Are you familiar with the shadowy threat of STOP/DJVU ransomware, a cybersecurity nightmare that has haunted users since 2018? This malicious software not only locks away your cherished photos, documents, and videos with an encryption key but also demands a ransom for their return, presenting a complex challenge for victims and cybersecurity experts alike. With its roots deeply entrenched in deceptive downloads and constantly evolving to outsmart detection efforts, STOP/DJVU ransomware symbolizes a significant and persistent danger in our interconnected world.
This article delves into the inner workings of STOP/DJVU ransomware, from its cunning infiltration methods to effective strategies for prevention, removal, and recovery, equipping you with the knowledge to safeguard your digital domain against this formidable foe.
STOP/DJVU Ransomware Summary
| Name | STOP/DJVU Ransomware |
| Type | Ransomware, Cryptovirus |
| Short Description | Files get encrypted on your computer machine and demands a ransom to be paid to allegedly recover them. |
| Symptoms | The malicious program will encrypt your files with the help of the AES and RSA encryption algorithms. All locked files will have a new extension appended to them. |
| Distribution Method | Spam Emails, Email Attachments |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
| Data Recovery Tool | Windows Data Recovery by Stellar Phoenix Notice! This product scans your drive sectors to recover lost files and it may not recover 100% of the encrypted files, but only few of them, depending on the situation and whether or not you have reformatted your drive. |
What Is STOP/DJVU Ransomware?
STOP/DJVU ransomware represents a sophisticated form of malware that infiltrates systems to encrypt files, essentially holding them hostage. Discovered initially in 2018, this ransomware variety encrypts users’ files, including photos, documents, and videos, by adding one of its many unique file extensions such as .djvu, .lkfr, .lkhy, .moia, or .fatp. Upon successful encryption, it demands ransom in exchange for decryption keys, trapping users in a dire predicament. This ransomware typically spreads through deceptive downloads, such as software cracks and pirated content, leveraging the allure of free access to entice unsuspecting users.
The primary intention behind STOP/DJVU ransomware is to force victims to pay a ransom to regain access to their files. However, paying the ransom offers no guarantee that the encrypted files will be restored. This malicious software uses public key cryptography, a secure encryption method that makes unauthorized decryption incredibly challenging without the corresponding private key, held only by the attackers.
The History and Evolution of STOP/DJVU Ransomware
Since making its debut in 2018, STOP/DJVU ransomware has evolved significantly, becoming one of the most prolific ransomware families targeting individuals across the globe. Its adaptability is evident through the release of numerous variants, each designed to exploit different vulnerabilities and evade detection by security software.
The evolution of STOP/DJVU ransomware is marked by its developers’ continuous efforts to refine its mechanisms for delivery and encryption. Unlike early versions that may have relied on simpler methods of infection, recent iterations employ more sophisticated tactics, such as exploiting software vulnerabilities and using elaborate phishing campaigns. This adaptability ensures its continued prevalence and effectiveness in compromising systems.
Furthermore, the STOP/DJVU family’s persistence is demonstrated by its developers’ responses to cybersecurity measures. As security researchers and software providers work towards neutralizing threats by developing decryption tools, the creators of STOP/DJVU ransomware counteract by releasing new, altered versions of the malware. This ongoing cat-and-mouse game makes STOP/DJVU a continuously relevant and dangerous threat in today’s digital environment.
Individuals and organizations alike must adopt comprehensive cybersecurity measures to mitigate the risk posed by STOP/DJVU ransomware. Investing in reputable security software, like SpyHunter, can offer crucial protection against such ransomware attacks. SpyHunter’s advanced security features are designed to detect and remove ransomware infections, providing users with peace of mind and significantly reducing the risk of falling victim to these malicious threats.
Adopting cautious online behaviors, such as avoiding downloading software from unverified sources and maintaining updated backups of important files, can also play a significant role in safeguarding against ransomware attacks. It’s essential to stay informed about the latest cybersecurity threats and to implement proactive measures to protect valuable data from ransomware like STOP/DJVU.
How STOP/DJVU Ransomware Infects Your System
Understanding how STOP/DJVU ransomware infiltrates computers is crucial for prevention and prompt response. This ransomware variant uses several strategies to bypass security measures and encrypt users’ files, making awareness and caution important defense measures.
Common Methods of Infection Employed by STOP/DJVU
STOP/DJVU ransomware employs various tactics to gain unauthorized access to systems:
- Freeware Programs: This ransomware often piggybacks on freeware programs downloaded from questionable sources, including torrent sites. Bundled software packages may contain hidden malware waiting to spring into action once installed.
- Fake Executable Files: Users downloading application extensions (.exe files) from unreliable sources may inadvertently initiate the ransomware. These fake executables often masquerade as legitimate software or updates.
- Malicious Scripts: Visiting compromised websites can trigger malicious scripts that download ransomware onto your computer. These scripts may activate when clicking on deceptive ads or alerts.
- Unsafe Networks: Networks lacking proper security can become conduits for distributing ransomware, especially when downloading or sharing files on such networks.
- Email Phishing: Fraudulent emails that mimic reputable entities can trick users into opening attachments or clicking links that deploy the ransomware onto their systems.
- Exploiting Software Vulnerabilities: Outdated or unpatched software presents opportunities for STOP/DJVU ransomware to exploit known flaws and infiltrate systems.
