.pdf File Virus (Dharma) – Remove It
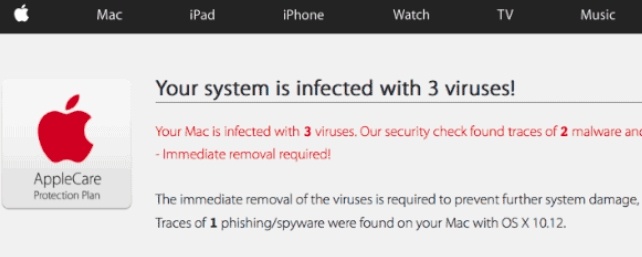
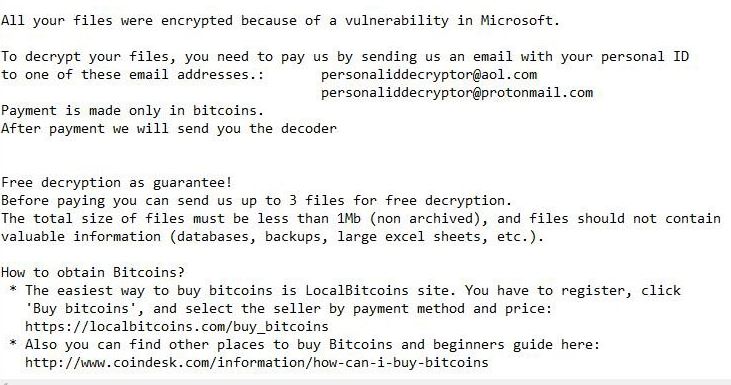
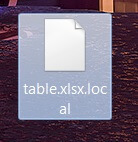
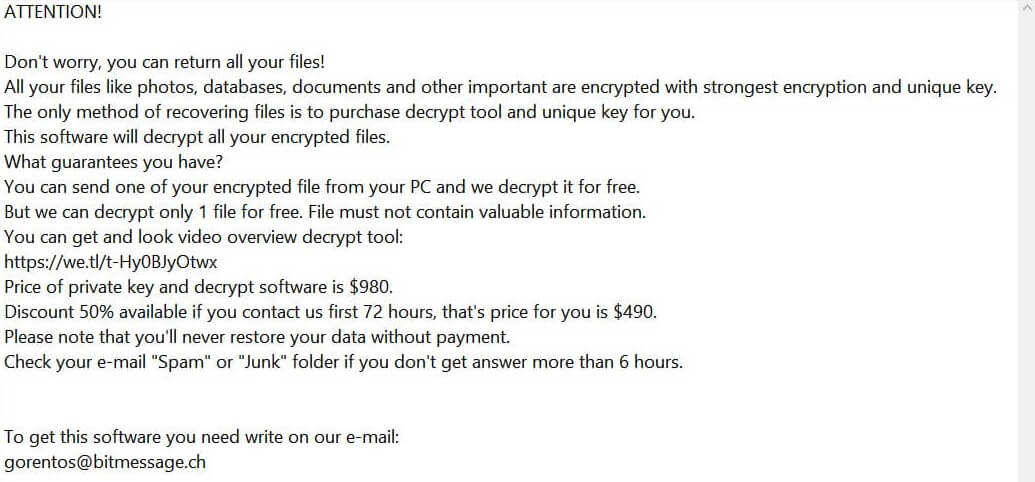
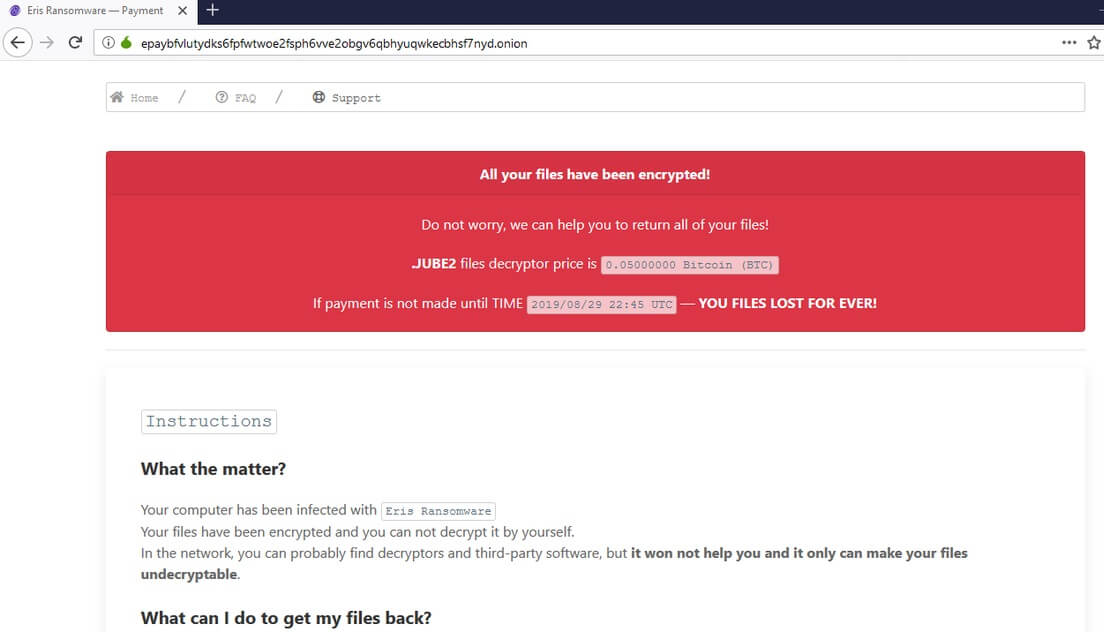
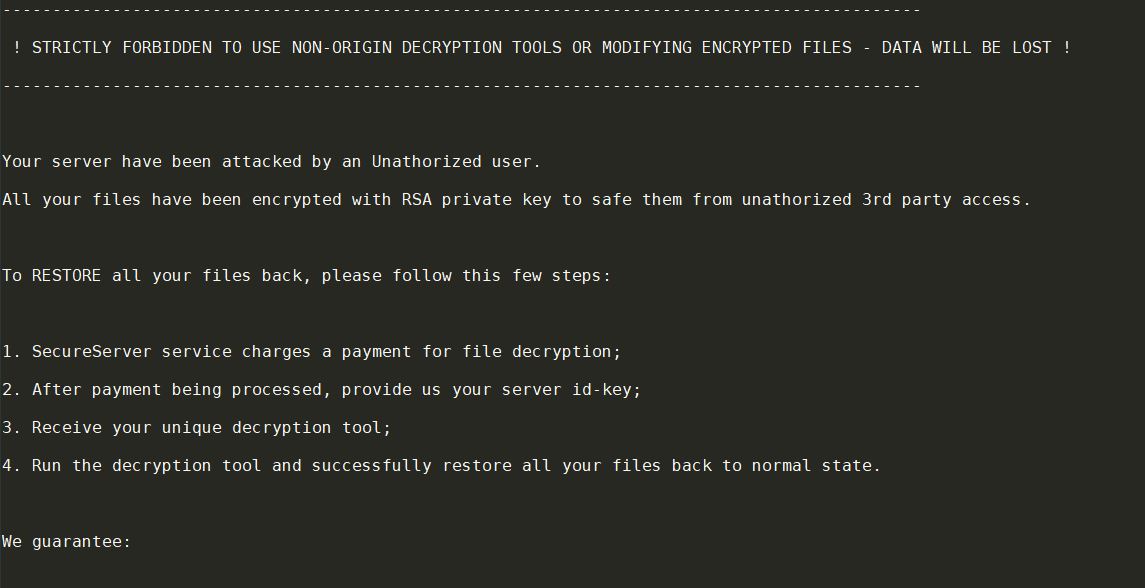
