Remove Raw6help.xyz Scam (1-888-345-8305)
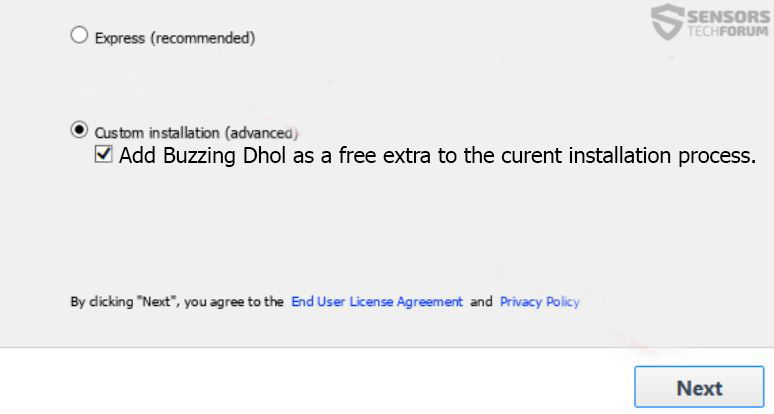
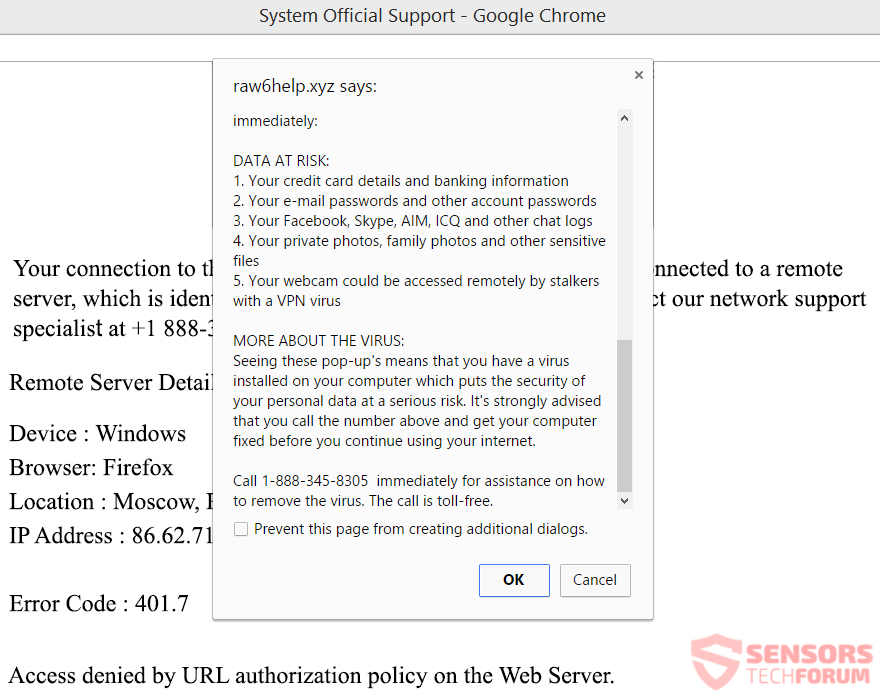
Raw6help.xyz is a website that is directly involved with a tech support scam. The site uses 1-888-345-8305 for the contact phone number. People that run this scam might call you from that number. You can experience endless redirects while browsing…