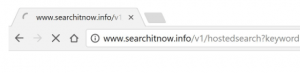
Searchit Mac Virus – How to Remove It
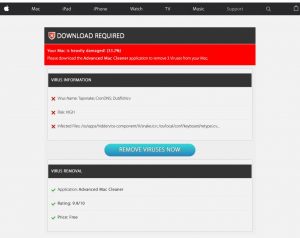
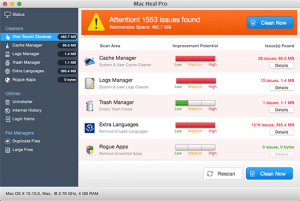
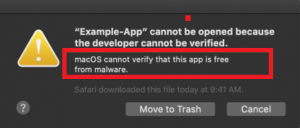
What is the Searchit virus? How to remove Searchit virus? How to remove Searchit virus from your Mac? Searchit virus is the name of a browser hijacking app that Is added on Macs and its primary purpose is to display…