Mais uma vez, o Android é vulnerável a um malware sério, e desta vez a escala da infecção é maior do que se poderia imaginar. Os pesquisadores de segurança se depararam com uma enorme, campanha incessante que infectou cerca de 5 milhões de dispositivos móveis em escala global. O malware foi apelidado de RottenSys.
Os invasores o ocultaram como um aplicativo de serviço de Wi-Fi do sistema que foi pré-instalado em milhões de novos dispositivos por marcas amplamente difundidas como Honor, Huawei, Xiaomi, OPPO, Vivo, Samsung, e GIONEE. Os dispositivos foram enviados por meio de Tian Pai, um distribuidor de telefones celulares com sede em Hangzhou, mas não se sabe se a empresa tem algo a ver com a campanha maliciosa.
Mais sobre a campanha de malware RottenSys Android
Pesquisadores da equipe de segurança móvel da Check Point descoberto uma nova família de malware amplamente difundida voltada para quase 5 milhões de usuários por receitas de publicidade fraudulentas. Pelo visto, este é um malware avançado projetado para assumir as permissões do Android para iniciar suas operações perniciosas.
De acordo com as descobertas, o malware começou a ser distribuído em setembro 2016. Em março deste ano, infectou 4,964,460 dispositivos, tornando-se uma das maiores campanhas de malware Android.
Como o RottenSys está ignorando a detecção?
Os agentes mal-intencionados por trás da operação obviamente sabem o que estão fazendo, já que o falso aplicativo do serviço System Wi-Fi não tem componentes maliciosos no início. Ele também não inicia nenhuma atividade suspeita e fica quieto por um tempo. Em vez de um comportamento agressivo, o malware está se comunicando com seu servidor de comando e controle para obter a lista dos componentes que realmente contêm código malicioso.
Então, o malware RottenSys continua baixando os componentes maliciosos silenciosamente, por meio da permissão DOWNLOAD_WITHOUT_NOTIFICATION que não requer nenhuma interação do usuário. Tipicamente, o malware baixa três componentes adicionais.
Assim que todos os componentes necessários forem baixados, RottenSys implanta uma estrutura de virtualização de aplicativos Android de código aberto chamada ‘Small’ (github.com/wequick/small). A estrutura permite que todos os componentes sejam executados simultaneamente para alcançar a funcionalidade maliciosa combinada de uma extensa rede de anúncios bruta que exibe anúncios na tela inicial do dispositivo na forma de janelas pop-up ou anúncios em tela inteira, os pesquisadores explicaram.
Para evitar que sua operação seja desligada pelo sistema Android, RottenSys usa outra estrutura de código aberto chamada MarsDaemon (github.com/Marswin/MarsDaemon). Enquanto o MarsDaemon mantém os processos vivos, também prejudica o desempenho do dispositivo e esgota a bateria.
Também é importante notar que o RottenSys está adaptado para empregar o Guang Dian Tong (Plataforma de anúncios Tencent) e o Ad Exchange do Baidu por sua operação de fraude publicitária. além disso, os pesquisadores dizem que o malware tem algumas variantes das cargas úteis (o conta-gotas e os componentes adicionais), e cada variante é adaptada para diferentes campanhas, tipo de dispositivo, plataforma de propaganda, e espalhar o canal.
Os pesquisadores identificaram dois C paralelos&Servidores C que foram usados pela RottenSys para sua operação. Elas "também conseguiu analisar os ataques e definir canais separados nos quais os atacantes operam e ainda verificar o volume de dispositivos infectados e anúncios fraudulentos exibidos aos usuários”.
O resultado final é que a operação da RottenSys é uma rede de anúncios extremamente agressiva:
No passado 10 dias sozinha, estourou anúncios agressivos 13,250,756 vezes, e 548,822 dos quais foram traduzidos em cliques em anúncios. Como um exemplo do possível fluxo de receita que os invasores desfrutam deste malware, nós [Os pesquisadores] calculou a receita dessas impressões e cliques de acordo com a estimativa conservadora de 20 centavos para cada clique e 40 centavos para cada mil impressões. De acordo com esses cálculos, os invasores ganharam mais de $ 115.000 com sua operação maliciosa apenas nos últimos dez dias!
O que pode ser feito para atenuar o RottenSys?
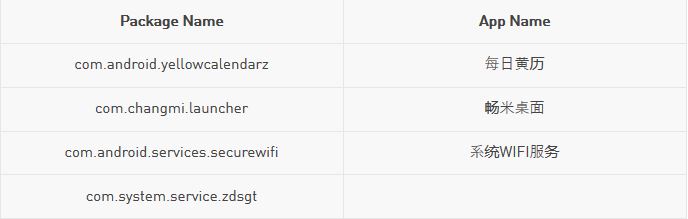
Os usuários devem desinstalar o conta-gotas RottenSys. Contudo, o nome exato do pacote deve ser conhecido para que seja removido completamente. Se você estiver vendo anúncios desconhecidos na tela inicial do seu novo telefone, vá para as configurações do sistema Android, em seguida, para o gerenciador de aplicativos, e localize os seguintes nomes de pacotes de malware possíveis. Em seguida, desinstale-os: