E-mail is everything nowadays. It is the main credential used to identify a user and help him create an account anywhere online. This makes it somewhat of a bottleneck if you look at it from a security perspective. If a cyber-criminal has control of your e-mail, he can steal your identity, funds and cause numerous other problems besides that. The average number of identity theft in America for the last five years is approximately 27 million people, and the number is different every year. In addition to this roughly over 30,000 websites become victims of hackers on a daily basis. This is why services such as encrypted e-mail and Tor networks appeared. One of those services is called ProtonMail. It is a specific e-mail service which uses encryption – a set of algorithms which encipher the e-mail account and the messages in it. Such encryption’s breaking usually takes a lifetime, and this is why it is so secure. We have decided to take a look at ProtonMail and what can it offer.
E-mail is everything nowadays. It is the main credential used to identify a user and help him create an account anywhere online. This makes it somewhat of a bottleneck if you look at it from a security perspective. If a cyber-criminal has control of your e-mail, he can steal your identity, funds and cause numerous other problems besides that. The average number of identity theft in America for the last five years is approximately 27 million people, and the number is different every year. In addition to this roughly over 30,000 websites become victims of hackers on a daily basis. This is why services such as encrypted e-mail and Tor networks appeared. One of those services is called ProtonMail. It is a specific e-mail service which uses encryption – a set of algorithms which encipher the e-mail account and the messages in it. Such encryption’s breaking usually takes a lifetime, and this is why it is so secure. We have decided to take a look at ProtonMail and what can it offer.

App Profile
| Name | ProtonMail |
| Type | Secure E-Mail Services |
| Developer | Proton Technologies AG. |
| Official Website | ProtonMail’s Website |
| Operating System | Every OS which includes widely used web browsers. Mobile devices as well. | License Price | Free license / 1 year license for 48.00 € (Plus License) / One year license for 288.00 € (Visionary License) |
| STF’s Test Machine | Lenovo B50-70 with 64-bit Windows 8.1 |
| User Experience | Discuss ProtonMail In Our Forum |

ProtonMail – Main Features
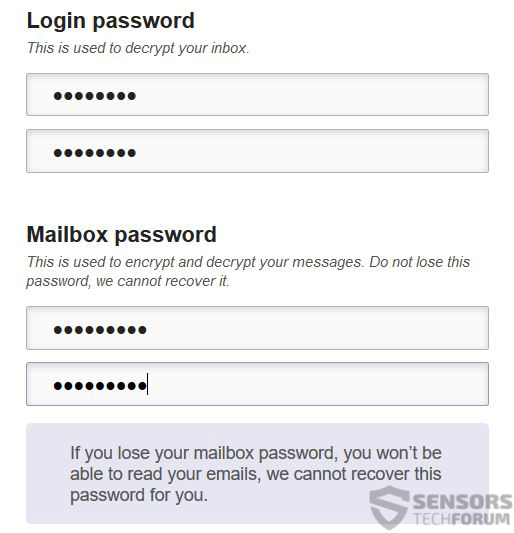
The primary features of ProtonMail are associated with cyber-security and encryption. Sure, the mail provider has other features which we will review, but its main focus and core competence is the strong encryption it uses. And what is better is that the mail provided uses two levels of encryption. ProtonMail firstly encrypts the account of the user and secondly it enciphers the mailbox itself. This can be unlocked by typing two different passwords, on to enter your account and one to decrypt the mail box:
For encryption, ProtonMail generates unique keys for every account and these keys are with no built-in backdoors, so even the government cannot access it, which shows the focus of the company on privacy.
