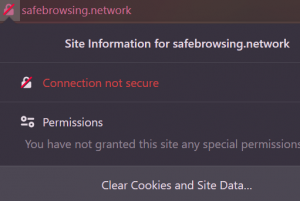
Safebrowsing.network Mac – How to Remove
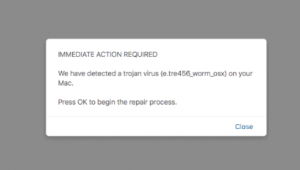
What is Safebrowsing.network? Exactly how does specifically Safebrowsing.network operate? How to get rid of Safebrowsing.network completely from your Mac? Exactly how to stop redirects from Safebrowsing.network? The Safebrowsing.network website comes from a possibly undesirable application, additionally referred to as PUA…


![Discovery Engine Virus on Mac – How to Remove It [Free Instructions]](https://cdn.sensorstechforum.com/wp-content/uploads/2019/11/discovery-engine-mac-virus-how-to-remove-restore-data-sensorstechforum-com-300x255.jpg)