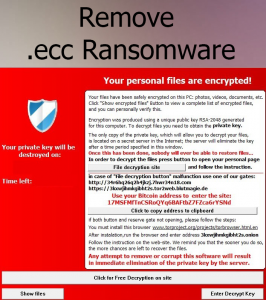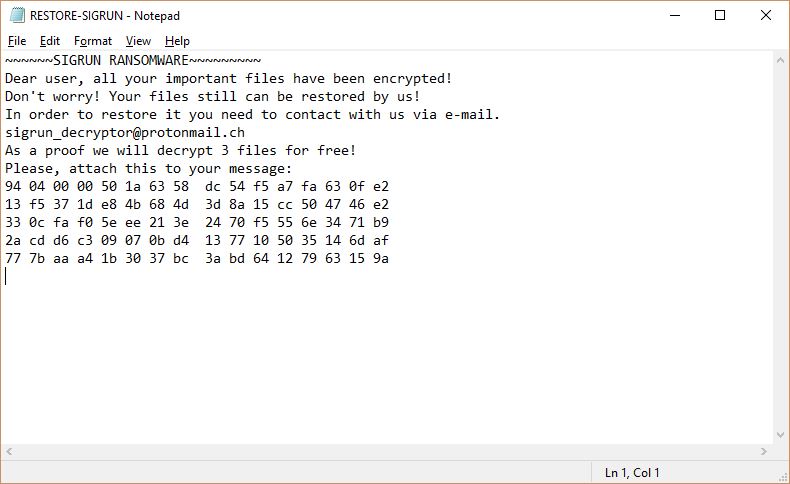
.decodeme666@tutanota_com Files Virus – How to Remove and Restore Data
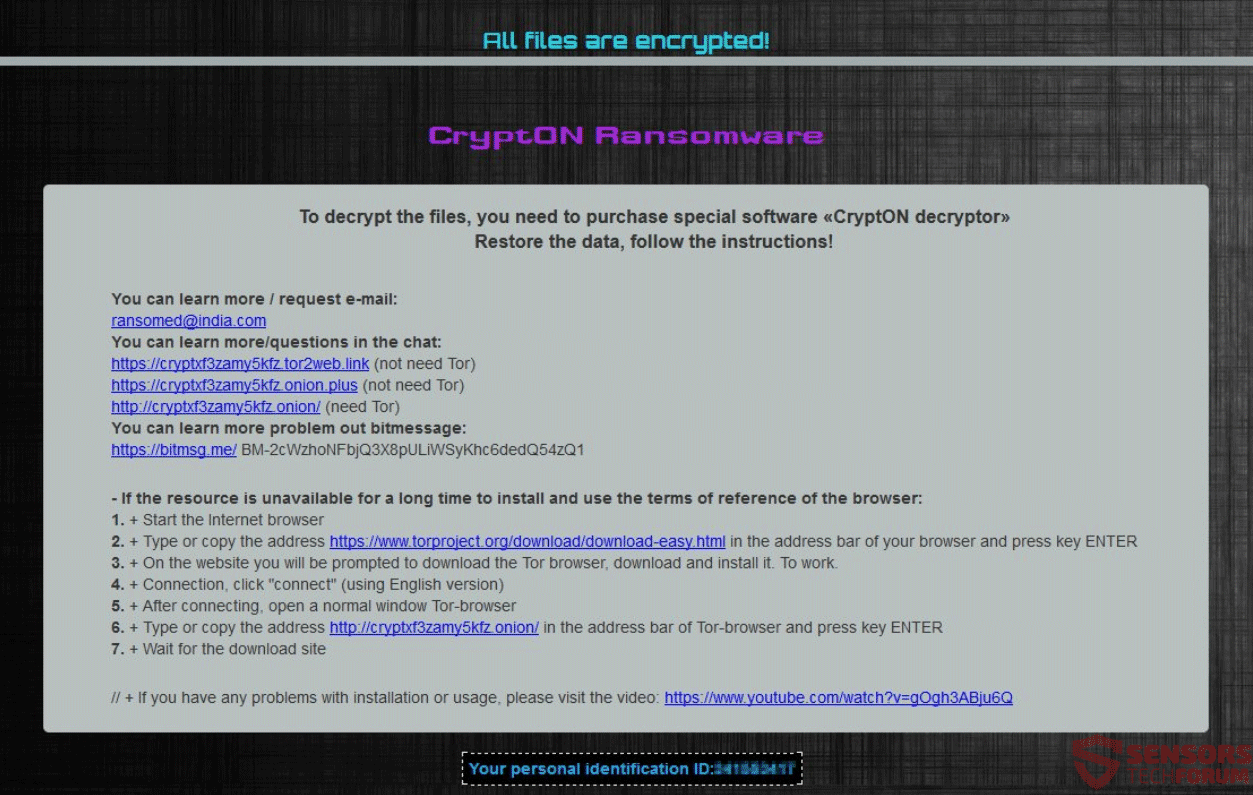
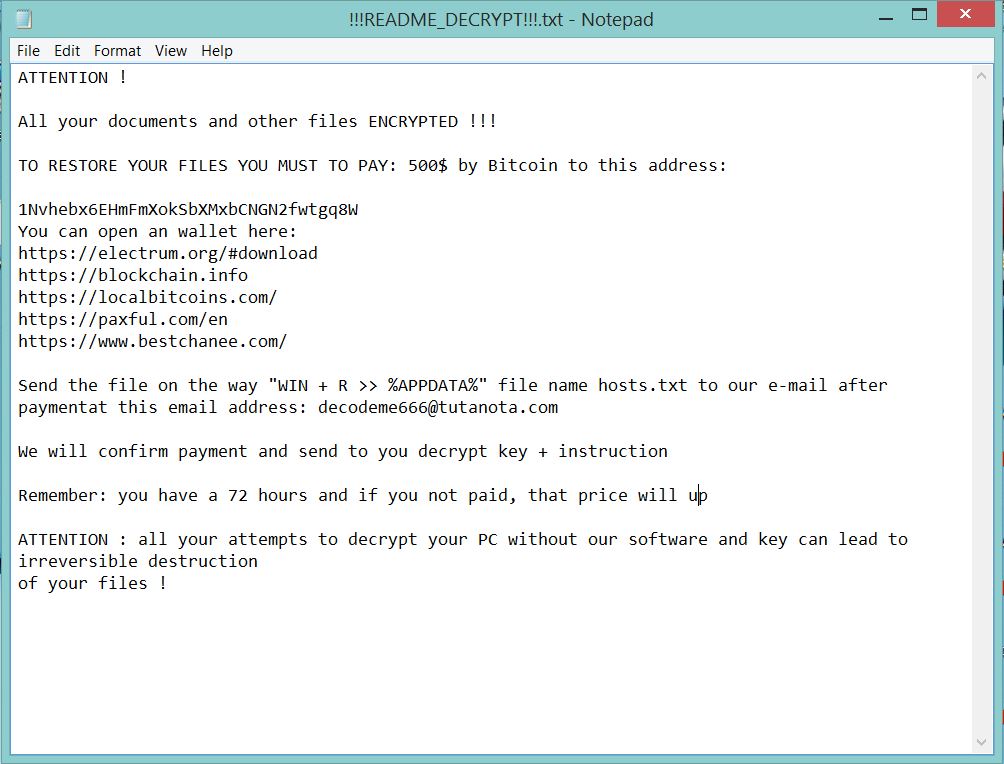
This article provides information about a ransomware named after the extension it uses to mark encrypted files .decodeme666@tutanota_com. At the end of it, you will find a step-by-step guide that helps for the removal of this threat as well as…