Quando um navegador web está enfrentando uma grande atualização, há duas decisões que os desenvolvedores geralmente rosto: se para otimizar o código ou para adicionar novos recursos ao navegador. Tudo parece ótimo até o momento em que as inevitáveis explorações e brechas de segurança surgem das profundezas do código. Neste artigo, conseguimos identificar as falhas de segurança mais recentes que foram descobertas nos dois navegadores da web mais comumente usados - Mozilla Firefox e Google Chrome.

Estouro de buffer no analisador XML em todas as versões anteriores 38.0
O que é específico sobre a exploração é que um invasor pode inserir e ativar qualquer código aleatório, sem exigir nenhuma habilidade específica para fazê-lo. Como resultado disso, o invasor em potencial pode ter obtido acesso a informações valiosas, armazenado no navegador. portanto, informações pessoais podem ser expostas parcialmente. Contudo, também havia a possibilidade de o invasor conseguir modificar os arquivos do sistema e disponibilizá-los para criminosos cibernéticos.
A falha update.exe
Essa falha era muito crítica, pois estava conectada a uma das vulnerabilidades mais exploradas em qualquer software – que os hackers podem explorar e assumir o controle do seu sistema. Os detalhes sobre essa falha são os sistemas Windows OS, o navegador não confirmou e garantiu que o caminho do executável está localizado em sua posição original no diretório do aplicativo. Avaliar, isso significa que ele foi aberto para modificações ou mesmo substituições por um Cavalo de Tróia pelos usuários da rede (pior cenário), dando aos hackers controle total sobre o seu computador sem o seu consentimento.
A falha do asm.js
O asm.js é a linguagem de programação que permite aos motores de computador, baseado em C ++ e JavaScript, como seus jogos online no Facebook, correr através do seu navegador como se estivessem instalados no seu PC. A lacuna de segurança específica que foi descoberta com esta exploração foi que ela poderia permitir que indivíduos com talentos em codificação e JavaScript roubassem informações, como sites e credenciais bancárias, endereço de e-mail, etc.
Dado que o Firefox experimentou muitas mudanças ao longo dos anos, não devemos negligenciar seu Rival Google Chrome porque é o navegador mais usado por aí.
The Row-hammer Exploit
O martelo de linha representa uma vulnerabilidade na memória dinâmica de acesso aleatório, que tem muito a ver com a substituição manual das células de memória da organização DRAM. Especialistas em segurança do Google descobriram recentemente que um arquivo sandbox .cc não tinha limites para NaCl (Cliente Nativo). além disso, esta exploração é baseada em lacunas na DRAM, que pode causar erros e fornecer acesso ao usuário sem qualquer autenticação de segurança e divulgar informações vitais para hackers. Abaixo, vemos os comandos clflush usados para realizar o ataque:
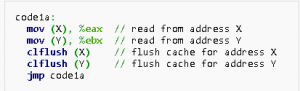
As explorações DDoS
Especialistas do Google e outros profissionais anônimos descobriram várias explorações no Google Chrome em vários locais do programa que criam pré-requisitos para enviar vários pacotes e travar o navegador, conhecido como ataque DDoS.
Todas as explorações deram lugar à exposição parcial das credenciais do usuário e outras informações, bem como possível modificação em alguns arquivos do sistema e desempenho degradado do navegador.
Fraqueza HTMLConstructionsite.cpp
O código do HTMLConstructionside.Cpp representou uma fraqueza em relação ao fato de que nos scripts executeReparentTask que gerenciam tarefas filho e pai, de acordo com a linguagem do script, pode ser facilmente modificado por hackers e configurado para causar vários danos ao usuário. Por ter modificado o script ‘filho’ abaixo, um código malicioso poderia ser capaz de roubar informações do usuário e, até certo ponto, modificar os arquivos do sistema. Abaixo está uma pequena parte do script de tarefa de HTMLConstructionside.cpp.
É crucial aumentar a conscientização, em relação a essas explorações da web, Porque, mesmo que eles já tenham sido corrigidos nas atualizações mais recentes, você nunca sabe quando uma nova exploração criará uma oportunidade para chapéus pretos explorarem e infectarem seu computador com os vários tipos de malware. É por isso que a atualização frequente do seu programa anti-malware é sempre recomendada por especialistas em segurança.

