MacRansom e MacSpy são duas amostras de novos malwares Mac que foi criado pela mesma pessoa. Essa pessoa também está oferecendo as duas peças para venda por meio do modelo de malware-como-um-serviço em dois portais dark web. Clientes em potencial e aspirantes a cibercriminosos são instruídos a entrar em contato com o autor por meio de um endereço Protonmail.
Pesquisadores da AlienVault e Fortinet decidiram entrar em contato com o criminoso para que eles tenham a chance de analisar MacRansom e MacSpy. A primeira coisa que os pesquisadores da Fortinet apontaram, Contudo, diz respeito à ampla crença de que os Macs estão protegidos contra ataques de ransomware e malware.
“É verdade que é menos provável que um usuário do Mac OS seja atacado ou infectado por malware do que um usuário do Windows, mas isso não tem nada a ver com o nível de vulnerabilidade no sistema operacional. É em grande parte causado pelo fato de que mais de 90% dos computadores pessoais rodam no Microsoft Windows e apenas cerca de 6% no Mac OS da Apple," elas explicado.
Então, quais são as especificidades das amostras de malware para Mac recém-descobertas?
Mais sobre MacSpy
Pelo visto, MacSPy tem duas versões: uma versão básica gratuita e uma avançada que pode ser comprada em Bitcoins.
Quanto aos recursos maliciosos do MacSpy, o malware é um simples RAT/spyware projetado para capturar capturas de tela, gravar audio, roubar fotos, recuperar o conteúdo da área de transferência, roubar históricos de navegação e baixar dados, e tinha recursos de keylogging. O malware também se comunicou via Tor. Quanto à versão avançada que está disponível por um determinado preço - ela pode recuperar qualquer arquivo ou dados da máquina da vítima. Também é capaz de criptografar o diretório do usuário, conceder acesso a contas de e-mail e sociais, entre outras coisas.
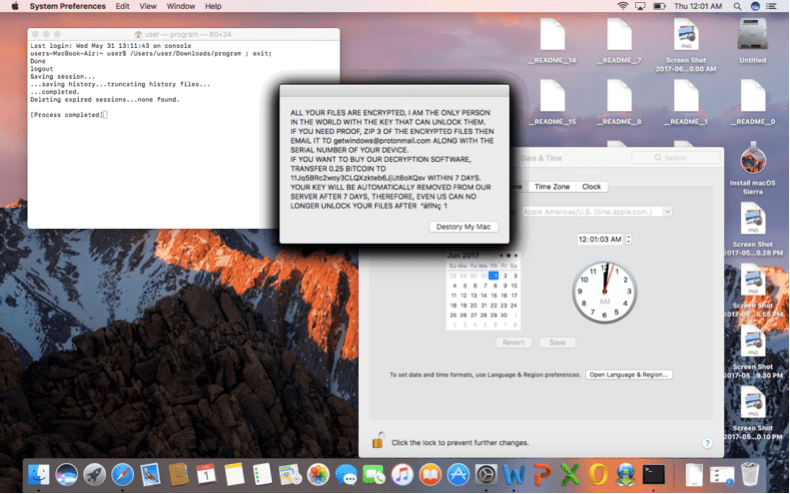
Mais sobre MacRansom
De acordo com seu desenvolvedor, MacRansom usa criptografia inquebrável. Contudo, mais detalhes não são fornecidos. A análise dos pesquisadores da Fortinet mostra que o ransomware só pode criptografar até 128 arquivos por meio de criptografia simétrica com uma chave codificada. O desenvolvedor usou dois conjuntos de chaves simétricas: um ReadmeKey e um TargetFileKey.
“O ReadmeKey é usado para descriptografar o arquivo ._README_ que contém as notas e instruções de resgate, enquanto o TargetFileKey é usado para criptografar e descriptografar os arquivos da vítima,”Escreveram os pesquisadores, acrescentando que:
Uma coisa notável que observamos quando a engenharia reversa do algoritmo de criptografia / descriptografia é que o TargetFileKey é permutado com um número gerado aleatoriamente. Em outras palavras, os arquivos criptografados não podem mais ser descriptografados assim que o malware for encerrado - o TargetFileKey será liberado da memória do programa e, portanto, torna-se mais desafiador criar um decodificador ou ferramenta de recuperação para restaurar os arquivos criptografados.
além do que, além do mais, MacRansom não tem a capacidade de se comunicar com um comando & Servidor de controle para TargetFileKey, o que significa que não há uma cópia preparada da chave para descriptografar os arquivos. “Contudo, ainda é tecnicamente possível recuperar o TargetFileKey. Uma das técnicas conhecidas é usar um ataque de força bruta. Não deve demorar muito para uma CPU moderna forçar bruta uma chave de 8 bytes quando a mesma chave é usada para criptografar arquivos conhecidos com conteúdo de arquivo previsível. mesmo assim, ainda estamos céticos quanto à afirmação do autor de poder descriptografar os arquivos sequestrados, mesmo assumindo que as vítimas enviaram ao autor um arquivo aleatório desconhecido,”Concluíram os investigadores.
O que MacRansom e MacSpy têm em comum?
Como mencionado no início, as duas peças parecem ter sido cunhadas pelo mesmo desenvolvedor. MacRansom e MacSpy compartilham os mesmos mecanismos anti-análise, e também use o mesmo método para criar um ponto de lançamento para que a peça inicie na reinicialização do sistema.
Nem o MacRansom nem o MacSpy são assinados digitalmente, o que significa que, se um usuário baixar um deles e executá-lo, o sistema operacional exibirá um aviso informando que o programa vem de um desenvolvedor não identificado. O desenvolvedor do malware também diz aos usuários para obter acesso físico à máquina de destino para instalá-lo e executá-lo.