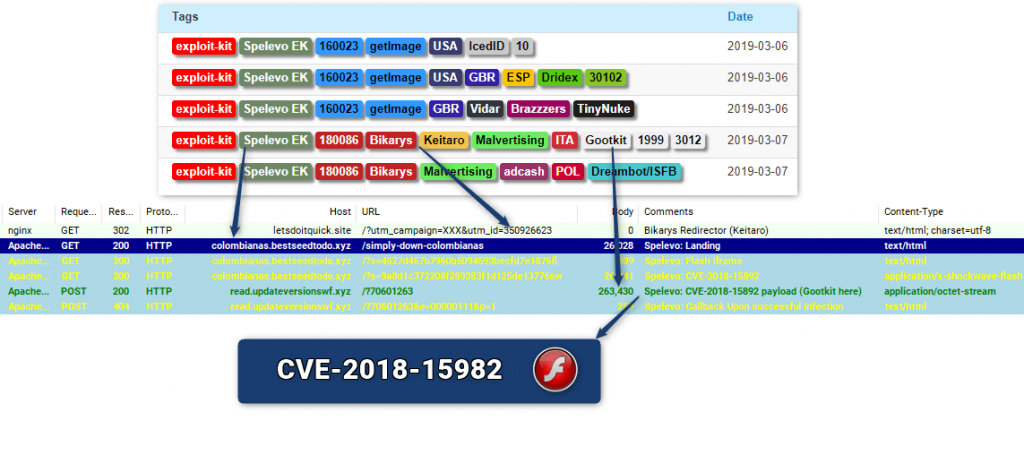
There’s a new exploit kit in town, and it’s called Spelevo EK. According to reports, the exploit kit is using the CVE-2018-15982 vulnerability to gain access to unpatched systems. The vulnerability is located in Flash Player.
Flash Player versions 31.0.0.153 and earlier, and 31.0.0.108 and earlier have a use after free vulnerability, reads its official advisory. Successful exploitation of the flaw could lead to arbitrary code execution.
Earlier this month, malware researcher Kafeine tweeted about the new exploit kit:
It looks like there is a new EK in town (CVE-2018-15982 inside). See 85.17.197[.101. I first thought about GrandSoft but that’s not it. Reminds SPL EK (an evolution?). Going for “Spelevo” as name.
The CVE-2018-15982 vulnerability was previously used in targeted attacks in which attackers used malicious Word documents that included a Flash file with the vulnerability. The Word document was included in a RAR archive with a JPG picture. Upon triggering the Flash vulnerability, the malware extracted the RAT code embedded in the JPG picture.
Spelevo Exploit Kit CVE-2018-15982 Technical Details
The Spelevo exploit kit is believed to have some similarities with “SPL EK”. Note that the SPL exploit kit was mainly seen in 2012 and 2013, and was most often associated with ZeroAccess and Scareware/FakeAV.
The use of the CVE-2018-8174 vulnerability has been spotted there as well, malware researchers say.
The exploit kit may be distributing Backdoor.Win32.Gootkit.K also known as the Gootkit backdoor. Last year, attackers hacked into MailChimp’s network to send fake invoices and emails ridden with malware, Gootkit included. In one particular case, Red Bull Records’ MailChimp account was compromised and abused to distribute an Apple-themed phishing email. It appeared that Mailchimp’s network was abused to distribute the backdoor for four whole months, said researcher Kevin Beaumont.
What to do if you believe you’ve been compromised
The very first thing to do is to update your Flash Player to its latest version which is not exploitable. As already said, CVE-2018-15982 is a vulnerability that allows remote code execution in Flash Player up to 31.0.0.153. The vulnerability was patched on December 05, 2018. You can refer to the official security bulletin for further details.
The next step is making sure that your system hasn’t been affected by malware. If you scan your system with an anti-malware program, and the program detects a backdoor such as Gootkit, you should considering removing the threat immediately. Having a backdoor or any form of malicious software on your system can lead to a variety of catastrophic scenarios.
A backdoor Trojan, or a RAT, is utilized to give remote access to the infected system or network. Thanks to backdoors, cybercriminals get to decide when to initiate the exploit, and what malicious activities will take place in the attack. Backdoors may be used to send and receive data, launch operations, display information or reboot the PC. An infected computer can also become a silent participant in a botnet or zombie network.