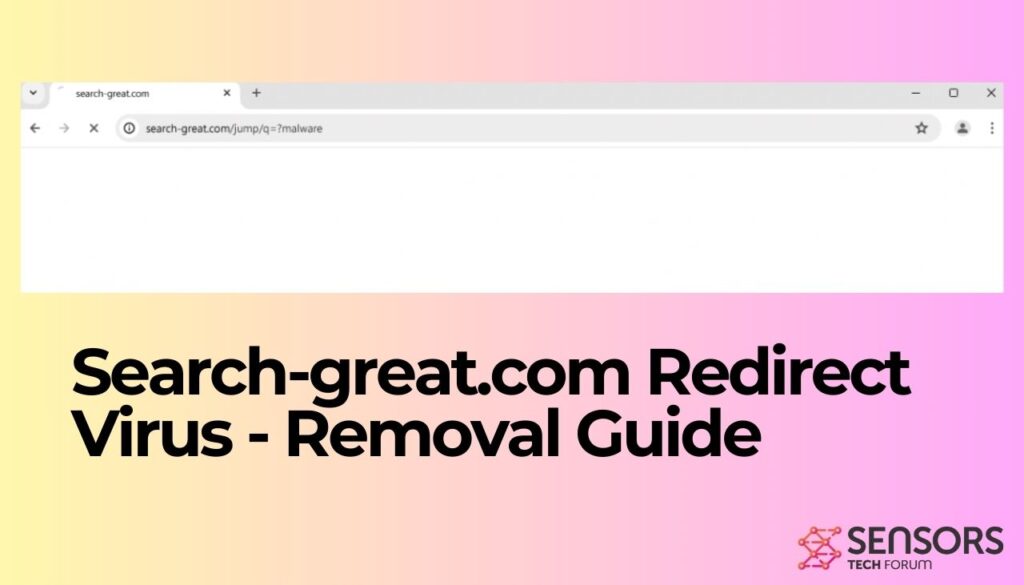
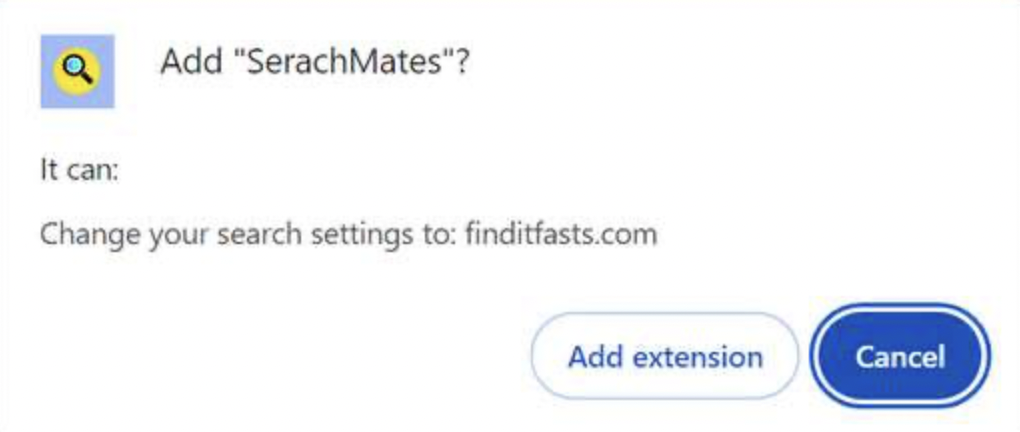
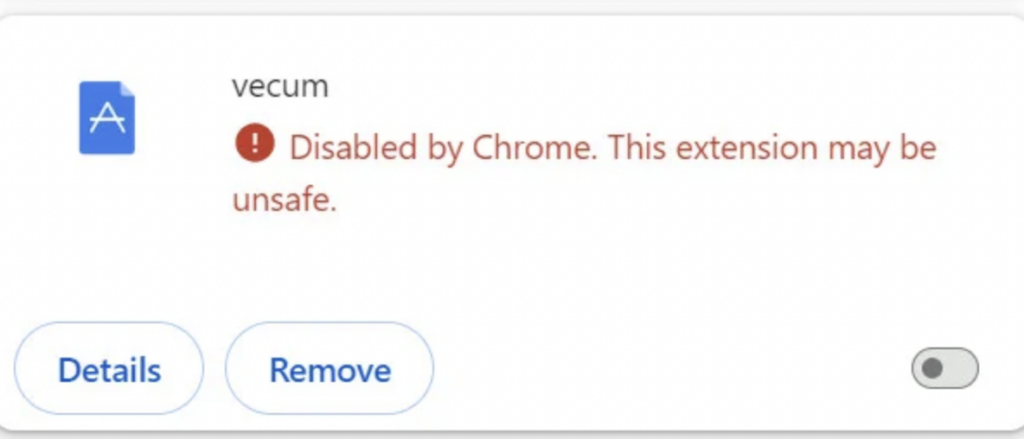
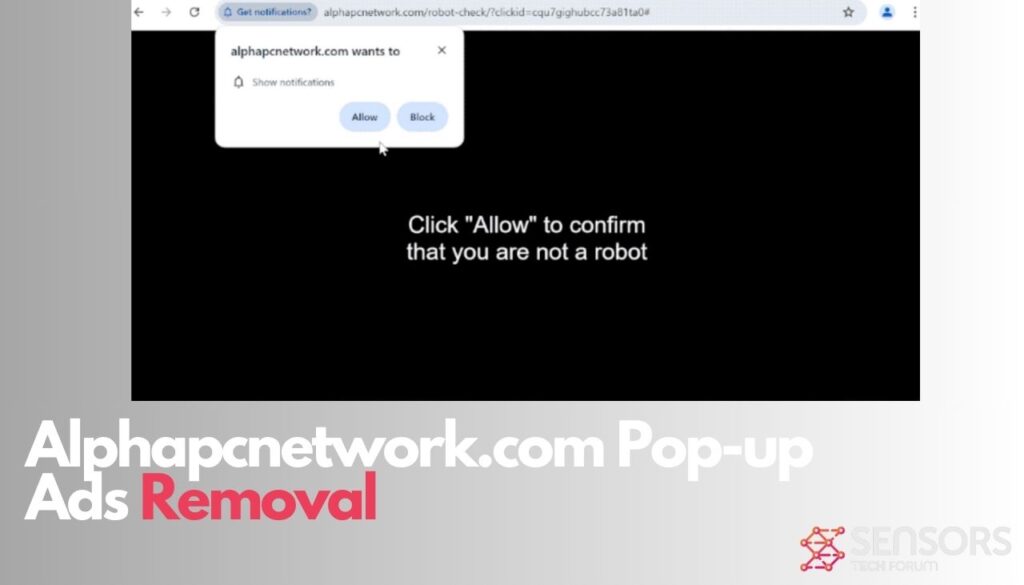
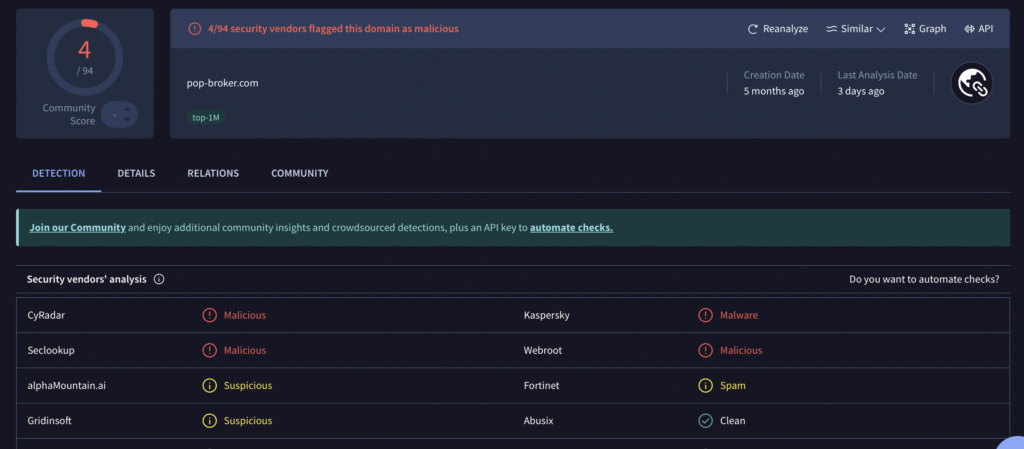
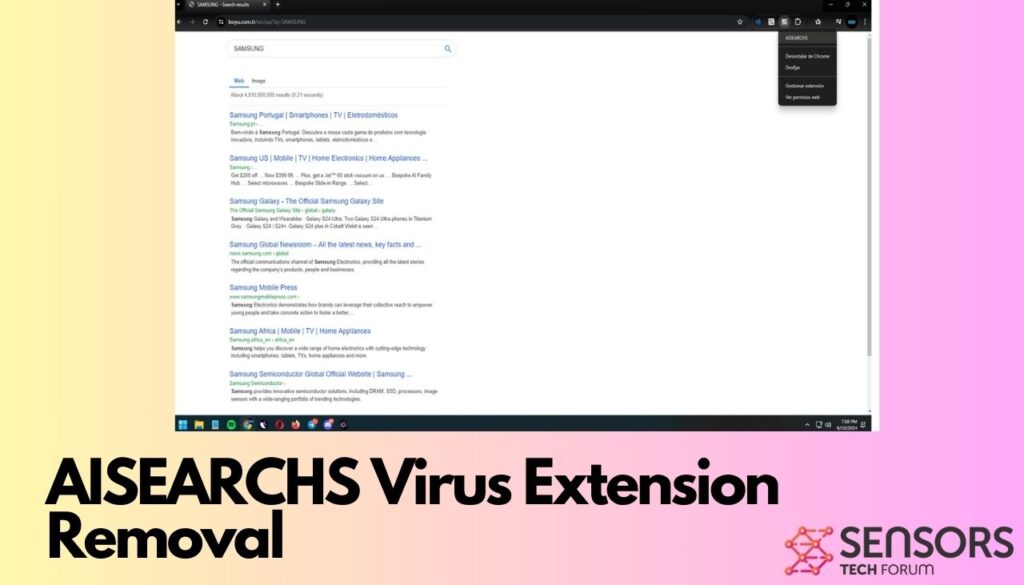
PUADlManager:Win32/Snackarcin – How to Remove
What Is PUADlManager:Win32/Snackarcin? PUADlManager:Win32/Snackarcin has been classified as a malicious potentially unwanted application (PUA) which can perform various activities on an infected machine. These include ad injection, redirects, data collection, spying on your activities, sharing collected data with a remote…


![Flowprotocol.co.in Pop-ups – How to Remove [Guide] Flowprotocol.co.in Pop-ups - How to Remove](https://cdn.sensorstechforum.com/wp-content/uploads/2024/09/Flowprotocol.co_.in-Pop-ups-How-to-Remove--1024x585.jpg)



![Tuckedmajor.com – Is It a Virus? [Removal Guide] Tuckedmajor.com - Is It a Virus](https://cdn.sensorstechforum.com/wp-content/uploads/2024/08/Tuckedmajor.com-Is-It-a-Virus-1024x585.jpg)
![Is Utweb.exe a Virus? [Fix Guide] Utweb.exe - What Is It & How to Remove](https://cdn.sensorstechforum.com/wp-content/uploads/2024/08/Utweb.exe-What-Is-It-How-to-Remove-1024x585.jpg)