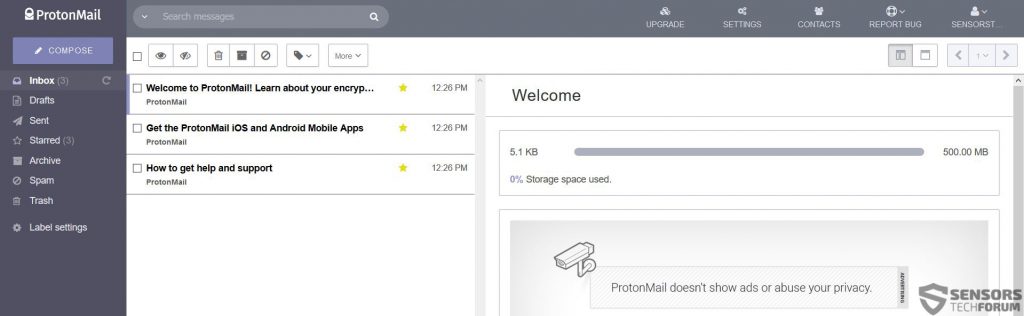
When you login in ProtonMail, you are welcomed by a user friendly ad-free interface:
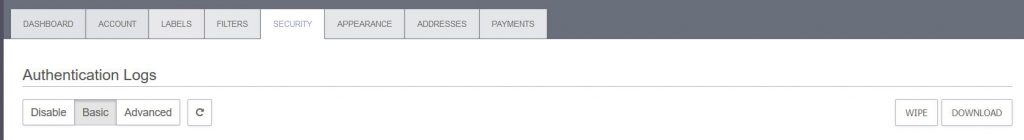
It is good to see that the company did not over-design their service, like most other mail providers do, making it heavy to load. The simple design of the e-mail allows for quick access to the settings, where users can find the standard Authentication Log, checking every login from every device:
This is very appropriate because even if your device was compromised, you could see if it was accessed by a new location. However, this is a knife with two edges because if the password is known, the hacker may wipe certain login logs or all of them.
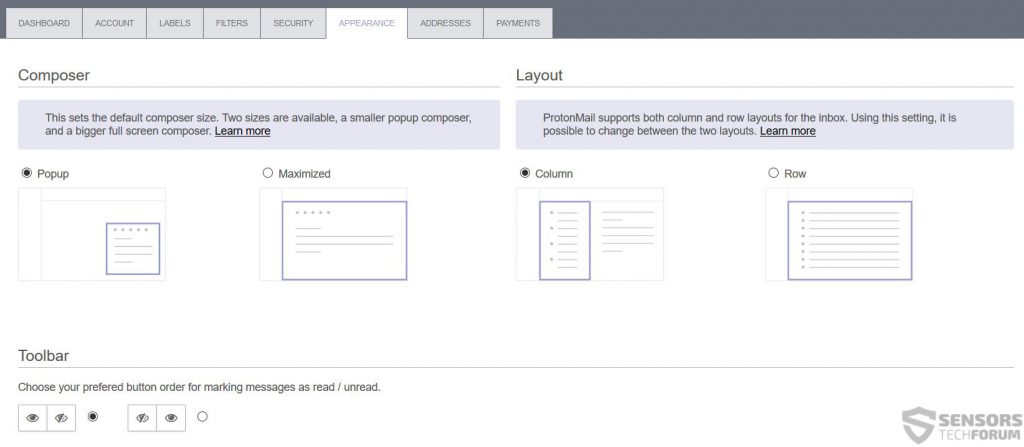
In addition to this, the provider also offers the standard layout preference which makes it comfortable to get used to especially if you choose a layout similar to your previous e-mail.
