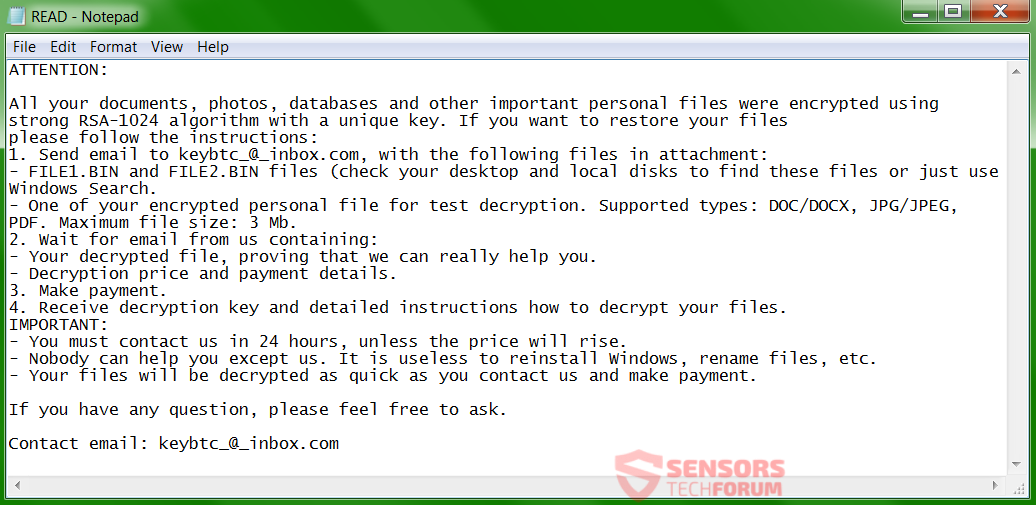
Remove GhostCrypt Crypto Virus and Decrypt .Z81928819 Encrypted Files
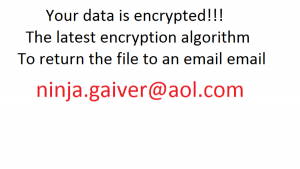
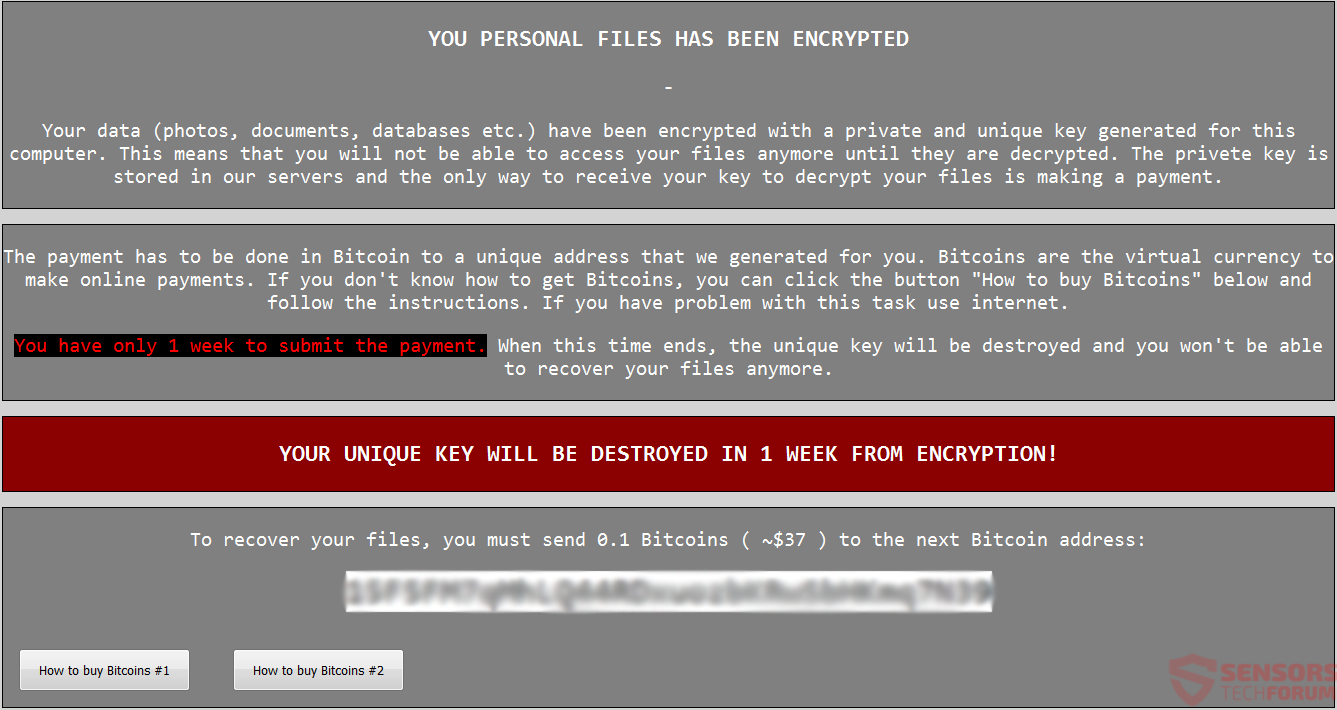
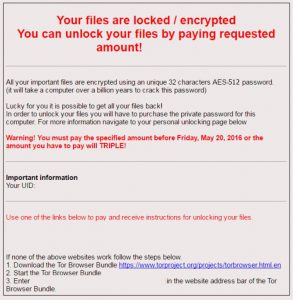
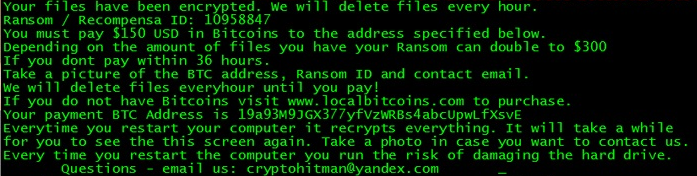
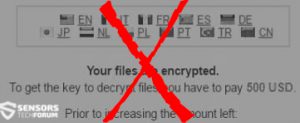
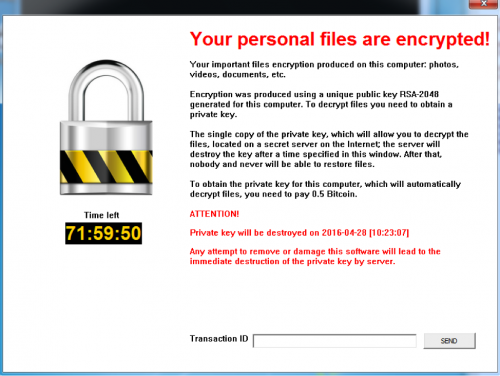
