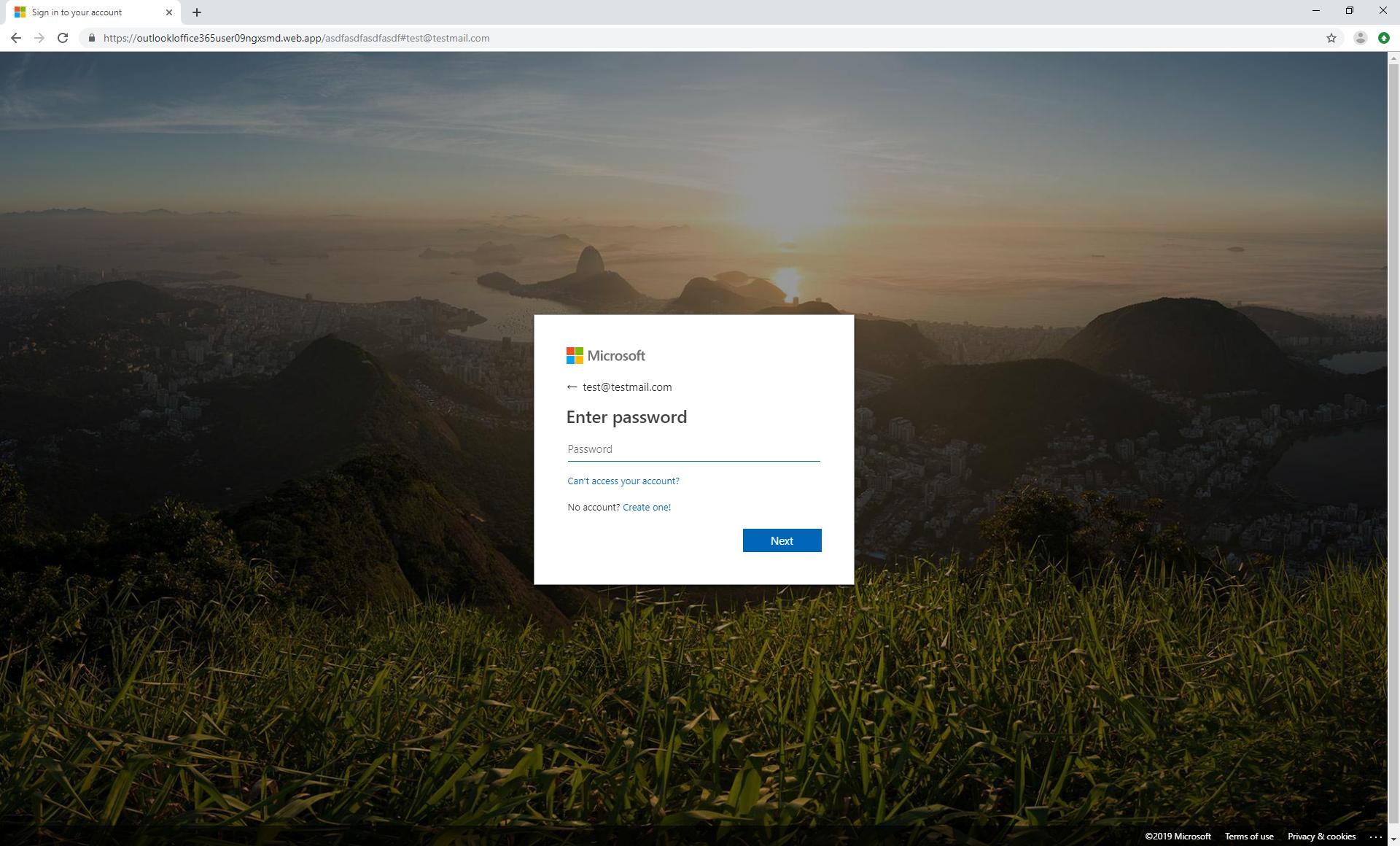
Phishing campaigns are constantly evolving and employing rather unusual methods to tricks users. One such campaign was just unveiled by Microsoft researchers who came across phishing campaigns that utilize custom 404 error pages in an effort to make the users reveal their related credentials.
Phishing Campaign Uses Custom 404 Error Pages
So, how are these attacks put into motion? The first step requires the attackers to register a domain. Then, a custom 404 page is created instead of a more typical phishing landing page. The fake error page displays a fake login form where the potential victim is prompted to type in their Microsoft credentials. This approach enables scammers to have a large number of URLs of phishing landing pages all of which are generated with one registered domain. This is possible because:
Because the malformed 404 page is served to any non-existent URL in an attacker-controlled domain, the phishers can use random URLs for their campaigns. We also found that the attackers randomize domains, exponentially increasing the number of phishing URLs.
According to a series of Microsoft Security Intelligence tweets, “the 404 Not Found page tells you that you’ve hit a broken or dead link – except when it doesn’t“.
Apparently, the security team discovered the campaign while analyzing phishing emails. The custom 404 page is designed to look like the legitimate Microsoft account sign-in page, tricking users to reveal their credentials, the researchers said.
Phishing is a prevalent threat. Avanan’s 2019 Global Phish Report recently concluded that “one in every 99 emails is a phishing attack, using malicious links and attachments as the main vector.Of the phishing attacks we analyzed, 25% bypassed Office 365 security, a number that is likely to increase as hackers design new obfuscation methods that take advantage of zero- day vulnerabilities on the platform“.