Remove PARTYDOG Ransomware
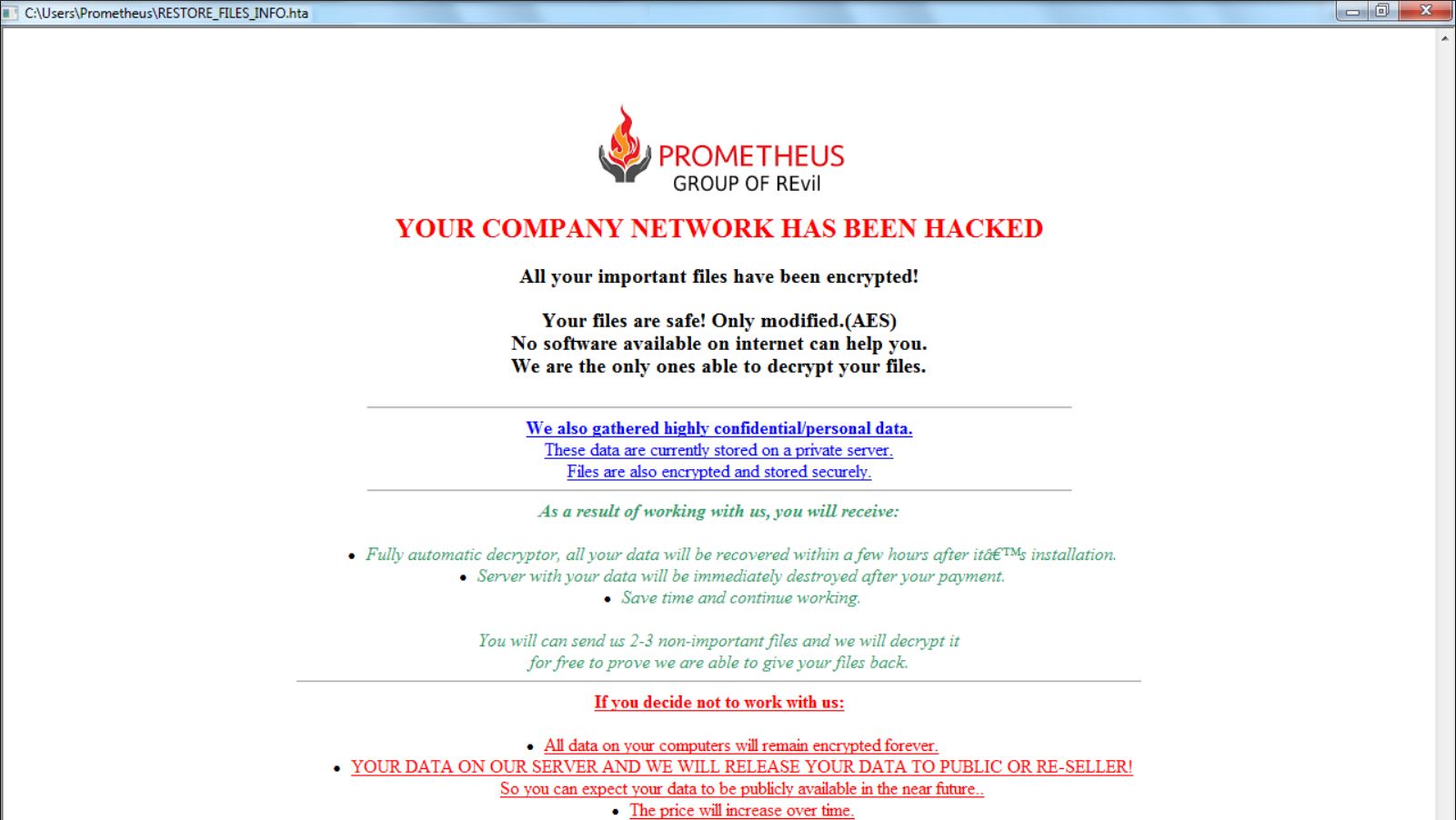
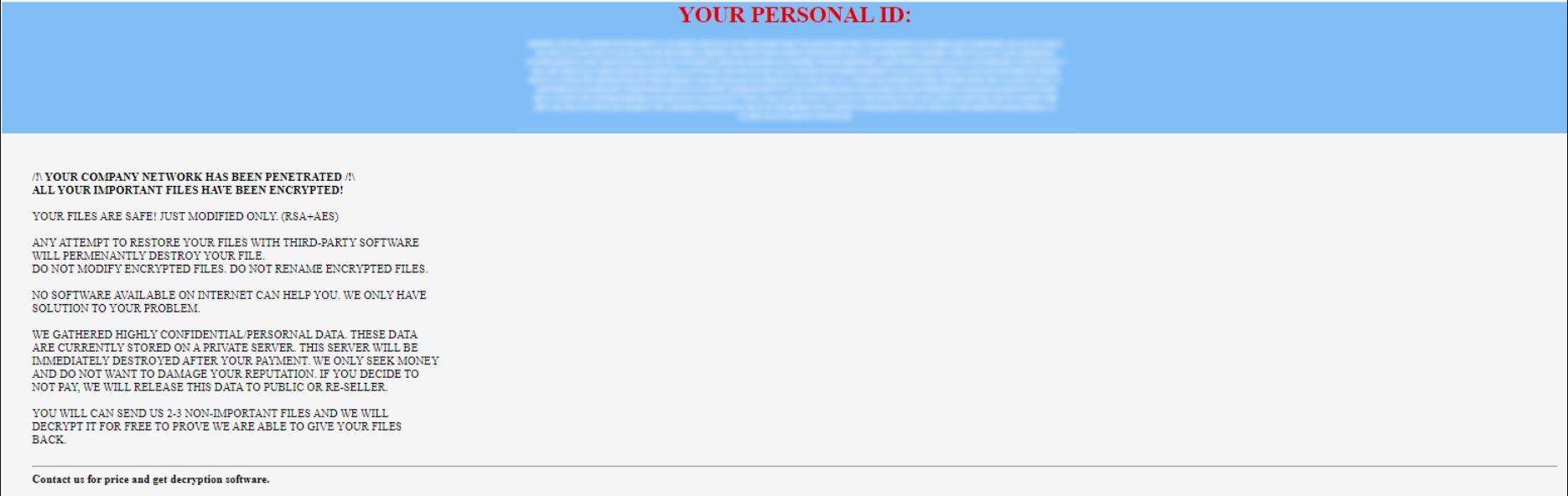
PARTYDOG Virus What does it mean to see the extension .PARTY appended to the names of all your valuable files? It means that your PC has been infected with ransomware called PARTYDOG. This ransomware encrypts personal files and then displays…


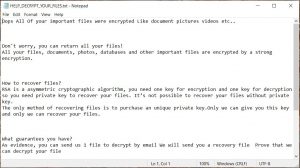











![Root Ransomware [.root Virus File] – How to Remove root virus ransom message](https://cdn.sensorstechforum.com/wp-content/uploads/2021/05/root-virus-ransom-message.png)