Há um novo exploit kit na cidade, e é chamado Spelevo EK. De acordo com relatórios, o exploit kit está usando a vulnerabilidade CVE-2018-15982 para ter acesso a sistemas desatualizados. A vulnerabilidade está localizado no Flash Player.
Versões do Flash Player 31.0.0.153 e anteriores, e 31.0.0.108 e anteriores têm uso após vulnerabilidade gratuita, lê seu aviso oficial. A exploração bem-sucedida da falha pode levar à execução arbitrária de código.
No início deste mês, pesquisador de malware Kafeine twittou sobre o novo kit de exploração:
Parece que há um novo EK na cidade (CVE-2018-15982 dentro). Vejo 85.17.197[.101. Eu pensei pela primeira vez no GrandSoft, mas não é isso. Lembra o SPL EK (uma evolução?). Indo para “SPELEVM” como nome.
A vulnerabilidade CVE-2018-15982 foi usada anteriormente em ataques direcionados nos quais os invasores usavam documentos maliciosos do Word que incluíam um arquivo Flash com a vulnerabilidade. O documento do Word foi incluído em um arquivo RAR com uma imagem JPG. Ao disparar a vulnerabilidade do Flash, o malware extraiu o código RAT incorporado na imagem JPG.
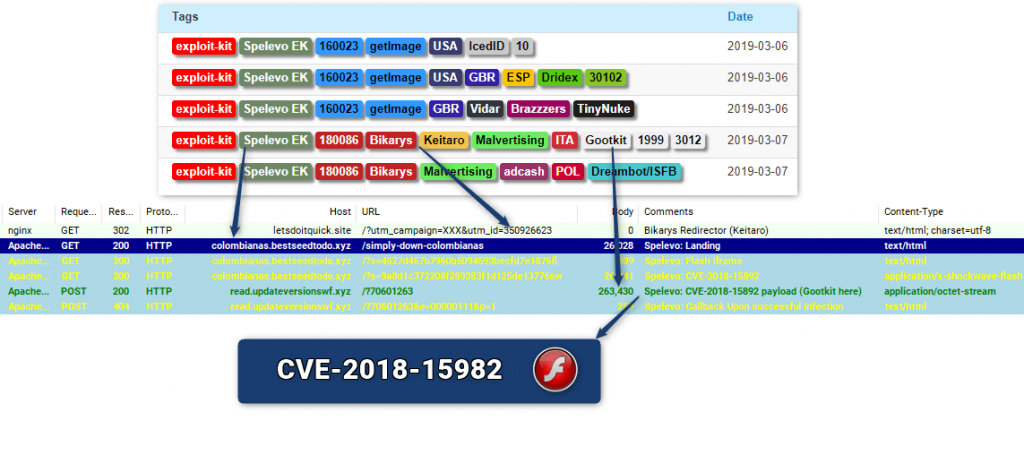
Detalhes técnicos do Spelevo Exploit Kit CVE-2018-15982
Acredita-se que o kit de exploração Spelevo tenha algumas semelhanças com o "SPL EK". Observe que o kit de exploração SPL foi visto principalmente em 2012 e 2013, e foi mais frequentemente associado ao ZeroAccess e Scareware / FakeAV.
O uso da vulnerabilidade CVE-2018-8174 também foi identificado lá, pesquisadores de malware dizem.
O kit de exploração pode estar distribuindo o Backdoor.Win32.Gootkit.K também conhecido como backdoor do Gootkit. Ano passado, invasores invadiram a rede do MailChimp para enviar faturas e e-mails falsos com malware, Gootkit incluído. Em um caso particular, A conta MailChimp da Red Bull Records foi comprometida e abusada para distribuir um email de phishing com tema da Apple. Parecia que a rede da Mailchimp foi abusada para distribuir a porta dos fundos por quatro meses inteiros, disse o pesquisador Kevin Beaumont.
O que fazer se você acredita que foi comprometido
A primeira coisa a fazer é atualizar o Flash Player para a versão mais recente, que não é explorável. Como já foi dito, CVE-2018-15982 é uma vulnerabilidade que permite a execução remota de código no Flash Player até 31.0.0.153. A vulnerabilidade foi corrigida em dezembro 05, 2018. Você pode consultar o boletim oficial de segurança para mais detalhes.
A próxima etapa é garantir que seu sistema não seja afetado por malware. Se você verificar seu sistema com um programa anti-malware, e o programa detecta um backdoor como o Gootkit, você deve considerar remover a ameaça imediatamente. Ter um backdoor ou qualquer forma de software malicioso em seu sistema pode levar a uma variedade de cenários catastróficos.
Um Trojan backdoor, ou um RAT, é utilizado para fornecer acesso remoto ao sistema ou rede infectado. Graças a backdoors, cibercriminosos decidem quando iniciar a exploração, e quais atividades maliciosas ocorrerão no ataque. Backdoors podem ser usados para enviar e receber dados, operações de lançamento, exibir informações ou reiniciar o PC. Um computador infectado também pode se tornar um participante silencioso em uma rede botnet ou zumbi.