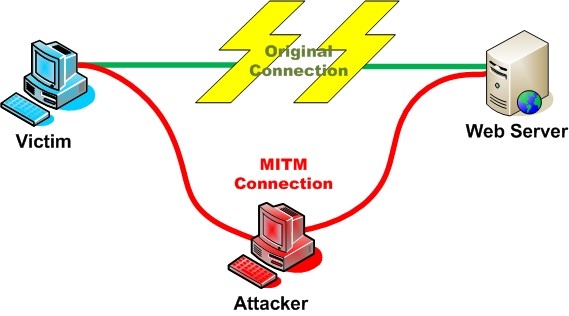
Um novo tipo Man-in-the-Middle (MITM) Um ataque chamado “DoubleDirect” está se espalhando pela Internet atualmente. O que o ataque faz é redirecionar o tráfego de conexões sem fio de grandes domínios de sites como o Facebook, Google, Twitter, para sites infectados por malware. Caindo em tal, os hackers podem roubar certificados, credenciais e outros dados pessoais, bem como infectar com malware suas vítimas.
Método de Trabalho DoubleDirect
O novo malware foi encontrado por pesquisadores da empresa de segurança Zimperium. Sua técnica consiste em desviar as tabelas de rotas das Mensagens de Controle do Protocolo da Internet (ICMP) de um hospedeiro para outro. Os protocolos estão sendo usados como roteadores para direcionar a máquina dos usuários para uma maneira melhor de um local específico na Internet.
“DoubleDirect usa pacotes de redirecionamento ICMP (tipo 5) para modificar as tabelas de roteamento de um host. Isso é legitimamente usado por roteadores para notificar os hosts na rede que uma rota melhor está disponível para um determinado destino ”, Pesquisadores do Zimperium escreveram em um post sobre o assunto.
Sujeitos aos Ataques
Sujeitos ao ataque são dispositivos com iOS (Incluindo 8.1.1.), OS X (incluindo Yosemite) e Android (incluindo Lollipop) que geralmente aceitam redirecionar rotas por padrão. O ataque não está funcionando no Windows e no Linux porque eles não permitem o redirecionamento do tráfego.
Normalmente, o redirecionamento do ICMP pode ser feito durante o envio, ou ao receber dados através de uma conexão sem fio, mas não pode ser aplicado a ambos. A novidade do DoubleDirect é que ele pode executar o ataque MitM simultaneamente para ambos, o que o torna bastante perigoso para as máquinas infectadas.
Analisando o ataque, os pesquisadores do Zimperium provaram que os hackers realizam uma pesquisa de DNS antes do ataque para determinar quais endereços IP a vítima visita. A próxima etapa que executam é enviar as mensagens de protocolo para todos os IPs encontrados. O ataque é conhecido por ser ativo em 31 países até agora - Argélia, Austrália, Áustria, Bahrain, Brasil, Canadá, China, Colômbia, Egito, Finlândia, França, Alemanha, Grécia, Índia, Indonésia, Iraque, Israel, Itália, Cazaquistão, Letônia, Malta, México, Países Baixos, Polônia, Federação Russa, Arábia Saudita, Sérvia, Espanha, Suíça, Reino Unido e Estados Unidos.
As redes corporativas também são vulneráveis a esses ataques, e os pesquisadores apresentaram uma ferramenta simples para a detecção de ataques DoubleDirect. Você pode conferir aqui.