Remove Strictor (BankAccountSummary) Ransomware and Restore .locked Files
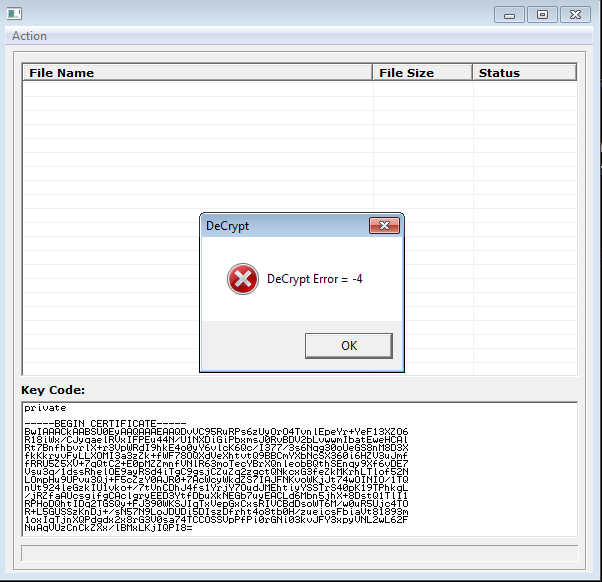
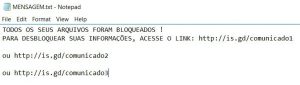
The “hidden tear” project has brought yet another ransomware. It is named Strictor and it is also known as BankAccountSummary ransomware which wants 500$ from infected users to get the files encrypted by it back at their disposal. The ransomware…