Staying vigilant and adopting safe browsing and download habits are vital in preventing ransomware infection.
Signs That Your Device Might Be Infected With STOP/DJVU
Recognizing the signs of a STOP/DJVU infection can help mitigate its impact:
- File Extension Changes: An immediate clue is the appearance of unfamiliar extensions, such as .djvu, appended to your files, indicating encryption.
- Ransom Notes: Finding a readme.txt file or similar ransom note on your desktop or within folders is a clear signal of ransomware activity.
- Inability to Open Files: If you’re unable to open files or they appear jumbled, it likely means they’ve been encrypted.
- System Performance Deterioration: Ransomware can significantly slow down your computer as it encrypts files or operates in the background.
Encountering these signs necessitates prompt action. Safeguarding against further damage means disconnecting from the internet and considering professional advice before making any ransom payments. For comprehensive protection and removal of such threats, employing a dedicated security solution like SpyHunter can provide real-time defense and minimize the risks associated with ransomware infections.
Step-by-Step Guide to Safely Remove STOP/DJVU Ransomware
Confronting the STOP/DJVU ransomware demands a calculated approach to ensure the safety of your data and the integrity of your computer system. This guide walks you through a strategic, step-by-step process to mitigate the threat of this pervasive ransomware.
Isolating the Infected Machine: A Crucial First Step
Before diving into the removal process, it’s critical to isolate the infected machine. This means disconnecting from the internet, turning off shared networks, and ceasing all data transfers. By doing so, you prevent the ransomware from spreading to other devices and protect your network integrity. Here are simple, practical steps:
- Disconnect your device from the internet, either by turning off the Wi-Fi connection or unplugging the Ethernet cable.
- Switch off Bluetooth and any other connection-based services to prevent the spread.
- Alert your network administrator or security team, if applicable, to ensure broader system safety.
These preemptive actions help contain the threat and create a secure environment for malware removal.
Utilize SpyHunter to Automatically Remove STOP/DJVU Ransomware
After isolating the affected machine, the next step is to tackle the ransomware directly. Using an advanced malware removal tool like SpyHunter streamlines this process.
The Benefits of Using SpyHunter for Ransomware Removal
SpyHunter is a powerful software designed to identify, isolate, and eliminate malware, including the notorious STOP/DJVU ransomware. It’s crafted for users of all technical backgrounds, offering a straightforward, effective approach to malware removal. Here are the key advantages:
- Advanced Detection Capabilities: SpyHunter employs sophisticated algorithms to detect both known and emerging malware threats.
- User-friendly Interface: Its intuitive design simplifies the virus removal process, making it accessible for all users.
- Automated Removal: Once malware is detected, SpyHunter efficiently removes these threats with minimal user intervention, reducing the risk of human error.
- Regular Updates: Frequent updates ensure SpyHunter stays ahead of the latest cybersecurity threats, providing ongoing protection for your device.
To use SpyHunter for ransomware removal:
- Download and install SpyHunter according to the provided instructions.
- Run a scan to identify malicious software on your device.
- Follow the prompts to remove any detected malware, effectively ridding your device of STOP/DJVU ransomware.
This approach not only eliminates the immediate threat but also fortifies your device against future infections, offering peace of mind in an ever-evolving digital environment.
Decrypt Your Files: Combating STOP/DJVU Ransomware
Falling victim to the STOP/DJVU ransomware can be a stressful experience, with personal or important files suddenly out of reach due to encryption. Fortunately, the fight against this form of cyberattack is not hopeless. Understanding the tools and methods available for decryption can play a pivotal role in recovering your data. This guide aims to simplify the decryption process, providing a beacon of hope for those affected.
Identifying Whether Your Files Were Encrypted With Online or Offline Keys
The first step towards decrypting your files is identifying the type of key used to encrypt them. STOP/DJVU ransomware variants use either online or offline keys. Determining which one was used is crucial as it significantly impacts your approach to recovery. Offline keys are reused across multiple victims, making decryption more straightforward once a key is recovered by cybersecurity experts. In contrast, online keys are unique to each victim, complicating the decryption process due to the specificity of the encryption.
To ascertain the type of encryption used on your files, examine the ransom note left by the attackers or use decryption tools provided by reputable cybersecurity firms, which often automatically identify the encryption type.
Exploring Available Decryption Tools for STOP/DJVU Files
Several tools have been developed to assist victims of STOP/DJVU ransomware in decrypting their files. The availability and effectiveness of these tools can vary based on the encryption key type used during the attack. Here’s how to proceed with the most commonly recommended decryption solutions:
- EmsiSoft Decryptor for STOP Djvu: This is a widely recommended tool for victims whose files were encrypted with offline keys. It’s straightforward to use:
- Download the EmsiSoft Decryptor for STOP Djvu from the official website.
- Run the program and follow the on-screen prompts to start the decryption process.
- If your data was encrypted with an offline key, the tool might successfully restore your files.
- Online Key Decryption: If your files were encrypted with an online key, the process becomes trickier. Since each key is unique, recovering your files without the specific key is challenging. Regularly checking for updates on decryption tools and community forums is advised, as new keys or methods might emerge.
- Checking for New Decryptors: Regularly visit reputable sources such as the ID Ransomware website or the EmsiSoft decryption tool page for updates on new decryption solutions that have been developed.
