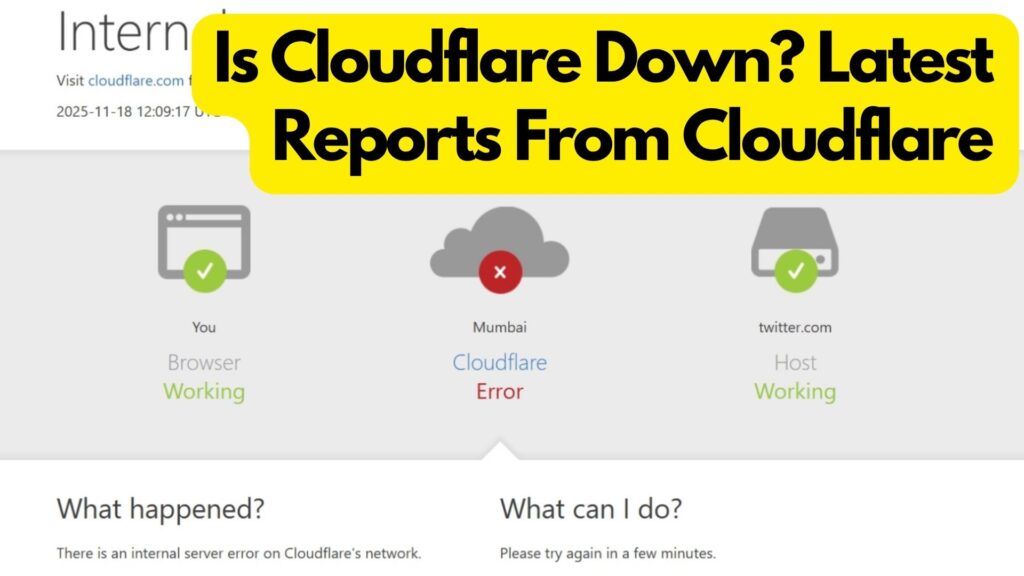
Is Cloudflare Down? Latest Reports From Cloudflare
Sensorstechforum.com Newsroom – November 18, 2025. A major outage at internet infrastructure provider Cloudflare today briefly broke large parts of the web, knocking services such as X (formerly Twitter), OpenAI’s ChatGPT, Canva and multiple other platforms offline or making them…


![Is Google Down? [Live Google Services Outage Report] is google down - google live outage report](https://cdn.sensorstechforum.com/wp-content/uploads/2025/09/is-google-down-1024x576.jpg)












