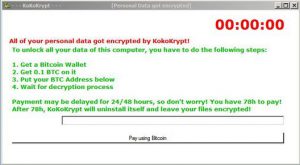
Remove iLock Ransomware and Restore AES-256 Encypted Files
This article aims to help you remove iLock ransomware virus from your PC and hopefully restore some of your encrypted files. The iLock ransomware, previously spotted in 2016 has returned with a new version. Being one of the first ransomware…



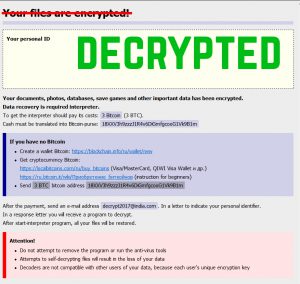
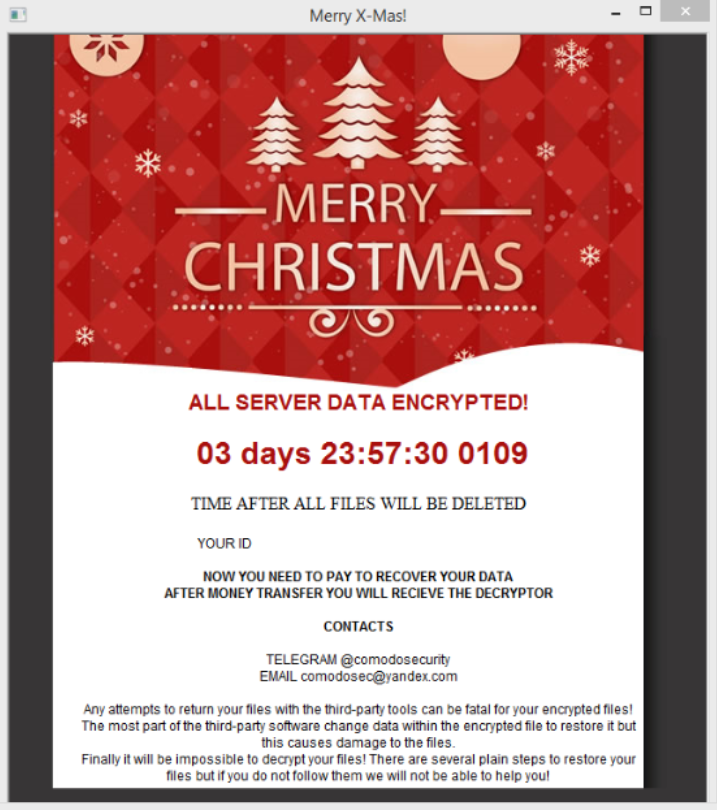
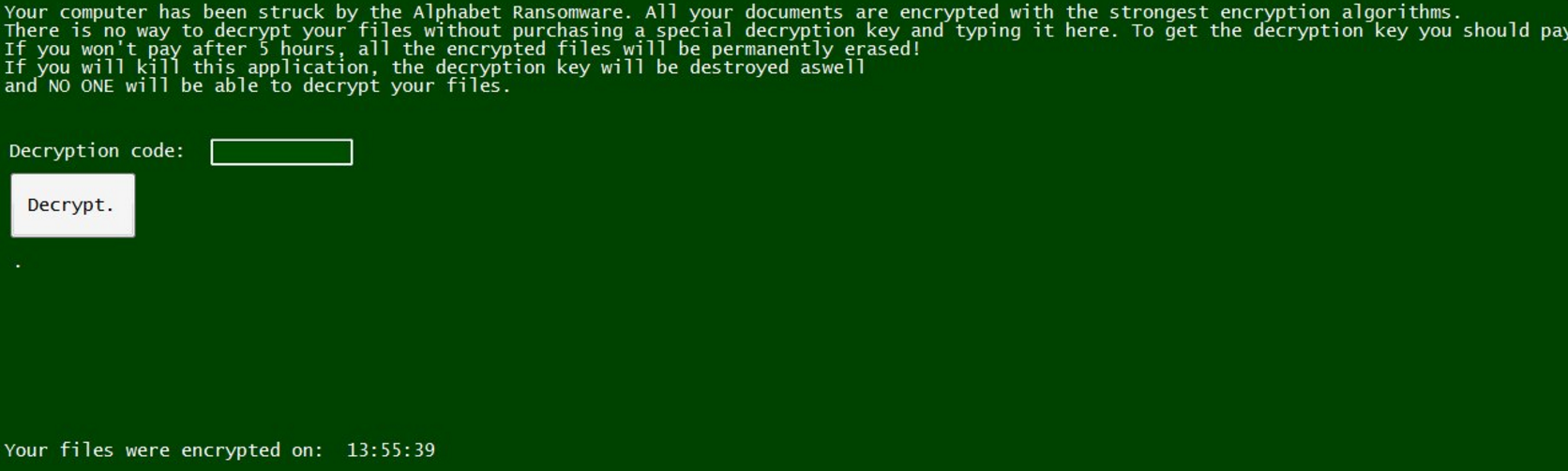


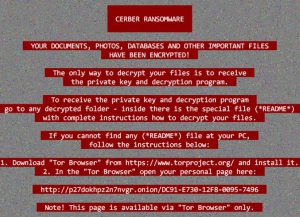
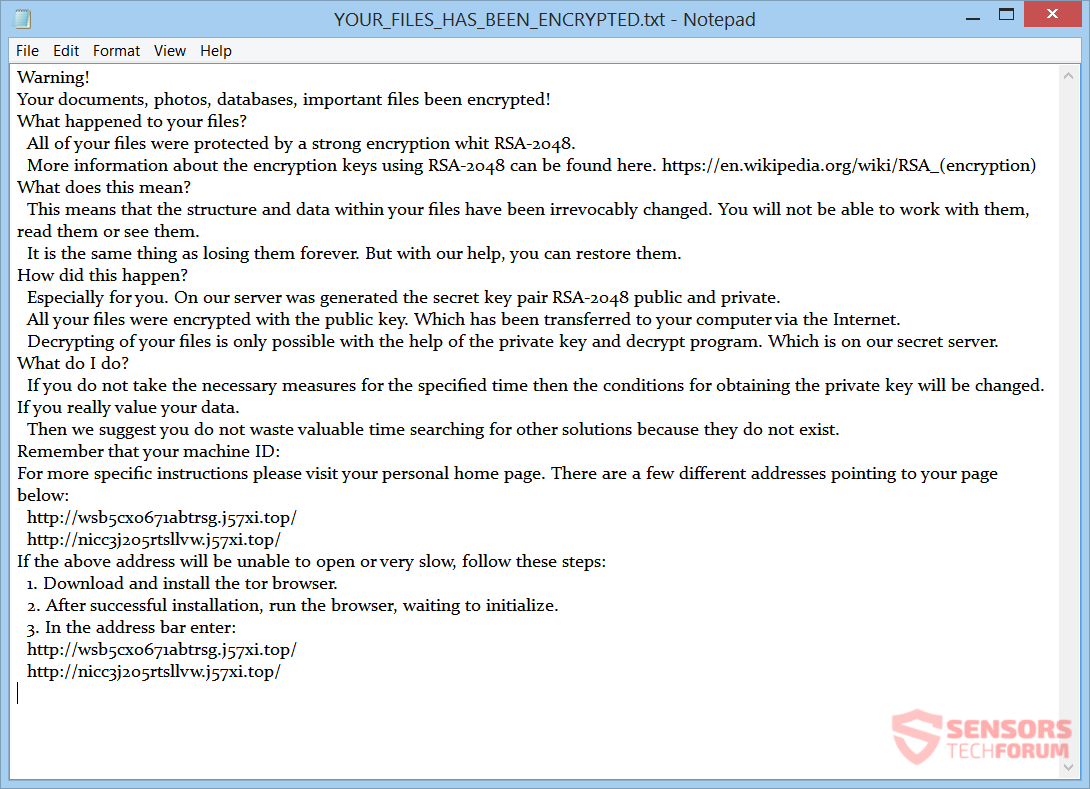

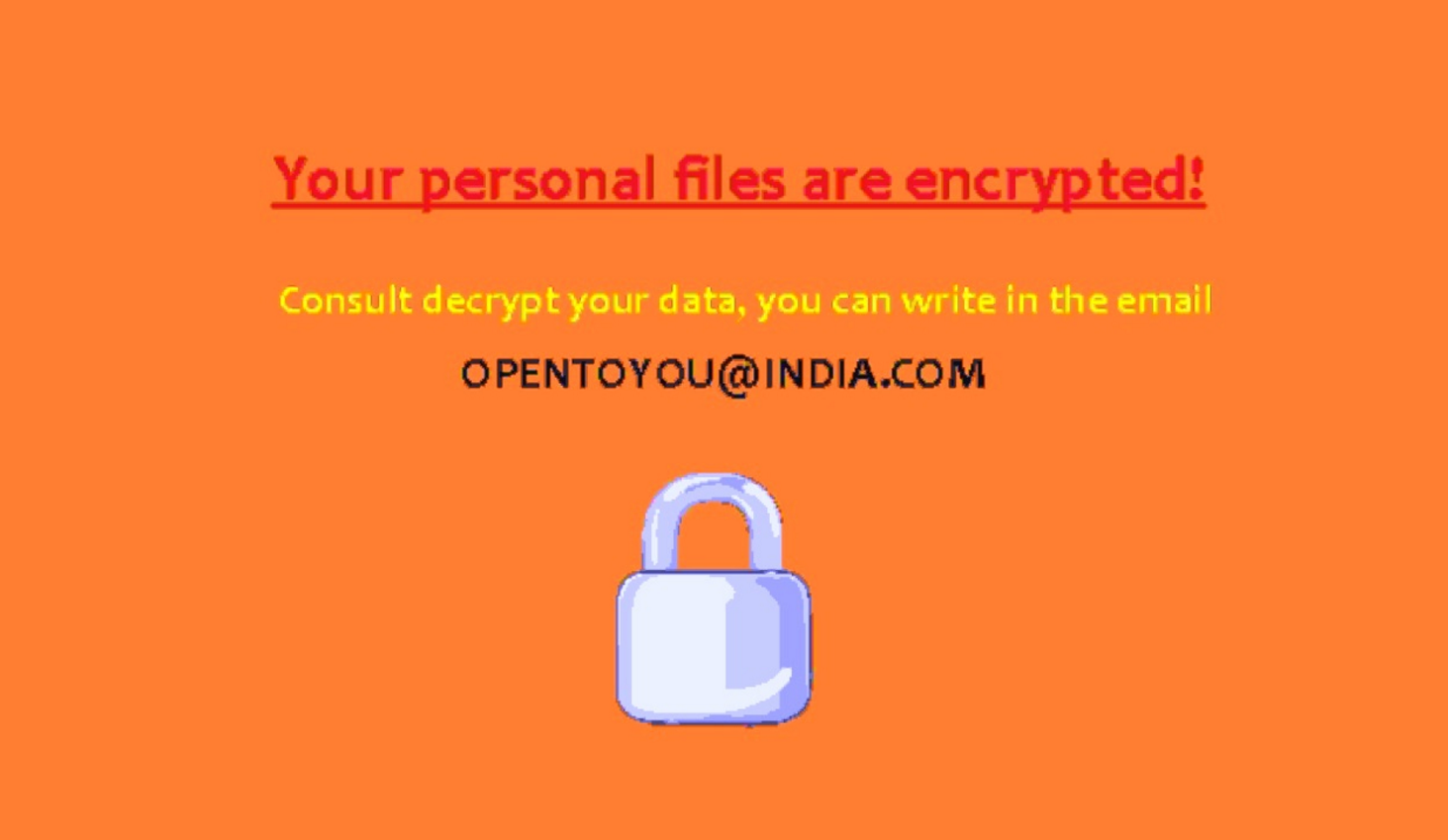