When dealing with encryption by an online key, maintaining hope and staying informed are crucial. Although immediate decryption might not be possible, the cybersecurity community’s continuous efforts often lead to breakthroughs that could facilitate the recovery of your files in the future.
In instances where decryption isn’t immediately feasible with the tools available, practicing good digital hygiene by backing up your data regularly and using security software like SpyHunter can provide a proactive defense against future ransomware attacks and simplify recovery should you become a victim.
Can STOP/DJVU Be Decrypted? [Available Decrypter]
In short, it can be, depending on the version of the ransomware.
There is a decrypter tool released for DJVU which requires .NET Framework 4.5.2 installed or a later version. The tool was initially released for the .puma, .pumax, .pumas versions of the cryptovirus. Michael Gillespie reguralrly updates it to support newly discovered verions like .format, .access, .ndarod, .bopador, .novasof, .dodoc, .todar and other. Keep in mind that the tool requires a pair of an original file and its encrypted version.
STOP/DJVU Versions That Can Be Decrypted
As explained by the decrypter’s developer, for all versions of STOP Djvu, files can be successfully decrypted if they were encrypted with an offline key that we have.
For older Djvu variants, files can also be decrypted using encrypted/original file pairs submitted to the STOP Djvu Submission portal. This method, however, is not applicable to New Djvu files encrypted after August 2019.
The EmsiSoft decrypter is able to decrypt 148 variants of the ransom-demanding software out of 202+ available. The following extensions are supported by the decryption tool:
→ .gero, .hese, .seto, .peta, .moka, .meds, .kvag, .domn, .karl, .nesa, .noos, .kuub, .reco, .bora, .nols, .werd, .coot, .derp, .meka, .mosk, .peet, .mbed, .kodg, .zobm, .msop, .hets, .mkos, .nbes, .reha, .topi, .repp, .alka, .shadow, .djvu, .djvur, .djvuu, .udjvu, .uudjvu, .djvuq, .djvus, .djvur, .djvut, .pdff, .tro, .tfude, .tfudet, .tfudeq, .rumba, .adobe, .adobee, .blower, .promos, .promoz, .promorad, .promock, .promok, .promorad2, .kroput, .kroput1, .pulsar1, .kropun1, .charck, .klope, .kropun, .charcl, .doples, .luces, .luceq, .chech, .proden, .drume, .tronas, .trosak, .grovas, .grovat, .roland, .refols, .raldug, .etols, .guvara, .browec, .norvas, .moresa, .vorasto, .hrosas, .kiratos, .todarius, .hofos, .roldat, .dutan, .sarut, .fedasot, .berost, .forasom, .fordan, .codnat, .codnat1, .bufas, .dotmap, .radman, .ferosas, .rectot, .skymap, .mogera, .rezuc, .stone, .redmat, .lanset, .davda, .poret, .pidom, .pidon, .heroset, .boston, .muslat, .gerosan, .vesad, .horon, .neras, .truke, .dalle, .lotep, .nusar, .litar, .besub, .cezor, .lokas, .godes, .budak, .vusad, .herad, .berosuce, .gehad, .gusau, .madek, .darus, .tocue, .lapoi, .todar, .dodoc, .bopador, .novasof, .ntuseg, .ndarod, .access, .format, .nelasod, .mogranos, .cosakos, .nvetud, .lotej, .kovasoh, .prandel, .zatrov, .masok, .brusaf, .londec, .krusop, .mtogas, .nasoh, .nacro, .pedro, .nuksus, .vesrato, .masodas, .cetori, .stare, .carote, .gero, .hese, .seto, .peta, .moka, .kvag, .karl, .nesa, .noos, .kuub, .reco, .bora
If you see your variant among the ones above, it should be 100% decryptable now.
Prevention Is Better Than Cure: How to Guard Against Ransomware Attacks
With the digital age comes the increased risk of ransomware attacks, where your precious data is encrypted and held for ransom. The good news is, with proactive measures, you can significantly minimize the risk of a breach. In this discussion, we’ll explore key strategies to safeguard your digital atmosphere effectively.
Effective Strategies to Backup Your Data Regularly
Regular data backups are your safety net in the event of a ransomware attack. Here are some user-friendly methods to ensure your data remains secure:
- External Storage Devices: Utilize external hard drives or USB drives to back up your files. Disconnect and store these in a safe place once the backup is complete to prevent them from being targeted in an attack.
- Cloud Services: Cloud storage is a convenient way to ensure your files are accessible even if your local devices are compromised. Services like Microsoft OneDrive allow for seamless backup and sync across devices, ensuring that your data is not only backed up but also up to date across all devices.
- Partition Your Drive: By keeping your operating system and personal files on separate drive partitions, you can protect your data even if you need to wipe your OS partition clean. This method adds an additional layer of data security.
By implementing these backup strategies, recovering from a ransomware attack becomes a manageable process rather than a catastrophic loss of data.
The Importance of Keeping Your Software Updated
Outdated software is a prime target for ransomware attacks due to security vulnerabilities that haven’t been patched. Follow these simple yet effective steps to enhance your digital security:
- Activate Automatic Updates: This ensures that software, especially your operating system and security solutions, are always up to date with the latest security patches.
- Regular Software Audits: Regularly review and update all software applications to mitigate potential entry points for ransomware.
Maintaining software updates is a straightforward yet crucial precaution against ransomware infiltration, shielding your digital environment from known vulnerabilities.
