Mscoldness.com Pop-up Virus – How to Remove
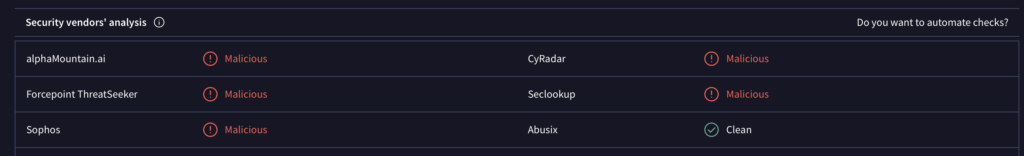
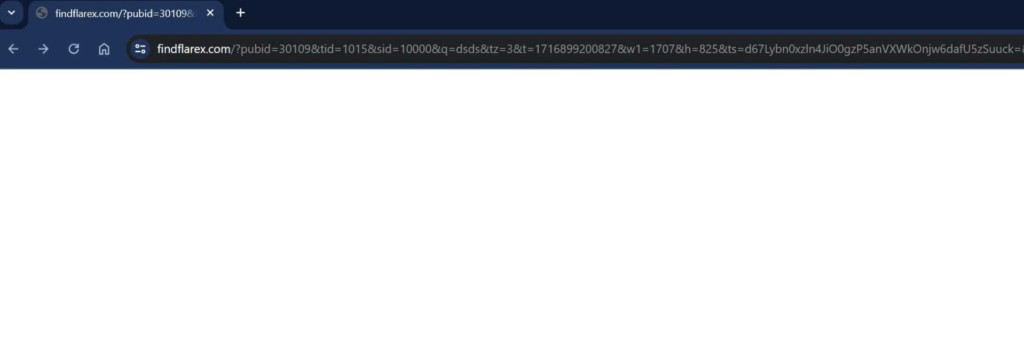
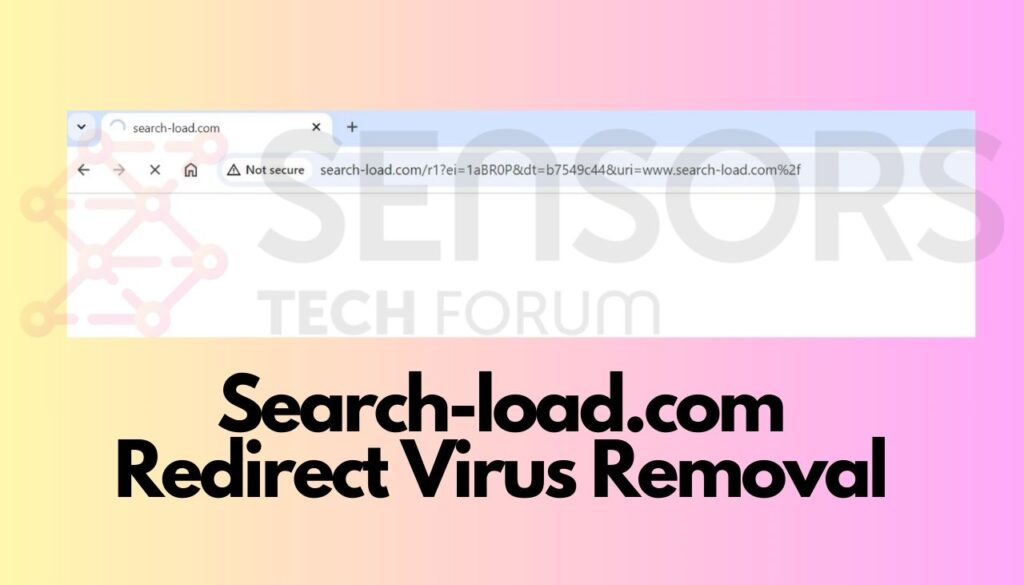
What Is Mscoldness.com? Mscoldness.com has been classified as a suspicious website that triggers fake pop-up alerts and push notifications. The appearance of the website in your browsing session may be a result of an adware infestation. Once an adware or…


![What Is taskhostw.exe? [Fix Guide] taskhostw exe issue](https://cdn.sensorstechforum.com/wp-content/uploads/2024/09/taskhostw-exe-issue-1024x327.png)

![SteamUnlocked – Is It Safe? [Virus Removal Guide] SteamUnlocked](https://cdn.sensorstechforum.com/wp-content/uploads/2024/09/SteamUnlocked--1024x420.png)

![Trojan:Win32/Wacatac – How to Remove It [Guide] TrojanWin32:Wacatac.G!ml](https://cdn.sensorstechforum.com/wp-content/uploads/2024/09/TrojanWin32Wacatac.Gml_-1024x752.png)


![“An Error Has Occurred in the Script on This Page” [Solved] An Error Has Occurred in the Script on This Page - Fix Guide](https://cdn.sensorstechforum.com/wp-content/uploads/2024/09/An-Error-Has-Occurred-in-the-Script-on-This-Page-Fix-Guide-1024x585.jpg)