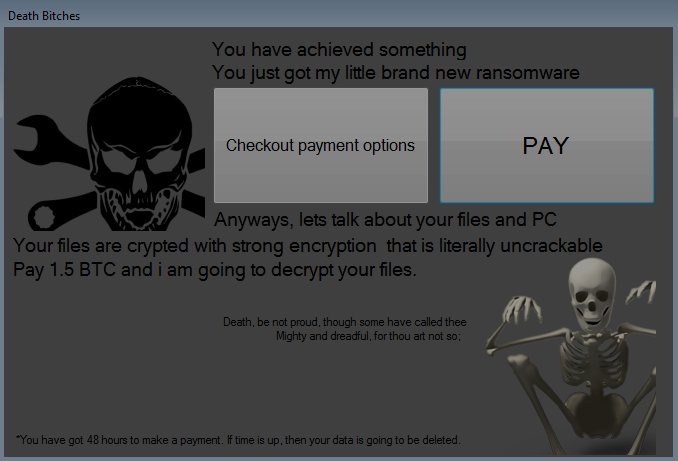
![Dharma Ransomware Using New File Extension [Mkgoro@india.com].xtbl and [Mkgoro@india.com].wallet New Dharma ransom note](https://cdn.sensorstechforum.com/wp-content/uploads/2016/12/Screen-Shot-2016-12-30-at-1.19.57-PM-150x150.png)