Why Investing in Comprehensive Security Solutions Like SpyHunter is Essential
In the fight against increasingly sophisticated ransomware threats, comprehensive security solutions stand as your vigilant guardians. SpyHunter, with its robust anti-malware capabilities, offers pivotal benefits:
- Proactive Protection: SpyHunter’s dynamic scanning engine is designed to detect and thwart ransomware attacks before they can encrypt your files, providing real-time protection that adapts to evolving threats.
- Comprehensive Threat Detection: Utilizing advanced algorithms, SpyHunter identifies and neutralizes a wide array of digital threats, ensuring comprehensive security for your system.
- Peace of Mind: With SpyHunter’s protective measures in place, you can navigate the digital world with confidence, knowing your system is shielded against various cybersecurity threats.
Investing in an all-encompassing security solution like SpyHunter not only enhances your defense against ransomware but also fortifies your digital privacy and integrity against a spectrum of cyber threats. Embrace SpyHunter for a bolstered security posture that keeps your digital life secure.
Understanding Ransomware: A Closer Look at STOP/DJVU’s Mechanics
Ransomware, in its most basic form, is a type of malicious software designed to block access to a computer system until a sum of money is paid. STOP/DJVU ransomware, however, takes this manipulation to another level by employing advanced encryption methods to lock files individually – making it particularly challenging to reverse the damage without the unique decryption key. This variant primarily targets Windows users, exploiting vulnerabilities or user negligence like downloading pirated software or clicking on deceptive links.
The process begins when the ransomware infiltrates a system, usually masked as a legitimate download. Upon execution, it scans for specific file types – such as documents, images, and multimedia files – and encrypts them using sophisticated public key cryptography. This means it uses a public key to encrypt the files and demands the victim to purchase a private key for decryption. To maintain a semblance of usability, STOP/DJVU only encrypts the first 5MB of the data, ensuring the user can still operate the system and, more importantly, access the internet to pay the ransom.
What Makes STOP/DJVU Different From Other Ransomware Variants?
What sets STOP/DJVU apart from other ransomware families is its sheer volume of variants and its aggressive rate of evolution. With names like .djvu, .lkfr, .lkhy, among others, each variant applies a unique file extension to encrypted files, making them easily identifiable but difficult to unlock without the corresponding decryption key. This constant evolution helps the ransomware avoid detection by security software, as new versions can initially fly under the radar of antivirus programs’ databases.
Moreover, the STOP/DJVU ransomware family demonstrates a preference for exploiting less discerning internet users who may engage in downloading pirated content or software cracks. This targeting strategy not only broadens its pool of potential victims but also exploits a niche that is less likely to seek official help due to the questionable legality of their activities.
The Psychological Tactics Employed by Cybercriminals Behind Ransomware
The cybercriminals behind STOP/DJVU ransomware exploit psychological tactics to pressure victims into paying the ransom. Upon encrypting the targeted files, the ransomware leaves a note that usually demands payment in cryptocurrency, promising a decryption key in return. This note often emphasizes a time-limited offer, where the ransom amount would double after a certain period, creating a sense of urgency.
By naming the encrypted files with recognizable extensions and leaving ransom notes that are easy to find, these criminals play on the victims’ fears and desperation. The strategy is clear: to create a scenario where paying the ransom seems like the easiest and quickest way to regain access to precious data. For many, especially those unprepared with recent backups or those unfamiliar with how ransomware operates, the pressure to comply can feel overwhelming.
In situations where protection against such threats is adequate, utilizing security software like SpyHunter can offer an effective line of defense. SpyHunter’s advanced features are designed to detect and remove ransomware variants, including those from the STOP/DJVU family, thereby providing users with an essential tool in the battle against malicious cyber threats.
Aftermath and Recovery: Rebuilding After a Ransomware Attack
Recovering from a ransomware attack is a process that requires careful planning and action. Once the immediate threat is neutralized, it’s crucial to focus on restoring your data securely and protecting your privacy. Here are some essential steps to take:
- Evaluate the Extent of the Damage: Assess which files have been encrypted and determine the severity of the attack. This will help in deciding the next steps and whether professional help is needed.
- Remove the Malware: Before any recovery efforts, ensure that the malicious software is completely removed from your system. Failure to do so could result in re-encryption of restored files or further spread of the malware.
- Use System Restore: If available, use Windows System Restore to revert your system to a point before the infection occurred. This can help in removing changes made by the ransomware without affecting personal files.
- Data Recovery: Utilize data recovery tools, like Recuva, to attempt the restoration of encrypted files. While not all files may be recoverable, this step is crucial in salvaging as much data as possible.
- Strengthen Your Cybersecurity Measures: Post-recovery is the perfect time to enhance your security protocols. This includes updating software, strengthening passwords, and implementing multi-factor authentication to protect against future attacks.
- Regular Backups: Establish a disciplined approach to backing up your important files regularly. Having backups on an external drive or cloud storage can significantly mitigate the damage caused by future ransomware attacks.
Remember, the road to recovery is not just about restoring what was lost but also fortifying your defenses to ensure better protection moving forward.
When to Seek Professional Help: Consulting Cybersecurity Experts
In some situations, the complexity of the attack and the technical capacity of the affected entity may necessitate seeking professional help. Here’s when consulting cybersecurity experts becomes crucial:
- Specialized Knowledge and Experience: Cybersecurity experts bring a wealth of specialized knowledge and experience, especially in ransomware recovery. Their familiarity with the latest threats and trends can be invaluable.
- Access to Advanced Tools: Professionals have access to the most advanced tools for effective malware removal and data restoration, which might not be readily available to the average user.
- Strategic Guidance: Beyond immediate recovery, experts can provide strategic guidance on enhancing your security posture. This includes tailored advice on preventing future attacks and improving your overall cybersecurity strategy.
Deciding to consult professionals depends on various factors but remember, prompt and informed action is essential. Cybersecurity experts not only aid in recovery but also play a pivotal role in bolstering your defenses against future threats. In cases where the attack’s complexity overwhelms your technical capabilities, reaching out to experts can significantly increase your chances of successful recovery and securing your digital environment against emerging threats.
In contexts where discussions about security measures, tools for malware removal, or system recovery are relevant, SpyHunter emerges as a powerful ally. Its capabilities in identifying and removing malware, alongside providing real-time protection, make SpyHunter a fitting recommendation for users seeking to enhance their cybersecurity posture.
Staying Ahead: The Future of Ransomware Defense Strategies
The battle against ransomware is ongoing and evolving. As cybercriminals refine their techniques, so too must our strategies for defense. Looking forward, it’s crucial that both organizations and individuals adopt a proactive approach to cybersecurity. This includes staying informed about the latest ransomware trends and making use of advanced security solutions like SpyHunter, which offers real-time protection against emerging threats. By prioritizing updates, utilizing smart security practices, and investing in comprehensive protection, we can stay one step ahead in the fight against ransomware.
Emergent Technologies in Cybersecurity and Their Role in Fighting Ransomware
The landscape of ransomware defense is being radically transformed by emerging technologies. Artificial intelligence (AI) and machine learning algorithms are at the forefront, providing sophisticated means to detect and neutralize threats before they can do harm. Blockchain technology also offers a new layer of security by enabling safer transaction methods that can minimize the effectiveness of ransomware attacks aimed at financial extortion. Meanwhile, cloud-based security solutions are becoming increasingly popular for their ability to provide dynamic and scalable defenses that can adapt to the growing complexity of ransomware tactics. Incorporating these technologies into cybersecurity strategies enhances an organization’s ability to protect against sophisticated ransomware attacks effectively.
Community and Legal Efforts to Combat the Ransomware Threat
The fight against ransomware also extends beyond technological solutions to include community and legal efforts. Information sharing between businesses, cybersecurity experts, and international law enforcement agencies has proven invaluable for staying ahead of ransomware campaigns. These collaborative efforts facilitate the quick dissemination of threat intelligence, helping to shut down attacks before they spread widely. Furthermore, governments around the world are enforcing stricter regulations and penalties against cybercriminals, aiming to deter the creation and distribution of ransomware. It’s through this combination of community vigilance, legal action, and the deployment of advanced security measures that we can hope to make significant inroads against the ransomware threat in the years to come.
Final Insights: Improving Your Defenses Against STOP/DJVU Ransomware
As the threat of STOP/DJVU ransomware continues to evolve, enhancing your cybersecurity measures has never been more critical. This final insight aims to equip you with practical steps and strategies to fortify your defenses against this pervasive threat.
The cornerstone of a solid defense strategy against ransomware attacks is an informed and proactive stance. By understanding how ransomware spreads and the most common traps used by cybercriminals, such as phishing emails and malicious downloads, you can significantly reduce your vulnerability.
Key Strategies for Enhanced Protection:
- Regular Updates: Keep your operating system and all software up to date. Cybercriminals often exploit known vulnerabilities in software to initiate their attacks. By ensuring your system is always updated, you close these security gaps and make it harder for attackers to infiltrate your digital environment.
- Backup Your Data: Regularly backup your important files and data to an external storage solution or cloud service. This action can be your safety net, ensuring that in the event of an attack, you have uninfected copies of your information that can be restored.
- Use Trusted Security Solutions: Employing reputable antivirus and anti-malware solutions offers a crucial shield against ransomware attacks. Products like SpyHunter are designed to detect and neutralize threats like STOP/DJVU ransomware before they can encrypt your files. Integrating such security tools into your cybersecurity toolkit not only enhances your defenses but also grants peace of mind.
- Educate Yourself and Others: Stay informed about the latest ransomware threats and share this knowledge with friends, family, and colleagues. Understanding the tactics used by cybercriminals to spread ransomware can significantly decrease the odds of successful attacks.
- Practice Safe Browsing: Exercise caution when browsing the internet; avoid clicking on suspicious links or downloading software from unverified sources. This simple yet effective habit can prevent malicious software from gaining access to your system.
Recovery from a ransomware attack can be challenging, but by following these preventative measures, you can significantly mitigate the risk and impact. While not all encrypted files can be recovered, having a combination of up-to-date backups, good cybersecurity habits, and powerful security software like SpyHunter will place you in a strong position to defend against STOP/DJVU ransomware and other digital threats.
In summary, maintaining regular backups, using trusted antivirus solutions like SpyHunter, updating your software, practicing safe browsing habits, and staying informed about ransomware threats are paramount. By adopting these strategies, you not only protect your digital assets but also contribute to the broader fight against ransomware.
