Tentativas de phishing do Gmail foram registradas. Pesquisadores de segurança do Wordfence detectaram uma técnica de phishing altamente eficaz e amplamente difundida que rouba credenciais de login para o Gmail e outros serviços. Pelo visto, durante as últimas semanas, usuários experientes em tecnologia comprometidos pelos ataques de phishing do Gmail têm compartilhado relatórios e detalhes para que mais usuários estejam cientes.
Ataque de phishing do Gmail: Detalhes técnicos
Gmail é o principal alvo dessas tentativas, mas outros serviços também são direcionados. É um esquema de phishing típico onde o invasor enviar um email para uma conta do Gmail. O e-mail pode parecer a ser enviado por alguém o alvo sabe, E isso é porque sua conta foi hackeada. O e-mail pode incluir um anexo de uma imagem. Ao clicar na imagem para visualizá-la, uma nova aba será aberta eo usuário será solicitado a fazer login no Gmail novamente. A barra de localização mostra o seguinte endereço: accounts.google.com, por isso mesmo o olho experiente pode ser enganado.
Assim que o login for concluído, a conta de destino está comprometida. Aqui está o que uma vítima do esquema de phishing compartilha:
Os invasores fazem login em sua conta imediatamente assim que obtêm as credenciais, e eles usam um de seus anexos reais, junto com uma de suas linhas de assunto reais, e envie para as pessoas da sua lista de contatos.
Por exemplo, eles entraram na conta de um aluno, puxou um anexo com um cronograma de prática da equipe atlética, gerou a captura de tela, e, em seguida, emparelhado com uma linha de assunto que estava tangencialmente relacionada, e enviei por e-mail para os outros membros da equipe atlética.
Todo o processo acontece muito rapidamente, e é automatizado ou os invasores estão em espera, processando as contas comprometidas.
Assim que o acesso a uma conta for obtido, o invasor tem acesso total a todos os e-mails da vítima, e também recebe acesso a outros serviços acessíveis por meio do mecanismo de redefinição de senha. Isso inclui outras contas de e-mail, Serviços SaaS, etc.
A descrição completa deste ataque de phishing do Gmail está disponível em Wordfence.
Esquemas de phishing geralmente comprometem serviços populares como o Google
Ano passado, Os pesquisadores da Webroot estabeleceram que o Google é a empresa com o maior impacto negativo de uma falsificação de identidade. Estas são descritas como organizações de alto risco, com 21% de todos os sites de phishing no período de janeiro a setembro 2016 fingir ser Google.
No topo de tudo, os atacantes ficam inquietos quando se trata de desenvolver novas táticas e vetores de ataque, e o phishing não é uma exceção. Informações confidenciais são altamente desejáveis, e a mudança para "software malicioso e atividades como serviço" só piora as coisas.
