
The Whiplr messenger has been found to utilize an insecure account verification procedure by requesting plain-text usernames and password combinations. This allows malicious users to easily hijack the information using various methods.
The Whiplr Messenger Uses an Insecure Account Verification Procedure: Avoid It to Stay Safe
The Whiplr messenger is a popular fetish dating application which has gained popularity among many mobile users. A security report however has found it to use an insecure account verification method which places all users at a significant privacy risk. The news broke out after a news site reported that registered users were asked to submit their account credentials (username, password and email address) in plain-text. A sample email message will read the following:
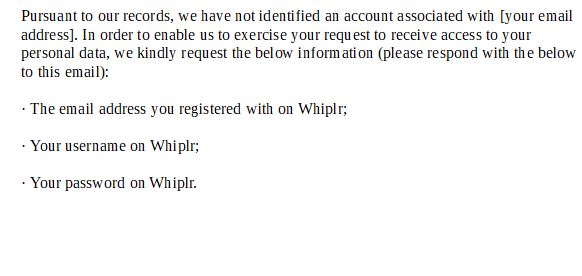
Pursuant to our records, we have not identified an account associated with [your email address]. In order to enable us to exercise your request to receive access to your personal data, we kindly request the below information (please respond with the below to this email):
· The email address you registered with on Whiplr;
· Your username on Whiplr;
· Your password on Whiplr.
This is a dangerous practice as it allows malicious users to obtain the credentials through various means. Whiplr themselves confirmed that they are storing the account credentials in plain text which means that upon launching a successful hacking attack on them the perpetrators of such crimes can hijack all user accounts.
Similar to other dating apps Whiplr allows the users to set up their own profiles including common elements such as photos, nickname, interests, age, hobbies and etc. As it is advertised as a used for adult dating stolen account credentials can be used for blackmail purposes.
There are several methods that the criminals may use in order to steal the account credentials:
- Man-in-the-Middle Attacks — By eavesdropping on network traffic the hackers may hijack the email messages contents and as a result the account information stolen.
- Virus & Trojan Horse Infections — By gettingg infected with malware that can transmit the victim’s activities to the hacker operators. This would also include email clients, browsers and the access to the app itself.
- Email Inbox Hack — If the criminals are able to intrude into the victim users email inbox then they can access the sent email messages.
The Whiplr data protection officer stated that the incident was an “error of judgment” in an isolated incident.