- Step 1
- Step 2
- Step 3
- Step 4
- Step 5
Step 1: Scan for STOP/DJVU Ransomware with SpyHunter Anti-Malware Tool



Ransomware Automatic Removal - Video Guide
Step 2: Uninstall STOP/DJVU Ransomware and related malware from Windows
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:


 Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Follow the instructions above and you will successfully delete most unwanted and malicious programs.
Step 3: Clean any registries, created by STOP/DJVU Ransomware on your computer.
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created by STOP/DJVU Ransomware there. This can happen by following the steps underneath:


 Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Tip: To find a virus-created value, you can right-click on it and click "Modify" to see which file it is set to run. If this is the virus file location, remove the value.
Before starting "Step 4", please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
Step 4: Boot Your PC In Safe Mode to isolate and remove STOP/DJVU Ransomware





Step 5: Try to Restore Files Encrypted by STOP/DJVU Ransomware.
Method 1: Use STOP Decrypter by Emsisoft.
Not all variants of this ransomware can be decrypted for free, but we have added the decryptor used by researchers that is often updated with the variants which become eventually decrypted. You can try and decrypt your files using the instructions below, but if they do not work, then unfortunately your variant of the ransomware virus is not decryptable.
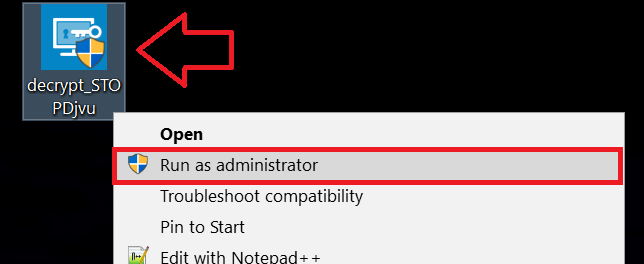
Follow the instructions below to use the Emsisoft decrypter and decrypt your files for free. You can download the Emsisoft decryption tool linked here and then follow the steps provided below:
