What Is Triangulation iPhone Virus
The Triangulation iPhone Virus is a type of malicious software that specifically targets Apple devices, primarily iPhones. Its main purpose is to engage in harmful activities such as sending malicious messages, stealing personal information, and gaining unauthorized control over the infected device. This virus spreads through deceptive links and websites, and removing it can be quite challenging. To safeguard your device, it is crucial to exercise caution while browsing the web and implement preventive measures.
Triangulation Summary
| Name | Triangulation |
| Type | iOS and macOS Malware |
| Short Description | Designed to modify operating system settings in order to display scam notifications and inject malicious code into iOS devices. |
| Symptoms | The affected device starts displaying a “Injection Required” notification, leading to performance slowdowns and exposing the system to the risk of malware infections. |
| Distribution Method | Software Packages, Freeware, Shady Websites |
| Detection Tool |
Check if Your System Has Been Affected by Triangulation
Download
Malware Removal Tool
|
Triangulation iPhone Virus – Why Is It Present?
The Triangulation iPhone Virus is a form of malicious software specifically designed to infect iPhones with harmful code. It commonly manifests as pop-up ads and fake notifications while actively collecting personal data from the compromised device.
Triangulation iOS Virus – Functions and Impact
Triangulation represents an iOS virus capable of silently installing malicious software on a user’s device without their knowledge. This malicious software has the potential to extract sensitive data, send spam messages, and disrupt the normal operation of the infected device. Furthermore, it can serve as a medium to propagate other forms of malicious programs, thereby perpetuating a cycle of infection.
Subsequently, the virus may introduce victims to additional malware, leading to data collection and the execution of various undesirable activities.
Is Triangulation a Significant Threat?
Yes, Triangulation poses a severe threat. If your computer becomes infected due to this site’s dissemination of malicious advertising (malvertising), it can be held responsible for various malicious activities, including:
- Downloading additional viruses.
- Updating and controlling mining operations.
- Capturing screenshots.
- Stealing files.
- Logging keystrokes.
- Extracting data from your PC.
- Manipulating microphone and audio settings.
Is Triangulation Classified as a Virus?
Triangulation is categorized as an iPhone malware that distributes malicious code. This classification makes it not only highly dangerous but also considerably risky since it possesses the capability to infect your iPhone or iPad with various types of viruses.
Protecting Your iPhone from Viruses
To shield your iPhone from viruses, ensure that you keep your device’s software up to date and refrain from downloading suspicious apps or clicking on dubious links. It is also advisable to utilize reliable mobile antivirus software and exercise caution when connecting to unknown Wi-Fi networks.
Removing the Triangulation Virus from iOS
To eliminate the Triangulation virus from iOS, follow the steps in the guide below
By adhering to these instructions, you can successfully eradicate this threat from your device at no cost.
Preparation before removal of Triangulation.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Turn off your phone until you know how bad is the virus infection.
- Open these steps on another, safe device.
- Make sure to take out your SIM card, as the virus could corrupt it in some rare cases.
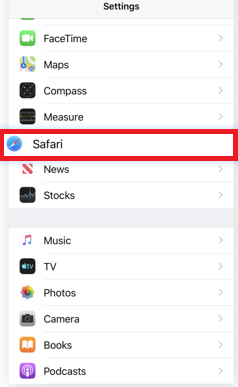
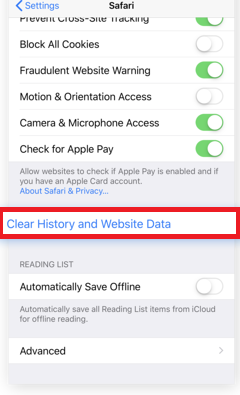
Step 1: Clear iPhone or iPad History and Data to remove settings changed byTriangulation

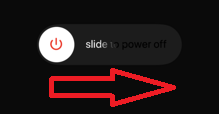
Step 2: Reset your iPhone to see if the suspicious behaviour is fixed and Triangulation stops infecting.
Step 3: Restore or Reset Your iPhone or iPad to removeTriangulation
If you have set up a backup on your iPhone or iPad, a good idea is to restore your device to an earlier time, when the virus was not present and the usage of your device was smooth and fast. Here is how to do it:


