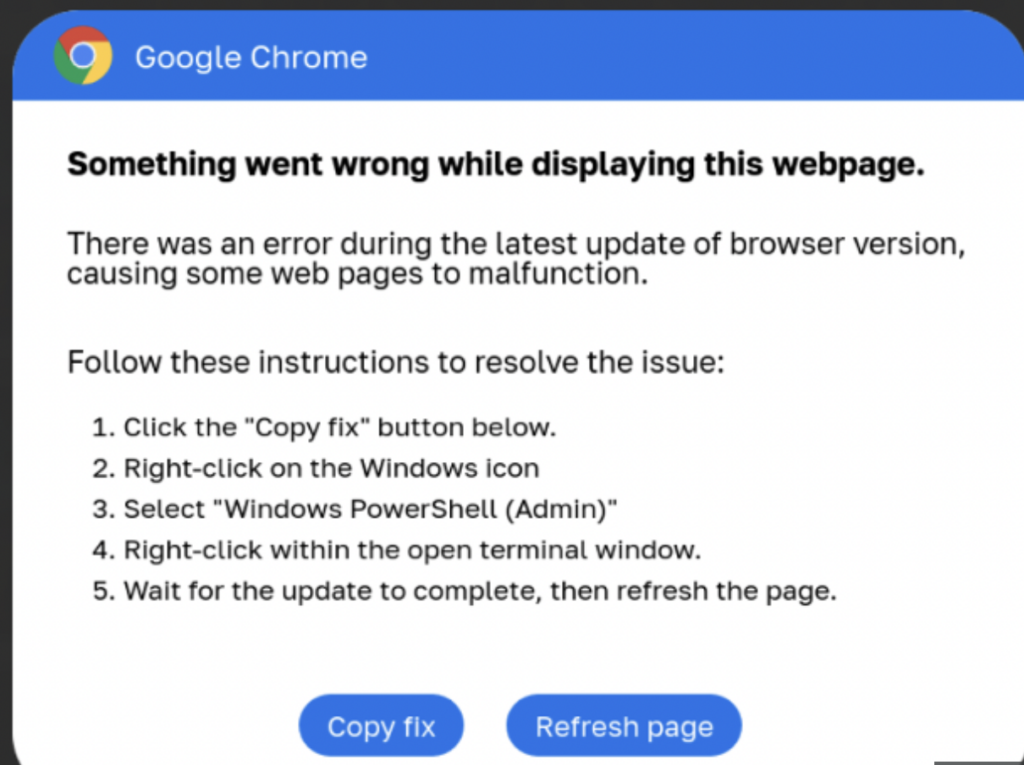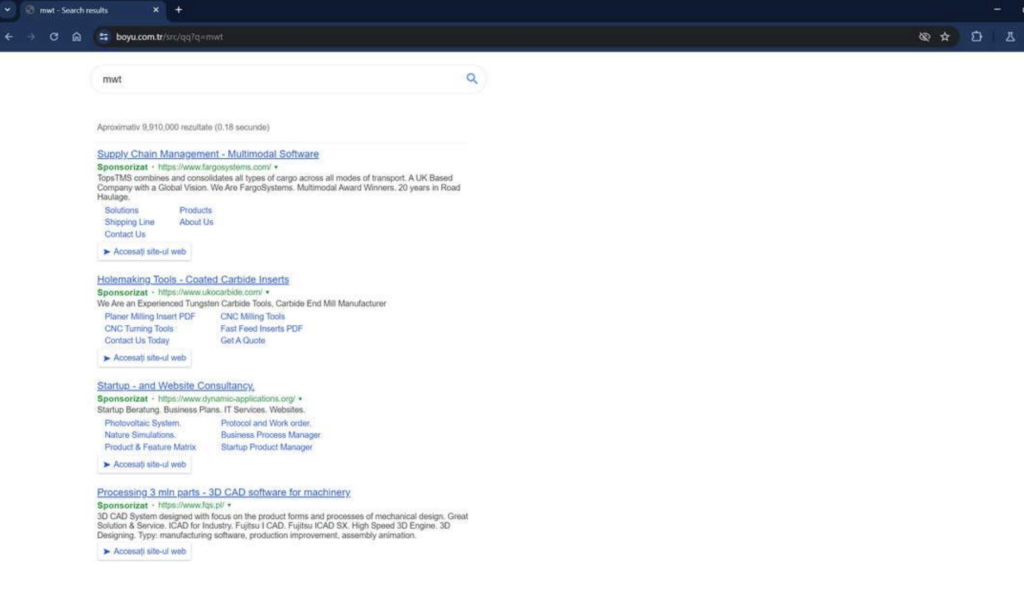
ISEEK Browser Extension Removal Steps
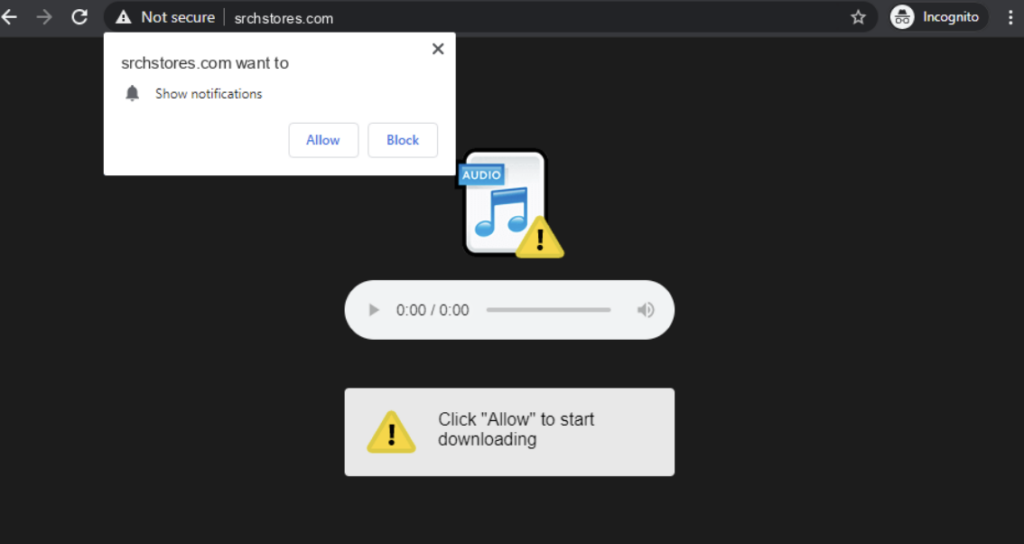
Are you struggling to remove a browser extension called ISEEK? Is your browser constantly redirecting you to findflarex.com and boyu.com? These symptoms are indications that a browser hijacker has sneaked into your browser. The article that follows will help you…




![What Is the NebulaNanoel Browser Extension? [Removal Steps] NebulaNanoel Browser Extension](https://cdn.sensorstechforum.com/wp-content/uploads/2024/07/NebulaNanoel-Browser-Extension-1024x585.jpg)
![“Instagram Password Hacker” Scam Explained [Protection Tips] Instagram Password Hacker Scam Explained](https://cdn.sensorstechforum.com/wp-content/uploads/2024/07/Instagram-Password-Hacker-Scam-Explained-1024x585.jpg)