Remove Komprogo Trojan Horse Completely
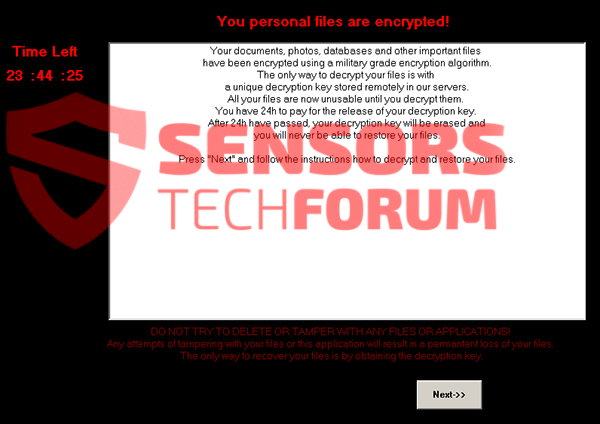
The Komprogo Trojan horse opens a backdoor on a compromised computer. It may download potentially malicious files, and may upload personal data to a few remote locations. It also modifies the Windows Registry. Komprogo Trojan Distribution Method There are a…