Not only your personal computer and smartphone are prone to ransomware attacks. TrendMicro researchers just unveiled that your Android TV is also exposed to the risk of being locked and becoming unusable until a ransom is paid.
The threat, dubbed FLocker (initially detected as ANDROIDOS_FLOCKER.A and short for Frantic Locker) has been around since May 2015. However, one version of several thousand variants has now been updated to attack smart TVs.
More Android Malware to Keep Away from
How Does FLocker’s Android Smart TV Version Infect Devices?
TrendMicro’s research doesn’t exactly indicate how a smart TV would be attacked. However, it’s highly likely that the attack is triggered by SMS or malicious links.
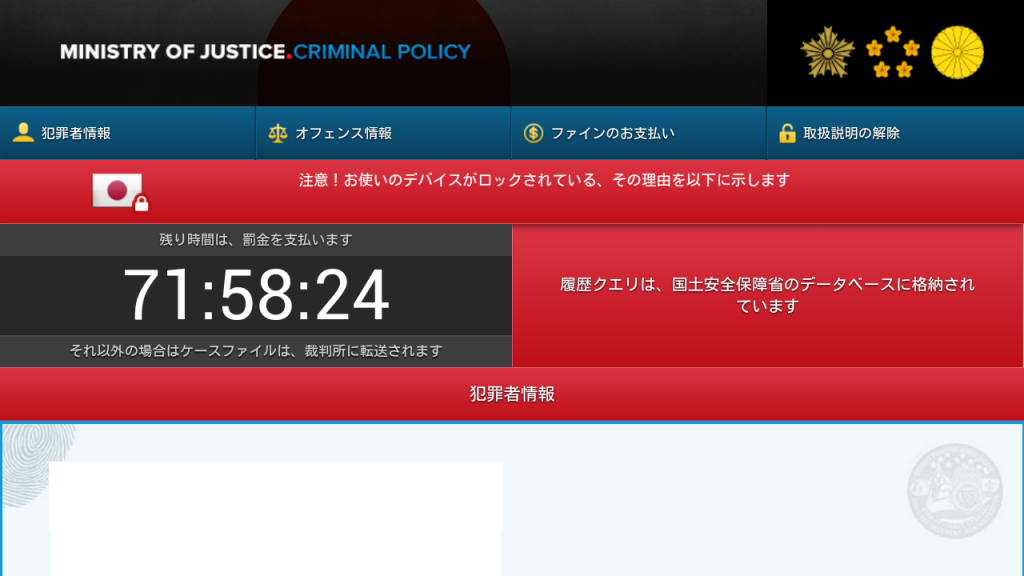
As with other screen lockers, FLocker will lock the screen of the targeted device and will display a ransom message written in the local language. The message would be from US Cyber Police or another similar institution.
The ransomware demanded by FLocker is not in Bitcoins but in… iTunes gift cards. The ransomware operators want to receive $200 in gift cards to unlock the device. In fact, the ransomware’s actions match those of smartphone lockers.
A curious fact is that the threat will not attack devices located in any of these countries: Kazakhstan, Azerbaijan, Bulgaria, Georgia, Hungary, Ukraine, Russia, Armenia, and Belarus. Moreover, if FLocker gets installed on a device in any of these regions, it will “stand still” for 30 minutes and then will request device admin privileges. If the request is rejected, the threat will display a fake system update screen.
Even though FLocker locks the screen of the devices, it will not encrypt any files. Nonetheless, it will harvest information from (and about) the device.
How to Remove FLocker from Affected Devices
Tech-savvy users can uninstall the ransomware but not before they remove its device admin privileges.
TrendMicro’s piece of advice:
We suggest user to contact the device vendor for solution first if their Android TV gets infected. Another way of removing the malware is possible if the user can enable ADB debugging. Users can connect their device with a PC and launch the ADB shell and execute the command “PM clear %pkg%”. This kills the ransomware process and unlocks the screen. Users can then deactivate the device admin privilege granted to the application and uninstall the app.


