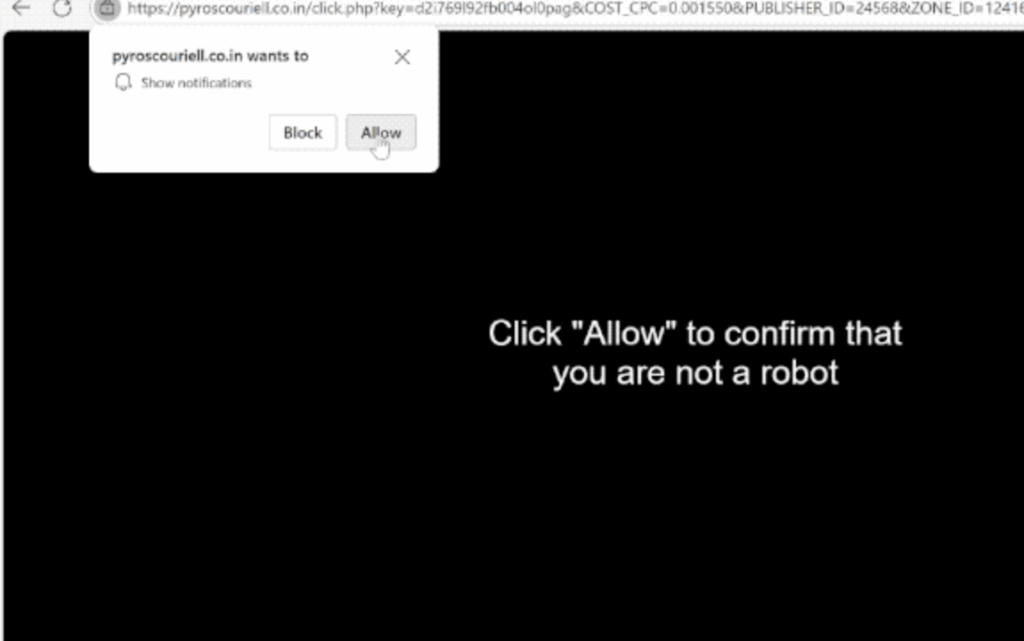
Pyroscouriell.co.in Pop-up Virus Removal Guide
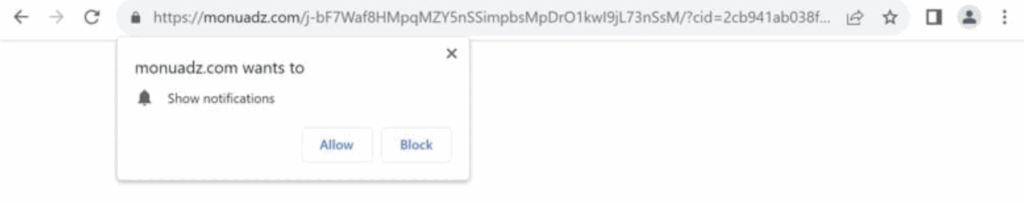
What Is Pyroscouriell.co.in? Pyroscouriell.co.in is a deceptive website that displays misleading pop-ups, often urging users to click “Allow” to confirm they’re not robots or to access content such as videos. In reality, this trick enables the site to send intrusive…