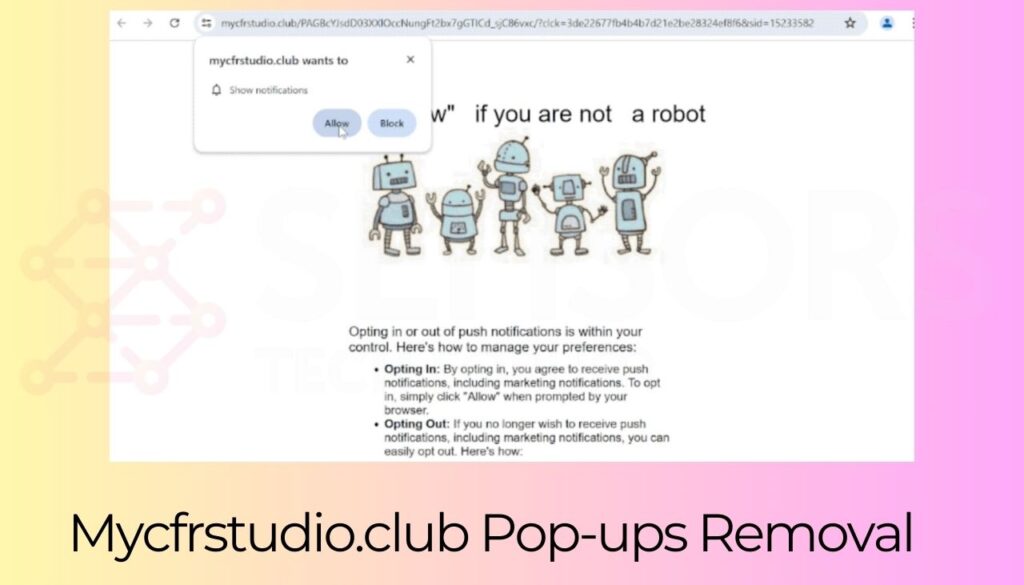
![Yandex.ru Redirect Virus Removal [Ultimate Guide] Yandex.ru Redirect Virus Removal](https://cdn.sensorstechforum.com/wp-content/uploads/2024/07/Yandex.ru-Redirect-Virus-Removal-1024x585.jpg)
Yandex.ru Redirect Virus Removal [Ultimate Guide]
Have you ever wondered about the powerhouse behind millions of internet searches in Russia? Meet Yandex.ru, far beyond a conventional search engine, this platform is a digital swiss army knife for its users, offering everything from email services to online…


![Removing Iadispatcher.com Redirect Virus [Fix Guide] Removing Iadispatcher.com Redirect Virus](https://cdn.sensorstechforum.com/wp-content/uploads/2024/07/Removing-Iadispatcher.com-Redirect-Virus-1024x242.png)

![Quick Switch Search Extension Virus Removal [Fix Guide] Quick Switch Search Virus Removal](https://cdn.sensorstechforum.com/wp-content/uploads/2024/07/Quick-Switch-Search-Virus-Removal-1024x585.jpg)
![CraxsRAT Android Malware Deciphered [Cybersecurity Guide] zyg0te.medium.com - EVLF threat actor](https://cdn.sensorstechforum.com/wp-content/uploads/2024/07/zyg0te.medium.com-EVLF-threat-actor-1024x641.png)
![WATZ Virus [.watz Files] Remove + Decrypt Guide [Solved] WATZ Files Virus](https://cdn.sensorstechforum.com/wp-content/uploads/2024/07/WATZ-Files-Virus-1024x576.jpg)
![TopNotch Search Redirect Removal [Fix] TopNotch Search](https://cdn.sensorstechforum.com/wp-content/uploads/2024/07/TopNotch-Search.jpg)
![Suguy.top Pop-ups Removal Guide [Solved] Suguy.top](https://cdn.sensorstechforum.com/wp-content/uploads/2024/07/Suguy.top_-1024x585.jpg)