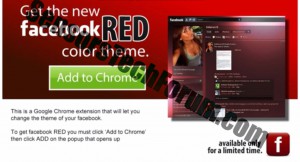
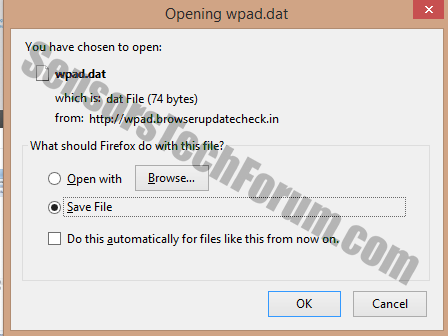
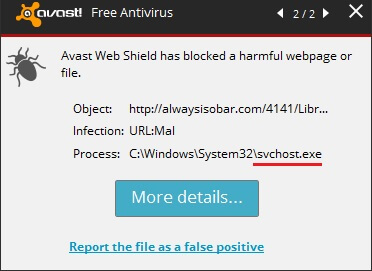
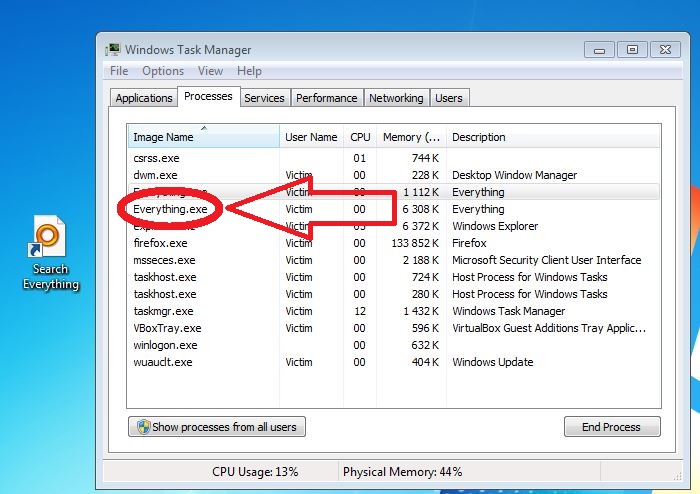
Identify and Remove Backdoor:Win32/Chaapt.A
Backdoor:Win32/Chaapt.A has been detected as a Trojan horse with backdoor capabilities. This means that it can connect to a Control&Command server and allow cyber criminals perform a range of malicious operations. Furthermore, once it is inside the system, Backdoor:Win32/Chaapt.A will…