lo posteriormente para revelar as senhas do usuário ou qualquer outro texto que ele tenha digitado.
O Ataque do Thermanator Explicado
“Se você digitar sua senha e se afastar ou se afastar, alguém pode aprender muito sobre isso após o fato,” disse o professor Gene Tsudik da equipe acadêmica.
O ataque foi chamado de Thermanator e pode ser usado para recuperar informações confidenciais do usuário, como senhas e PINs, bem como sequências curtas de texto. O ataque do Thermanator requer que várias condições sejam atendidas para funcionar corretamente. Primeiro, os atacantes precisam colocar uma câmera especializada com recursos de gravação térmica perto da vítima. A câmera também deve ser capaz de capturar as teclas do teclado da vítima, caso contrário, não vai funcionar.
De acordo com a explicação dos pesquisadores sobre o ataque do Thermanator (Vejo papel), é um tipo distinto de ataque interno, onde um cenário de ataque típico prossegue nas etapas a seguir:
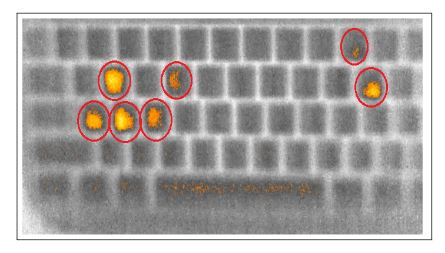
DEGRAU 1:A vítima usa um teclado para inserir uma senha genuína, como parte do login (ou desbloqueio de sessão) procedimento.
DEGRAU 2:Pouco depois, a vítima também: (1) voluntariamente se afasta, ou (2) se afasta, do local de trabalho.
DEGRAU 3:Usando imagens térmicas (v.g., fotos tiradas por uma câmera FLIR comum) o adversário coleta resíduos térmicos do teclado.
DEGRAU 4:Mais tarde, o adversário usa o "mapa de calor" das imagens para determinar as teclas pressionadas recentemente. Isso pode ser feito manualmente (i.e., via inspeção visual) ou automaticamente (i.e.,
via software especializado).
Com esses requisitos sendo atendidos, o invasor torna-se capaz de descobrir as teclas pressionadas pela vítima, mesmo sem conhecimento especial de hacking. As chaves capturadas podem ser montadas em possíveis strings e podem ser implantadas em um ataque de dicionário. Um ataque de dicionário é uma técnica popular para decifrar cifras e mecanismos de autenticação ao tentar determinar a chave de descriptografia ou frase-senha. Isso é feito usando centenas ou até milhões de possibilidades prováveis.
Os pesquisadores realizaram vários experimentos onde tiveram 31 os usuários inserem senhas em quatro modelos de teclado diferentes. Então, oito não especialistas em hacking foram solicitados a obter o conjunto de teclas pressionadas usando os dados registrados da câmera térmica. Os resultados desses testes revelaram que os dados térmicos registrados até 30 segundos após a entrada de texto são suficientes para um invasor não profissional recuperar todo o conjunto de teclas que o usuário-alvo pressionou.
Se você é o tipo de usuário que pressiona uma tecla por vez usando apenas dois dedos, é mais suscetível ao ataque do Thermanator.
Existe alguma conclusão para a descoberta do Thermanator dos pesquisadores?
pouco colocá, a pesquisa “expõe a vulnerabilidade dos sistemas baseados em senhas padrão à coleção adversária de emanações térmicas”. Com base nos resultados do estudo, os pesquisadores acreditam que esses ataques “representam uma nova ameaça confiável para sistemas baseados em senhas”, sugerindo que pode ser hora de reavaliar o uso de senhas.