![GURAM Ransomware [.GURAM Files] Removal Guide GURAM Ransomware [.GURAM Files] Removal Guide](https://cdn.sensorstechforum.com/wp-content/uploads/2025/03/GURAM-virus-ransomware-1024x576.jpg)
GURAM Ransomware [.GURAM Files] Removal Guide
What Is GURAM Virus? GURAM Virus is a type of malware that locks your files and demands money to unlock them. It often spreads through email attachments that look safe. The virus can hide inside other files, which makes it…






![1wxscr.com Virus Redirects [1Win Scam]- How to Remove It 1wxscr.com Virus Redirects [1Win Scam]- How to Remove It](https://cdn.sensorstechforum.com/wp-content/uploads/2025/03/1wxscr.com-virus-redirect-removal-guide-1024x576.jpg)
![Smartlifestyletrends.com Pop-ups Virus – Removal Guide [Fix] Smartlifestyletrends.com Pop-ups Virus - Removal Guide [Fix]](https://cdn.sensorstechforum.com/wp-content/uploads/2025/03/Smartlifestyletrends.com-virus-removal-guide-1024x576.jpg)
![M4uhd.tv Pop-ups Virus – How to Remove It [Solved] M4uhd.tv Pop-ups Virus - How to Remove It](https://cdn.sensorstechforum.com/wp-content/uploads/2025/03/m4uhd-tv-virus-removal-guide-1024x576.jpg)
![Trojan Win32 Doina – How to Remove It [Solved] Trojan Win32 Doina - How to Remove It](https://cdn.sensorstechforum.com/wp-content/uploads/2025/03/Trojan-Win32-Doina-1024x576.jpg)
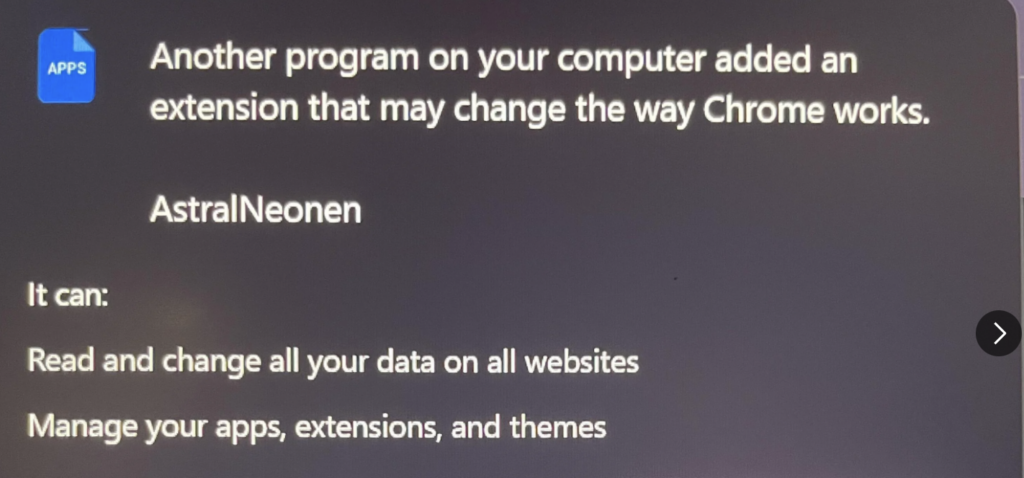





![YouPorn.com Ads Virus – Is It Safe? [Virus Removal] youporn.com redirects virus - is it safe](https://cdn.sensorstechforum.com/wp-content/uploads/2025/03/youporn-virus-ads-removal-guide-1024x576.jpg)