Researchers have demonstrated how a little gadget called Zigbee Sniffer could be used to hack smartphones, like Xiaomi Mi. The attack has been conducted via exploiting the same ports of the several sensors, which are a part of the “SmartHome” sensors of the device. This hack is yet another interesting development in smartphone and the IoT sector, suggesting that there are many researchers focused on improving it by demonstrating such hacks. This hack resulted in the network sniffing of the ZigBee wireless language used specifically for IoT devices. The white hat hacker may want to show with this that Xiaomi Mi phones could be turned into a network sniffer of those IoT devices of a given home as a consequence of modifying their firmware.
Researchers have demonstrated how a little gadget called Zigbee Sniffer could be used to hack smartphones, like Xiaomi Mi. The attack has been conducted via exploiting the same ports of the several sensors, which are a part of the “SmartHome” sensors of the device. This hack is yet another interesting development in smartphone and the IoT sector, suggesting that there are many researchers focused on improving it by demonstrating such hacks. This hack resulted in the network sniffing of the ZigBee wireless language used specifically for IoT devices. The white hat hacker may want to show with this that Xiaomi Mi phones could be turned into a network sniffer of those IoT devices of a given home as a consequence of modifying their firmware.
What Is Needed for The Hack?
An independent researcher at the faire-ca-soi-meme.fr has posted the whole information in which he claims he succeeded using three cheap sensors:
- A humidity and temperature sensor.
- A motion sensor.
- Sensor for opening a door.
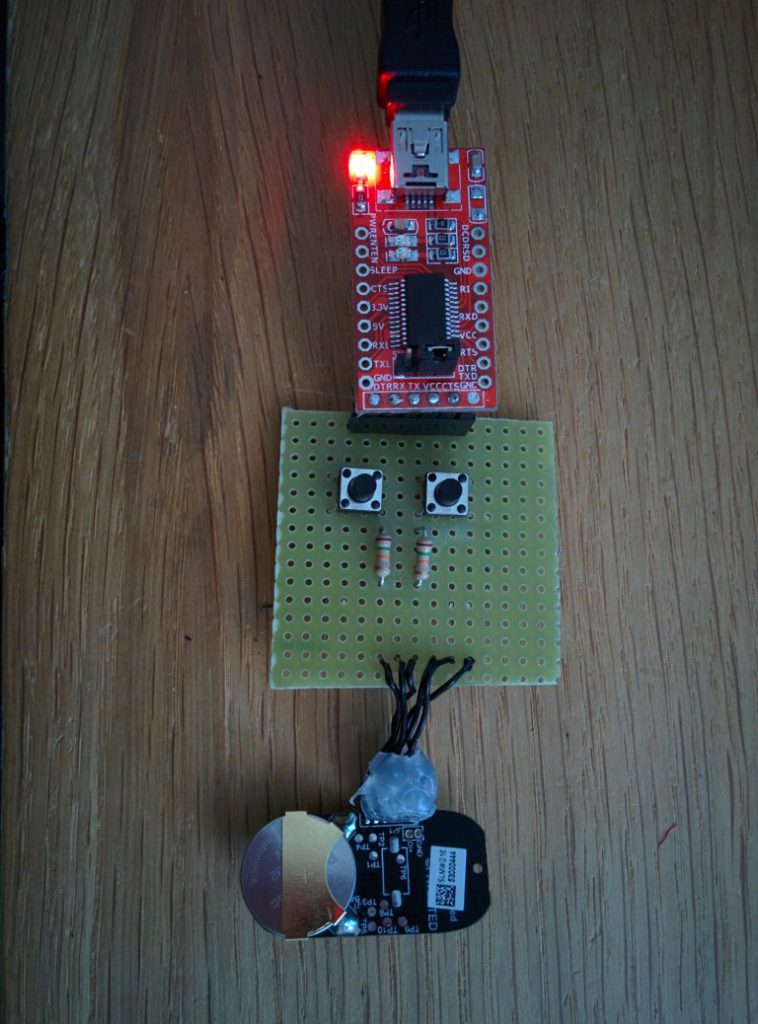
The hacker then connected Xiaomi programming card with the door opening sensor using connectors from Xiaomi and both of these devices were connected to a so called USB to TTL FTDI converter. The end result looks like the image below:
The Hacking Explained
For the hack to work, the programmer used a software, called BeyondStudio for NXP and SDK. Via this, it was possible to flash the Xiaomi sensor for temperature and humidity. After flashing it, the software can literally become a Zigbee Sniffer.
Despite some issues during installation, the programmer reports that he managed to modify the sensor to Sniff information out. Then, to analyze the sniffed traffic and link the hacked firmware, installed in the sensor, the researcher used Zigbee sniffer software which is compatible with it.
To read the packets, the researcher says that Wireshark is completely free and can successfully read everything, but there is also a protocol analyzer software that can be used, called Ubique Protocol Analyzer.
Then the researchers performed the following activities:
- Started the sniffing hardware.
- Installed the SmartHome software gateway.
- Paired the sensor for door opening.
- Paired the motion detector hardware.
In the end, via the Zigbee protocol, the sensors were able to communicate and sniff out information from the device and even decrypt it.
It can extract different data, like commands, queries and other information. Besides this information, the hacker could also extract data from the sensors themselves, but the data there was in an encrypted format. The hacker is convinced that with the right firmware and sensors he can take advantage of other devices, such as the Raspberry Pi. It may also be possible with the right software to develop and manipulate every other sensors.
Images Source: https://faire-ca-soi-meme.fr