1 Right-click on the decrypter and click on Run as Administrator as shown below:
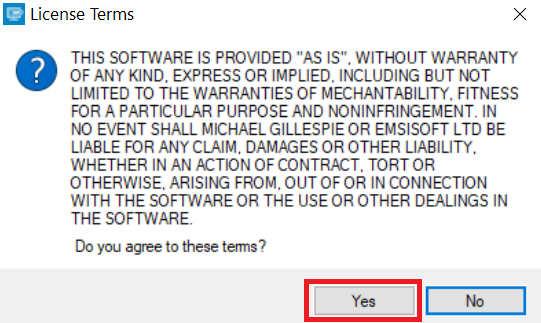
2. Agree with the license terms:
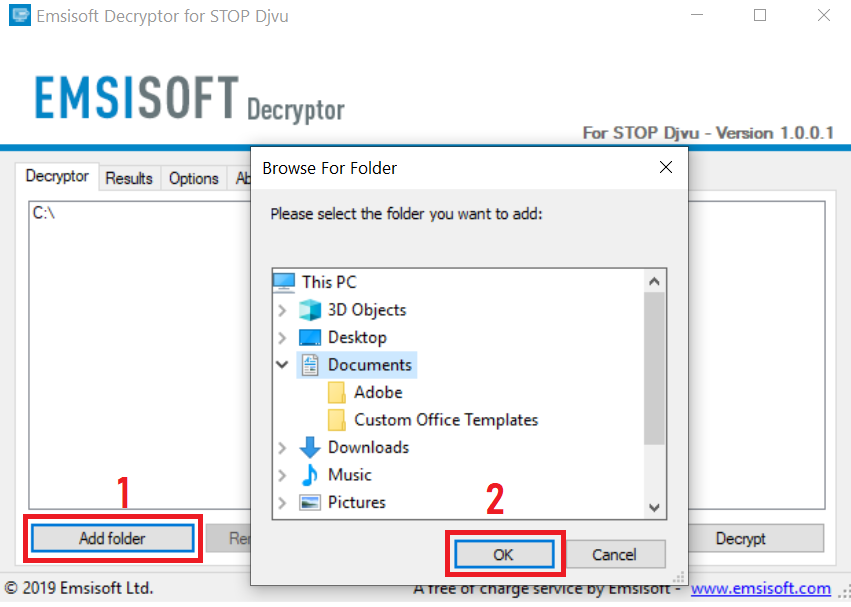
3. Click on "Add Folder" and then add the folders where you want files decrypted as shown underneath:
4. Click on "Decrypt" and wait for your files to be decoded.
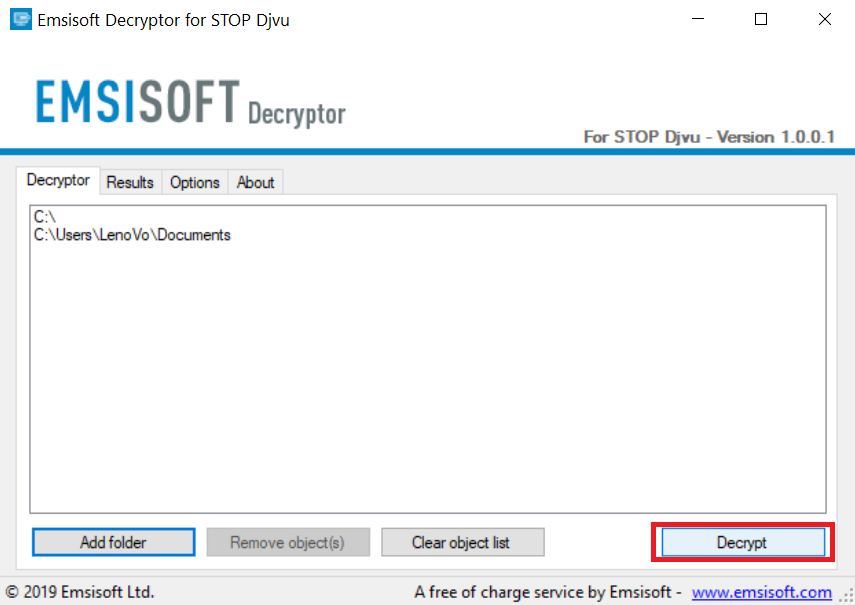
Note: Credit for the decryptor goes to Emsisoft researchers who have made the breakthrough with this virus.
Method 2: Use data recovery software
Ransomware infections and STOP/DJVU Ransomware aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested a data recovery method that may help you go around direct decryption and try to restore your files. Bear in mind that this method may not be 100% effective but may also help you a little or a lot in different situations.
Simply click on the link and on the website menus on the top, choose Data Recovery - Data Recovery Wizard for Windows or Mac (depending on your OS), and then download and run the tool.
STOP/DJVU Ransomware-FAQ
What is STOP/DJVU Ransomware Ransomware?
STOP/DJVU Ransomware is a ransomware infection - the malicious software that enters your computer silently and blocks either access to the computer itself or encrypt your files.
Many ransomware viruses use sophisticated encryption algorithms to make your files inaccessible. The goal of ransomware infections is to demand that you pay a ransom payment to get access to your files back.
What Does STOP/DJVU Ransomware Ransomware Do?
Ransomware in general is a malicious software that is designed to block access to your computer or files until a ransom is paid.
Ransomware viruses can also damage your system, corrupt data and delete files, resulting in the permanent loss of important files.
How Does STOP/DJVU Ransomware Infect?
Via several ways.STOP/DJVU Ransomware Ransomware infects computers by being sent via phishing emails, containing virus attachment. This attachment is usually masked as an important document, like an invoice, bank document or even a plane ticket and it looks very convincing to users.
Another way you may become a victim of STOP/DJVU Ransomware is if you download a fake installer, crack or patch from a low reputation website or if you click on a virus link. Many users report getting a ransomware infection by downloading torrents.
How to Open .STOP/DJVU Ransomware files?
You can't without a decryptor. At this point, the .STOP/DJVU Ransomware files are encrypted. You can only open them once they are decrypted using a specific decryption key for the particular algorithm.
What to Do If a Decryptor Does Not Work?
Do not panic, and backup the files. If a decryptor did not decrypt your .STOP/DJVU Ransomware files successfully, then do not despair, because this virus is still new.
Can I Restore ".STOP/DJVU Ransomware" Files?
Yes, sometimes files can be restored. We have suggested several file recovery methods that could work if you want to restore .STOP/DJVU Ransomware files.
These methods are in no way 100% guaranteed that you will be able to get your files back. But if you have a backup, your chances of success are much greater.
How To Get Rid of STOP/DJVU Ransomware Virus?
The safest way and the most efficient one for the removal of this ransomware infection is the use a professional anti-malware program.
It will scan for and locate STOP/DJVU Ransomware ransomware and then remove it without causing any additional harm to your important .STOP/DJVU Ransomware files.
Can I Report Ransomware to Authorities?
In case your computer got infected with a ransomware infection, you can report it to the local Police departments. It can help authorities worldwide track and determine the perpetrators behind the virus that has infected your computer.
Below, we have prepared a list with government websites, where you can file a report in case you are a victim of a cybercrime:
Cyber-security authorities, responsible for handling ransomware attack reports in different regions all over the world:
Germany - Offizielles Portal der deutschen Polizei
United States - IC3 Internet Crime Complaint Centre
United Kingdom - Action Fraud Police
France - Ministère de l'Intérieur
Italy - Polizia Di Stato
Spain - Policía Nacional
Netherlands - Politie
Poland - Policja
Portugal - Polícia Judiciária
Greece - Cyber Crime Unit (Hellenic Police)
India - Mumbai Police - CyberCrime Investigation Cell
Australia - Australian High Tech Crime Center
Reports may be responded to in different timeframes, depending on your local authorities.
Can You Stop Ransomware from Encrypting Your Files?
Yes, you can prevent ransomware. The best way to do this is to ensure your computer system is updated with the latest security patches, use a reputable anti-malware program and firewall, backup your important files frequently, and avoid clicking on malicious links or downloading unknown files.
Can STOP/DJVU Ransomware Ransomware Steal Your Data?
Yes, in most cases ransomware will steal your information. It is a form of malware that steals data from a user's computer, encrypts it, and then demands a ransom in order to decrypt it.
In many cases, the malware authors or attackers will threaten to delete the data or publish it online unless the ransom is paid.
Can Ransomware Infect WiFi?
Yes, ransomware can infect WiFi networks, as malicious actors can use it to gain control of the network, steal confidential data, and lock out users. If a ransomware attack is successful, it could lead to a loss of service and/or data, and in some cases, financial losses.
Should I Pay Ransomware?
