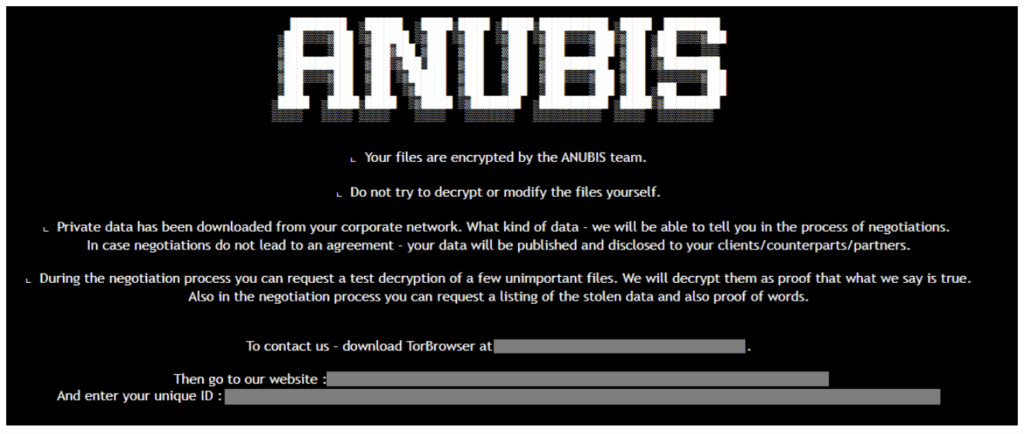
July 2025 Patch Tuesday: 130 Vulnerabilities Addressed
Microsoft’s latest Patch Tuesday release of fixes for 130 vulnerabilities did not include any updates for zero-day flaws that are currently being exploited. Still, the company acknowledged that one of the patched issues had already been made public before the…



![Runetki5.com – Is It Safe? [Virus Check] Runetki5.com](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Runetki5.com_-1024x799.png)
![12jav.net – Is It Safe? [Scam and Security Check] 12jav.net](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/12jav.net--1024x248.png)
![Xasiat.com – Is it Safe? [Scam and Virus Check] Xasiat.com](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Xasiat.com_-1024x201.png)
![Api.tigerai.app – Is It Safe? [Security Check] Api.tigerai.app - Is It Safe? [Security Check].exe](https://cdn.sensorstechforum.com/wp-content/uploads/2025/07/Api.tigerai.app-Is-It-Safe-Security-Check.exe_-1024x585.jpg)
![Xhamsterlive.com – Is It Safe? [Scam and Virus Check] Xhamsterlive.com](https://cdn.sensorstechforum.com/wp-content/uploads/2025/06/Xhamsterlive.com_-1024x668.png)

![MrMan.com – Is It Safe? [Scam Check] MrMan.com- is it safe?](https://cdn.sensorstechforum.com/wp-content/uploads/2025/06/MrMan.com-is-it-safe-1024x585.png)