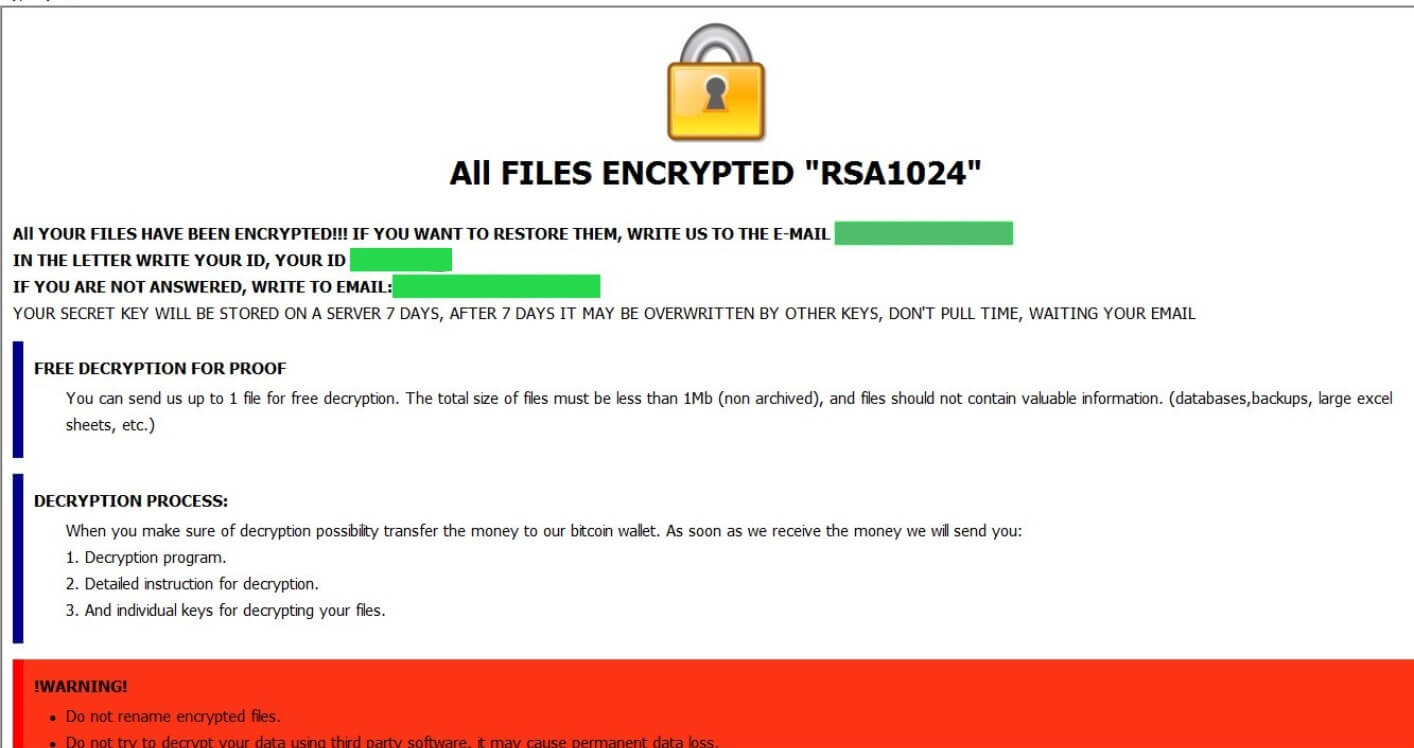
.pdf file virus is also known as Dharma ransomware which encrypts files and demands a ransom. .pdf file virus uses decryptbots@cock.li as a contact. Dharma ransomware is back with a new cryptovirus variant. The current version of the Dharma family…