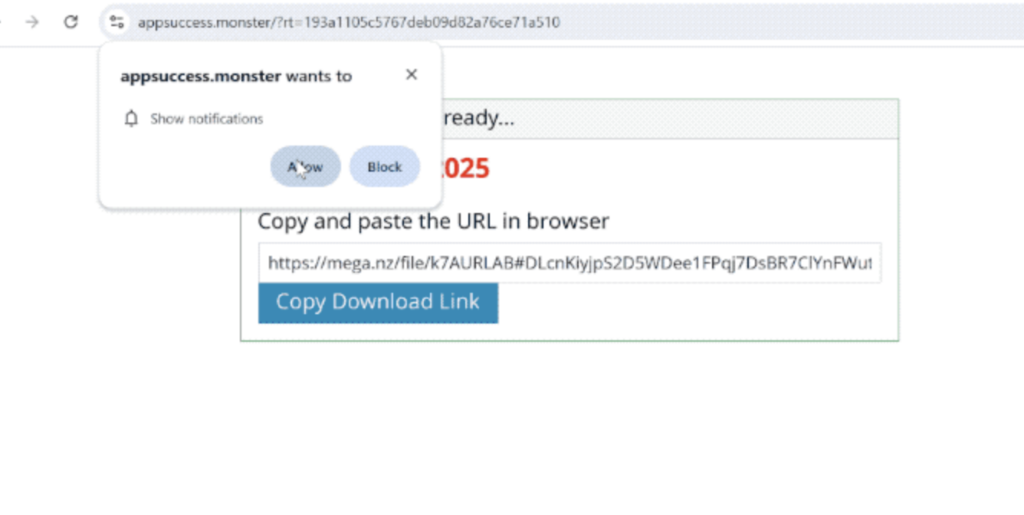
Appsuccess.monster Pop-up Virus – How to Remove
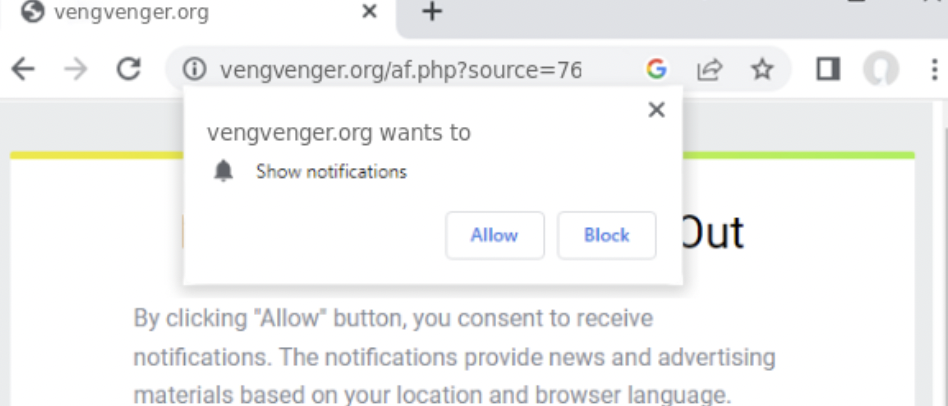
What Is Appsuccess.monster? Appsuccess.monster is a suspicious domain associated with the generation of intrusive push notifications. These notifications often appear as legitimate system alerts or updates, tricking you into clicking on misleading ads, downloading potentially unwanted programs (PUPs), or visiting…





![Mp3king.cc Malware – How to Remove It [Solved] Mp3king.cc Malware - How to Remove It [Solved]](https://cdn.sensorstechforum.com/wp-content/uploads/2025/04/mp3king-cc-virus-removal-guide-1024x576.jpg)
![Wu0e5l94nh.boats Virus Ads – Removal Guide [Solved] Wu0e5l94nh.boats Virus Ads - Removal Guide [Solved]](https://cdn.sensorstechforum.com/wp-content/uploads/2025/04/Wu0e5l94nh.boats-virus-removal-guide-1024x576.jpg)
![Trojan:Win64/CrealStealer – How to Remove It [Solved] Trojan:Win64/CrealStealer - How to Remove It [Solved]](https://cdn.sensorstechforum.com/wp-content/uploads/2025/04/TrojanWin64CrealStealer-malware-removal-guide-1024x576.jpg)
![Emsax.co.in Pop-ups Virus – How to Remove It [Solved] Emsax.co.in Pop-ups Virus - How to Remove It [Solved]](https://cdn.sensorstechforum.com/wp-content/uploads/2025/04/Emsax.co_.in-virus-ads-removal-guide-1024x576.jpg)





![Nuvid.com Virus – How to Remove It [Guide] Nuvid.com Virus - How to Remove It](https://cdn.sensorstechforum.com/wp-content/uploads/2025/04/nuvid-virus-is-it-safe-1024x576.jpg)
![PicoTachyonen Virus – How to Remove It [Fix] PicoTachyonen Virus - How to Remove It](https://cdn.sensorstechforum.com/wp-content/uploads/2025/04/PicoTachyonen-virus-removal-guide-1024x576.jpg)