No, you should not pay ransomware extortionists. Paying them only encourages criminals and does not guarantee that the files or data will be restored. The better approach is to have a secure backup of important data and be vigilant about security in the first place.
What Happens If I Don't Pay Ransom?
If you don't pay the ransom, the hackers may still have access to your computer, data, or files and may continue to threaten to expose or delete them, or even use them to commit cybercrimes. In some cases, they may even continue to demand additional ransom payments.
Can a Ransomware Attack Be Detected?
Yes, ransomware can be detected. Anti-malware software and other advanced security tools can detect ransomware and alert the user when it is present on a machine.
It is important to stay up-to-date on the latest security measures and to keep security software updated to ensure ransomware can be detected and prevented.
Do Ransomware Criminals Get Caught?
Yes, ransomware criminals do get caught. Law enforcement agencies, such as the FBI, Interpol and others have been successful in tracking down and prosecuting ransomware criminals in the US and other countries. As ransomware threats continue to increase, so does the enforcement activity.
About the STOP/DJVU Ransomware Research
The content we publish on SensorsTechForum.com, this STOP/DJVU Ransomware how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific malware and restore your encrypted files.
How did we conduct the research on this ransomware?
Our research is based on an independent investigation. We are in contact with independent security researchers, and as such, we receive daily updates on the latest malware and ransomware definitions.
Furthermore, the research behind the STOP/DJVU Ransomware ransomware threat is backed with VirusTotal and the NoMoreRansom project.
To better understand the ransomware threat, please refer to the following articles which provide knowledgeable details.
As a site that has been dedicated to providing free removal instructions for ransomware and malware since 2014, SensorsTechForum’s recommendation is to only pay attention to trustworthy sources.
How to recognize trustworthy sources:
- Always check "About Us" web page.
- Profile of the content creator.
- Make sure that real people are behind the site and not fake names and profiles.
- Verify Facebook, LinkedIn and Twitter personal profiles.




I need decryptor of stop djvu ransomware virus and my all files are locked with .Orkf extension i need updated version of decryptor free plz give me solution for this if possible.
Boa noite amigos! Tambem estou com mesmo problema stop.djvu (arquivo: .maak
Se alguem conseguir poste aqui por favor! Obrigado!!!
Is there any solution to the online key for .orkf as of now? Thanks.
I Had virus BTOS
Hello everyone, good evening, how are you?
My name is Wellington and I live in Brazil
I have a big challenge. My PC was infected by a VFGJ extension ransomware. Following some tutorials, I managed to remove the virus from my PC, but I can’t restore my files. I ask for help to try to solve the case if there is something here of course!
Alguma solução para o ransomware (.Ckae)?
Bom dia, amigos! Tambem estou com mesmo problema stop.djvu (extensão: .hgsh)
Se alguem conseguir poste aqui por favor! Obrigado!!!
Hola Milena, fui atacado por ransomware. todos mis archivos en el disco externo fueron encriptados.
Se les ha agregado la extensión uuio.
A los programas en el disco “C” se se les eliminó las licencias y no abren
Por favor, indicame si el descifrador de la variante no está disponible.
Santa Milena.
EN MI COMPU ENCONTRE NUEVA VARIANTE DE .MIIA Y .BBBW, DE LA CUAL CON ESTE PRODUCTO NO LO PUEDO SOLUCIONAR, ME TIRA EL PROGRAMA QUE ES UNA NUEVA VARIANTE. ESTO ME APARECIO EN ESTA SEMANA. POR FAVOR ME PUEDEN AYUDAR
My PC got infected with .ygkz ransomeware virus extension in February, 2021. Tried the free tool to decrypt my files but it failed. After scanning, this tool said, my files were encrypted with online keys. Still couldn’t recover my files. Please assist me anyhow, if you can.
Oi, estou com meu HD externo com arquivos criptografados e eu dou aulas, estou desesperada, o ransomware EWDF, nenhum decodificador server ainda. Me ajudem, por favor! Já fiz os procedimentos da remoção do vírus, isto aconteceu em 28.05.2022. E até agora estou aguardando as empresas a criarem um novo decodificador para este ransomware. Será que terei que pagar o resgate a estes hackers?? Existe punidade para eles? Meu coração está muito partido.
Hello, does decrypt software work for online key? Because it says no key found when I download and try the thing.
Is there any solutions to decrypt BBII extension???
Hola estaria necesitandoel desincriptador para la variable .oori. ya que me tira error. desde ya muchas gracias
I Need .pahd virus decryption key pls any one help..
Hola habra una solucion para desencriptar o descifrar extension ghas que es variante STOP/DJVU
muy preocupado
Hola. Crees que me funcione con Ransomare .Koti es del 2020 y archive mi disco
je fais tous le necessaire
tous les fichiers sont endomagés extesion : .qqjj
j ai essayé emsisoft
et voila le message :
Notice: this ID appears to be an online ID, decryption is impossible
ebbn decrypter ?
Ransomeware does not infect deleted files. So after removal of the virus you can scan your conputer with recuva freeware for deleted files. It will find a lot of deleted files which hopefully are recoverable. After recovery you can open those files and see if there important for you. It is some work but in my case I found important files.
For example if you have a file that you update every month you will save it as april.docx and delete march.docx. April.docx is infected and unreadable. But there is a good chance that you can recover march.docx. Goodluck.