phishing Estatísticas, atualização de abril 2017
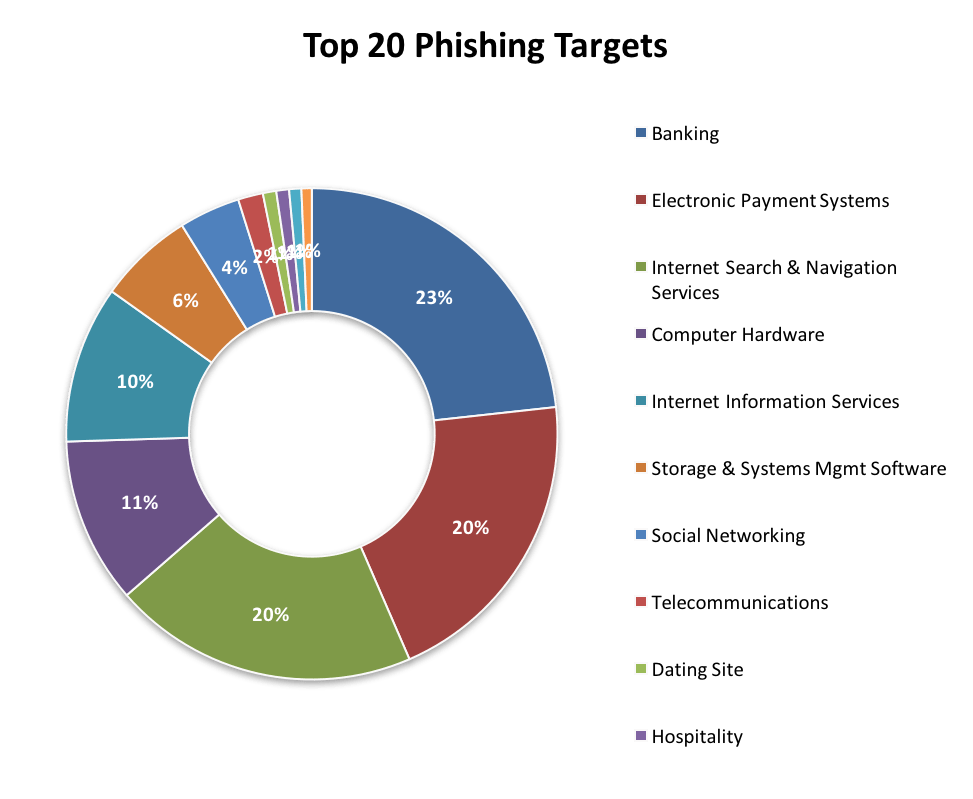
LookingGlass Cyber Solutions tem relatado um aumento na atividade de phishing na primeira semana de abril. A atividade geral de phishing aumentou em 30%, o aumento mais notável sendo registrado na indústria de Sistemas de Pagamento Eletrônico:
Não foram observadas tentativas de phishing do Gmail. Contudo, ataques de phishing em outros serviços foram. Dropbox foi direcionado em abril, 2017, por meio de e-mails habilmente elaborados que parecem legítimos. Um dos golpes envolvendo o Dropbox estava tentando colher as credenciais de login do Dropbox dos usuários usando uma solicitação de pedido que parecia legítima. O outro golpe foi tentar roubar a senha de e-mail do usuário por meio de uma solicitação falsa de compartilhamento de arquivo.
UMA Ataque de phishing no LinkedIn também foi detectado estar ativo em meados de abril. O esquema estava tentando enganar os usuários da rede profissional para fazer upload de seus currículos. Scammers estavam enviando e-mails sobre alegadas “aberturas de trabalho para os usuários do LinkedIn ativos”.
Como você notou, apesar dos diferentes alvos (Gmail, Dropbox, Facebook, LinkedIn, vários bancos, etc.) e-mails de phishing sempre têm muito em comum.
Dicas para se proteger contra tentativas de phishing
- Tenha cuidado com e-mails que exigem informações pessoais suas. Lembre-se de que os serviços legítimos normalmente não enviam essas solicitações por e-mail.
- Não se deixe enganar a revelar detalhes confidenciais, detalhes financeiros incluídos. Lembre-se de que os invasores também podem usar táticas de intimidação para induzi-lo a revelar informações de identificação pessoal.
- Tenha cuidado com solicitações de informações de aparência genérica. Um e-mail legítimo de uma organização legítima, como o banco de alguém, saberia o nome da pessoa. Os e-mails de phishing geralmente começam com “Prezado Senhor / Senhora”.
- Não envie informações confidenciais por meio de formulários em mensagens de e-mail.
- Não interaja com links ou anexos em um e-mail, a menos que tenha absoluta certeza de que o e-mail vem de uma fonte confiável.
- Certifique-se de que sua proteção anti-malware possui um recurso contra phishing.
digitalizador Spy Hunter só irá detectar a ameaça. Se você quiser a ameaça de ser removido automaticamente, você precisa comprar a versão completa da ferramenta anti-malware.Saiba Mais Sobre SpyHunter Anti-Malware Ferramenta / Como desinstalar o SpyHunter