AKBuilder é o nome do mais recente kit de exploração atualmente vendido em mercados subterrâneos e anunciado em vídeos do YouTube, como revelado por SophosLabs. AKBuilder está sendo implantado ativamente junto com dois outros construtores de exploit populares - Microsoft Word Intruder e Ancalog Builder.
O AKBuilder, em particular, gera documentos Word maliciosos em Rich Text. Os invasores usam para empacotar amostras de malware em documentos com armadilhas eletrônicas. Esses documentos estão sendo distribuídos em campanhas ativas de spam por e-mail.
Semelhante ao Microsoft Word Intruder e Ancalog Builder, AKBuilder também usa exploits para corromper intencionalmente arquivos usados para acionar automaticamente bugs no Office. Contudo, falhas no Windows também são direcionadas.
relacionado: É Império Embale o Next Big Exploit Kit?
Como mencionado, o novo EX está sendo vendido e anunciado, seu preço está próximo $550. Atores maliciosos devem pagar em moedas como Bitcoin e Perfect Money.
Visão geral técnica do AKBuilder
De acordo com Gábor Szappanos, o pesquisador que analisou o kit de exploração, existem duas variações do AKBuilder. A versão anterior, chamado AK-1, aproveitou duas vulnerabilidades no mesmo documento CVE-2012-0158 e CVE-2014-1761. A versão posterior, chamado AK-2, aproveita uma falha: CVE-2015-1641. AK-1 e AK-2 são lançados como um script Python, onde tudo é codificado e nada é configurável, exceto os nomes dos arquivos.
AKBuilder está sendo comprado e usado por vários grupos de cibercrimes, e foi implantado para espalhar várias famílias de malware. Os pesquisadores dizem que o grupo mais ativo e menos cuidadoso usando o EK são os grupos BEC da Nigéria..
relacionado: Golpes BEC: Os e-mails que as empresas falidas
Os pesquisadores foram capazes de estimar que AK-1 foi mais ativo entre meados de 2015 e 2016. Assim que a segunda variante foi lançada, AK-1 diminuído, que foi no verão de 2016. Contudo, AK-1 foi mais uma vez revivido conforme os pesquisadores recentemente começaram a observar novos ataques envolvendo o EK. Quanto ao motivo - a lacuna de mercado que precisava de exploits mais antigos do Office fornecidos pelo AK-1 deve tê-lo ressuscitado. O código-fonte do AK-2 é baseado no script Python do construtor AK-1 e exibe as mesmas características.
Que tipo de malware é distribuído pelo AKBuilder?
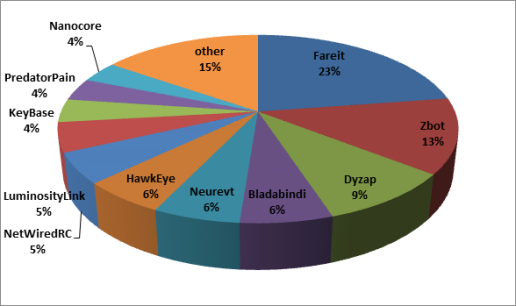
De acordo com SophosLabs, sobre 760 documentos maliciosos foram identificados, usado para distribuir sobre 50 diferentes famílias de malware, como cavalos de Troia bancários (Zbot, Chisburg, Fareit, Neurevt), o keylogger PredatorPain, e o backdoor NetWiredRC.
O gráfico abaixo mostra as famílias de malware distribuídas por AK-1 e AK-2:
Proteção contra AKBuilder Exploit Kit
Estar totalmente corrigido parece ser o elemento de segurança mais importante. AKBuilder usa exploits relativamente novos, como CVE-2014-1761 e CVE-2015-1641, mas felizmente não foi pego usando exploits de dia zero. Os pesquisadores dizem que, em ambos os casos, o uso da exploração ocorreu meses depois que a falha foi corrigida.
assim, mantenha todos os seus aplicativos atualizados e não se esqueça da importância de um poderoso programa anti-malware.
digitalizador Spy Hunter só irá detectar a ameaça. Se você quiser a ameaça de ser removido automaticamente, você precisa comprar a versão completa da ferramenta anti-malware.Saiba Mais Sobre SpyHunter Anti-Malware Ferramenta / Como desinstalar o SpyHunter