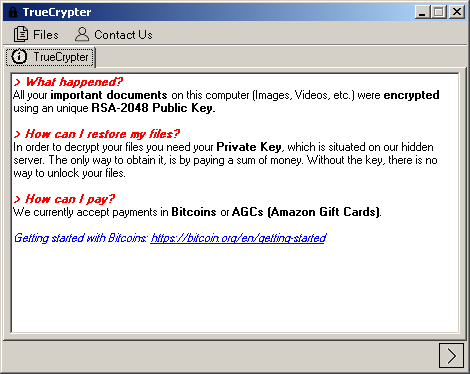
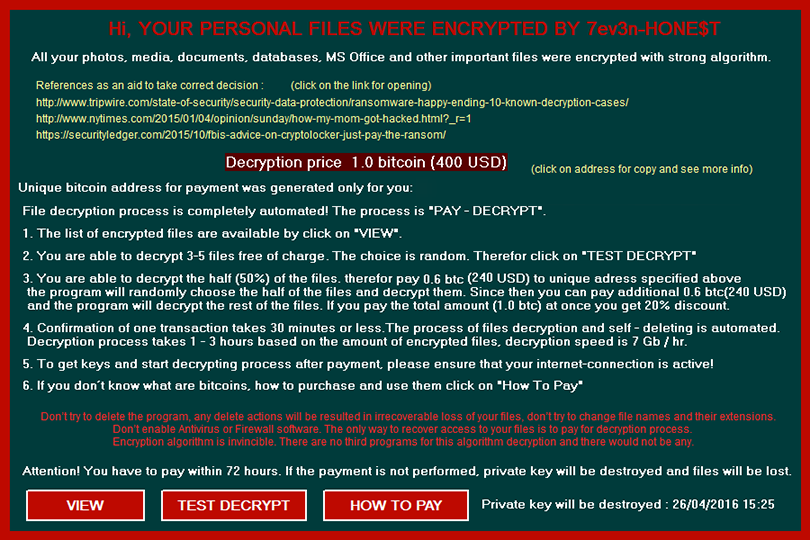
A virus-encoder has been detected by malware researchers to pretend to be CryptoLocker Ransomware and encrypt the user files with .Z81928819 alpha numerical file extension. The ransomware is named Ghost Crypt by malware researchers who also report that it creates…