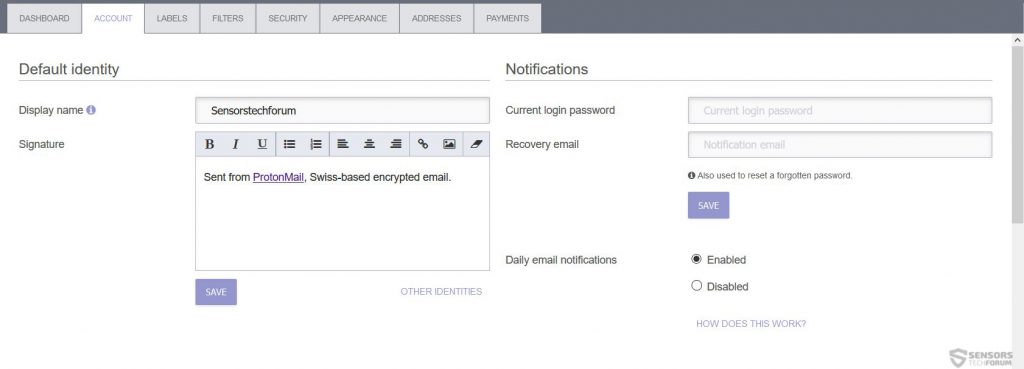
The provider also has the standard mail signature designing feature which can be modified extensively to be made unique:
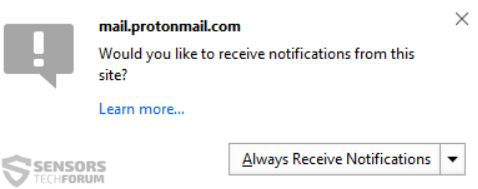
Next to it there is the ability to set browser notifications which appear even if your web browser is minimized:
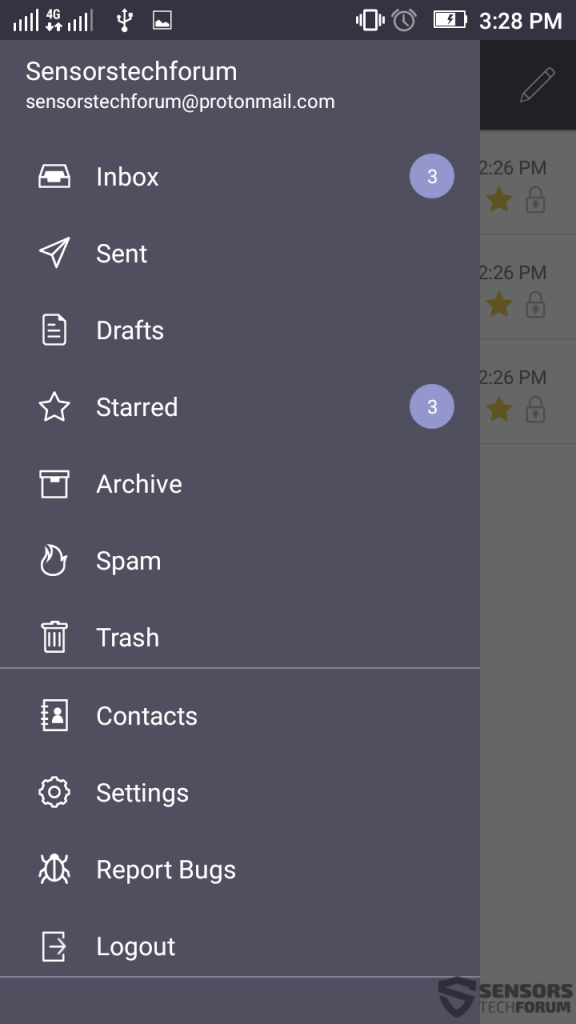
In addition to this, the application is quite widespread on different devices as well. It is also available as a mobile app for maximum comfort and mobile security as well:
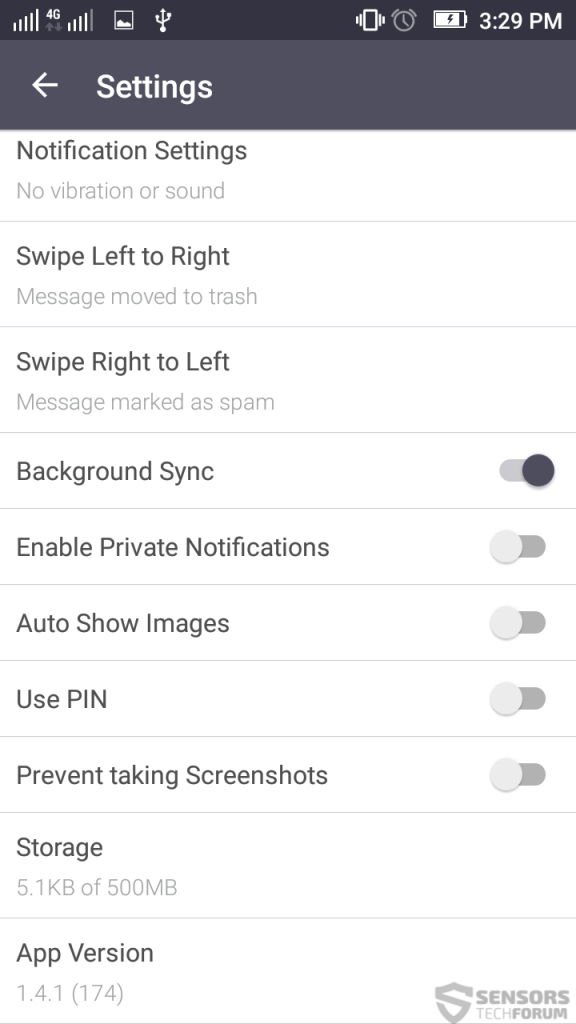
The mobile application of the provider has slightly different settings oriented towards the smartphone of the user:
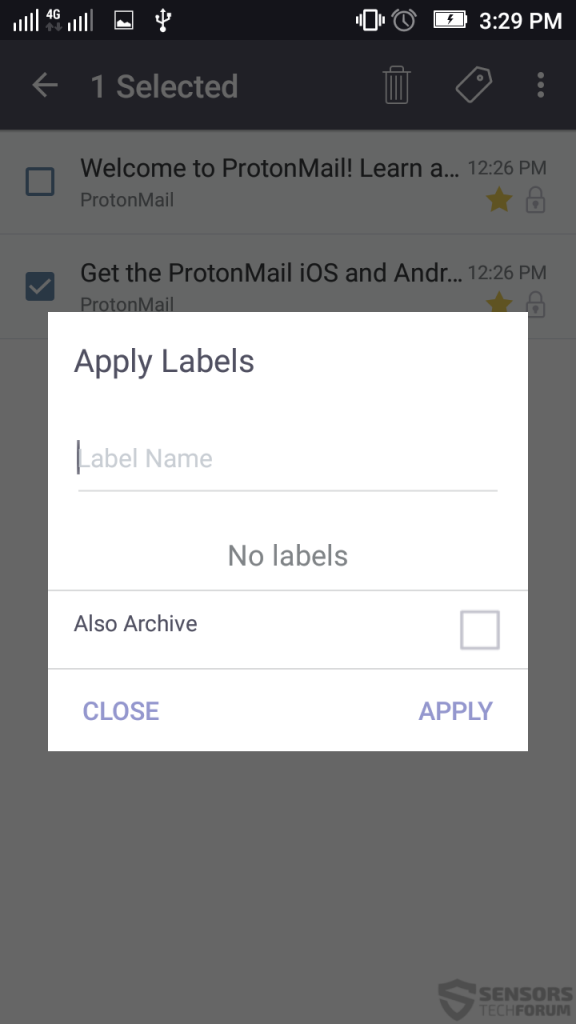
It also has labeling which allows you to label e-mails with custom labels, categorizing them based on your preferences.

What We Like
- Free 500.00 MB mail storage.
- You can send up to 150 encrypted messages per day.
- Simply designed interface which is very easy to work with.
- Security oriented interface.
- E-mail encryption with custom generated keys.

What Is Missing
- Annual price for the Visionary version is too high.
- Should have more authentication modes and preferences.

Conclusion
 As a bottom line, this is an e-mail provider strongly focused on privacy, by encrypting the mailbox of the user thus having two passwords. However, the e-mail account becomes useless once the device using it has been hacked, no matter how strong is its encryption. Information-stealing malware, like various types of Trojans, Keyloggers, Botnets may collect the password of the affected computer. This is why we recommend having an advanced anti-malware protection and following certain practices to help you and your data to stay as safe as possible, because when malware attacks your computer, these days it usually attacks a significant part of your life because everything is saved online today.
As a bottom line, this is an e-mail provider strongly focused on privacy, by encrypting the mailbox of the user thus having two passwords. However, the e-mail account becomes useless once the device using it has been hacked, no matter how strong is its encryption. Information-stealing malware, like various types of Trojans, Keyloggers, Botnets may collect the password of the affected computer. This is why we recommend having an advanced anti-malware protection and following certain practices to help you and your data to stay as safe as possible, because when malware attacks your computer, these days it usually attacks a significant part of your life because everything is saved online today.