AKBuilder is the name of the latest exploit kit currently being sold in underground markets and advertised in YouTube videos, as revealed by SophosLabs. AKBuilder is actively being deployed alongside two other popular exploit builders – Microsoft Word Intruder and Ancalog Builder.
AKBuilder particularly generates malicious Word documents in Rich Text. Attackers use it to package malware samples into booby-trapped documents. These documents are being distributed in active email spam campaigns.
Similarly to Microsoft Word Intruder and Ancalog Builder, AKBuilder also uses exploits to intentionally corrupt files used to automatically trigger bugs in Office. However, flaws in Windows are also targeted.
Related: Is Empire Pack the Next Big Exploit Kit?
As mentioned, the new EX is currently being sold and advertised, its price being around $550. Malicious actors should pay in currencies such as Bitcoin and Perfect Money.
AKBuilder Technical Overview
According to Gábor Szappanos, the researcher who looked into the exploit kit, there are two variations of AKBuilder. The earlier version, named AK-1, leveraged two vulnerabilities in the same document CVE-2012-0158 and CVE-2014-1761. The later version, named AK-2, leverages one flaw: CVE-2015-1641. AK-1 and AK-2 are both released as a Python script, where everything is hardcoded and nothing is configurable except the file names.
AKBuilder is being bought and used by various cybercrime groups, and has been deployed to spread various malware families. Researchers say that the most active and least careful group using the EK are Nigerian BEC groups.
Related: BEC Scams: Emails That Bankrupt Businesses
Researchers were able to estimate that AK-1 was most active between mid-2015 and 2016. Once the second variant was released, AK-1 diminished, which was by the summer of 2016. However, AK-1 has once more been revived as researchers recently started to observe new attacks involving the EK. As to why – the market gap that was in need of older Office exploits provided by AK-1 must have resurrected it. AK-2’s source code is based on the AK-1 builder Python script and displays the same characteristics.
What Kind of Malware Is Distributed by AKBuilder?
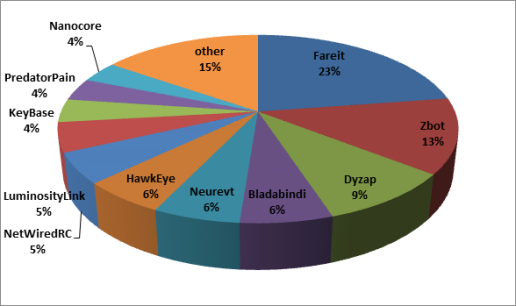
According to SophosLabs, about 760 malicious documents were identified, used to distribute over 50 different malware families, such as banking Trojans (Zbot, Chisburg, Fareit, Neurevt), the PredatorPain keylogger, and the NetWiredRC backdoor.
The chart below shows the malware families distributed by both AK-1 and AK-2:
Protection against AKBuilder Exploit Kit
Being fully patched appears to be the most important safety element. AKBuilder uses relatively new exploits such as CVE-2014-1761 and CVE-2015-1641, but luckily hasn’t been caught using zero-day exploits. Researchers say that in both cases the use of the exploit took place months after the flaw was patched.
So, keep all of your applications updated and don’t forget the important of a powerful anti-malware program.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter