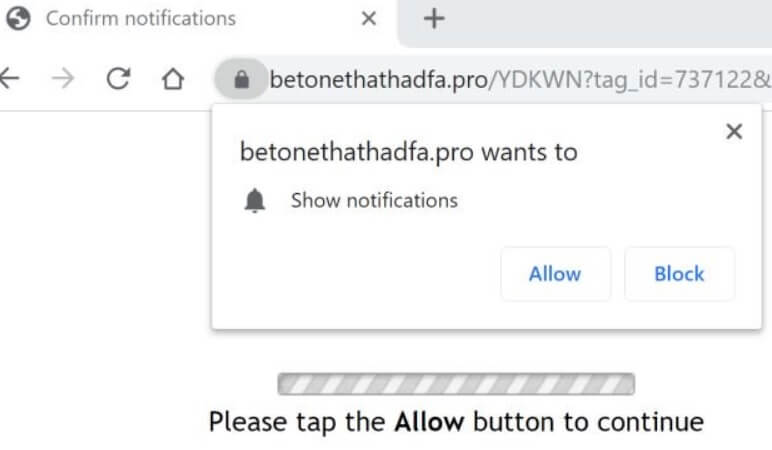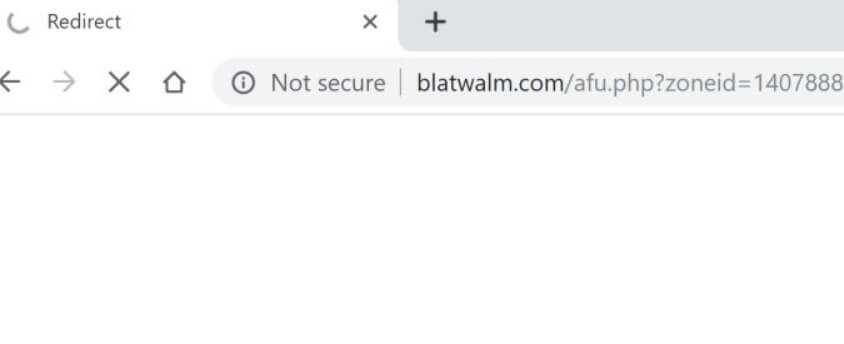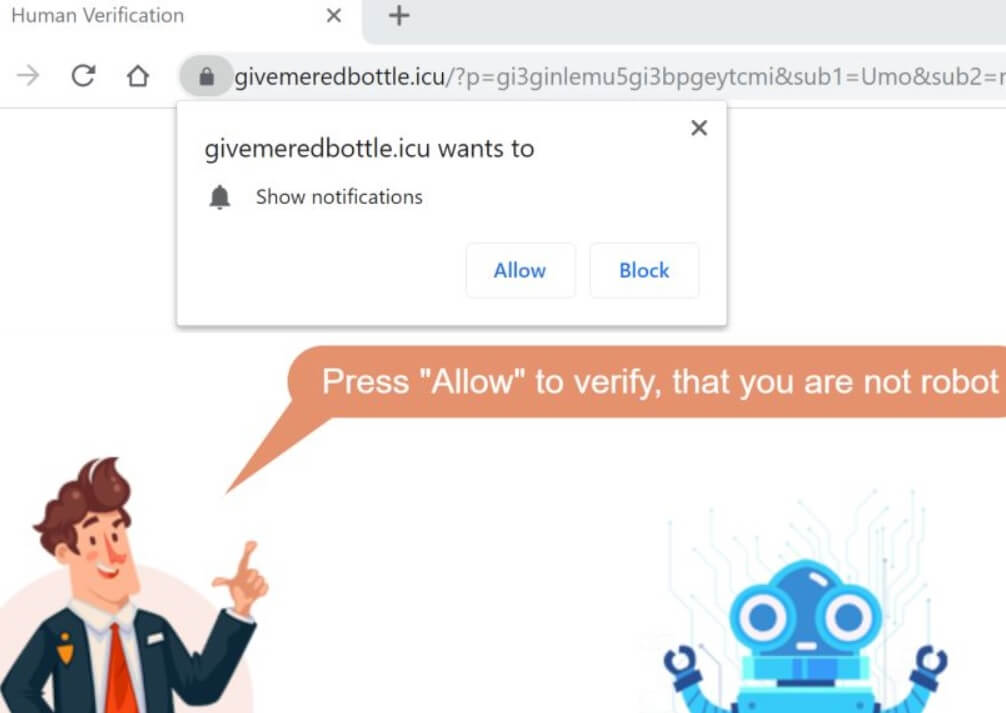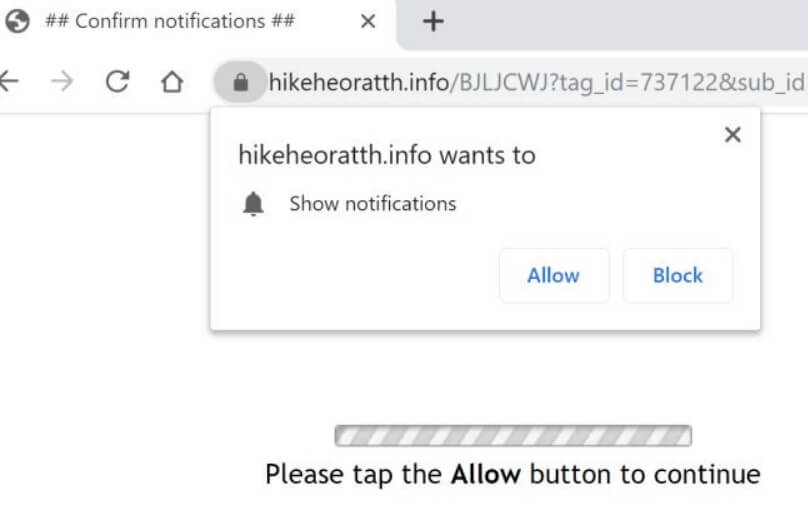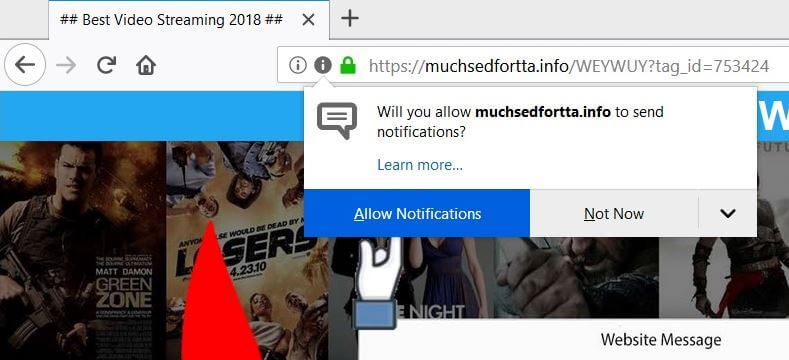
Remove TestForSpeed.com Hijacker (Update July 2019)
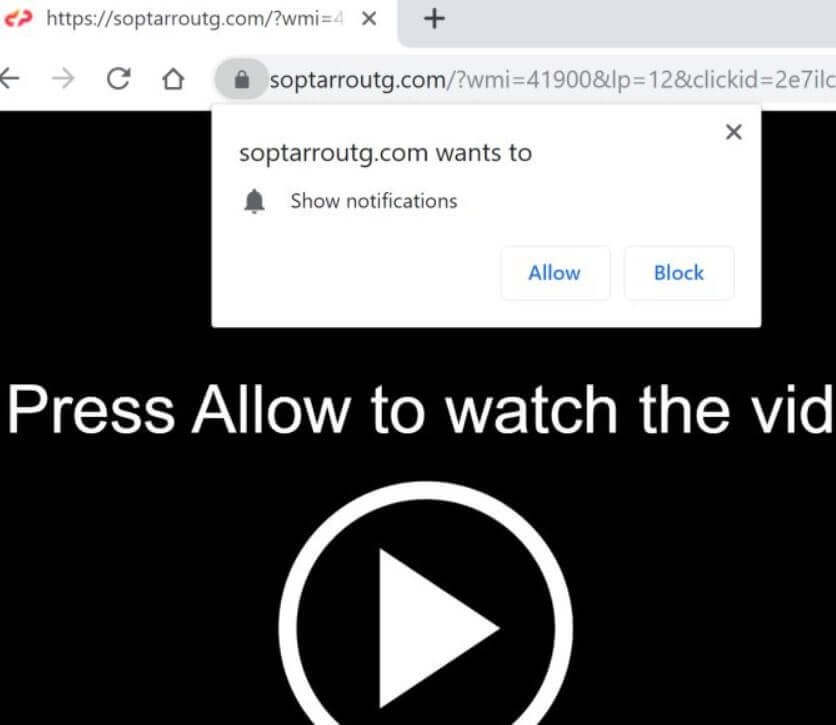
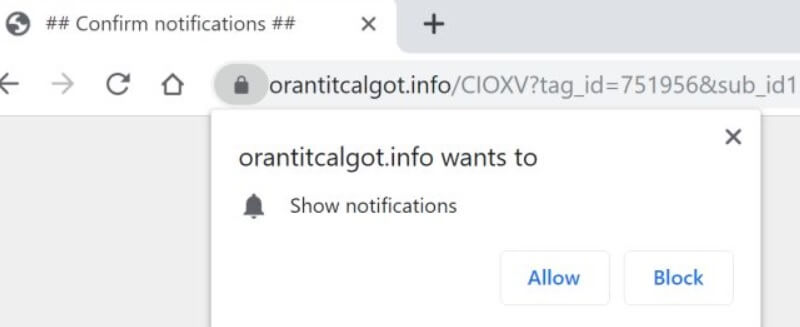
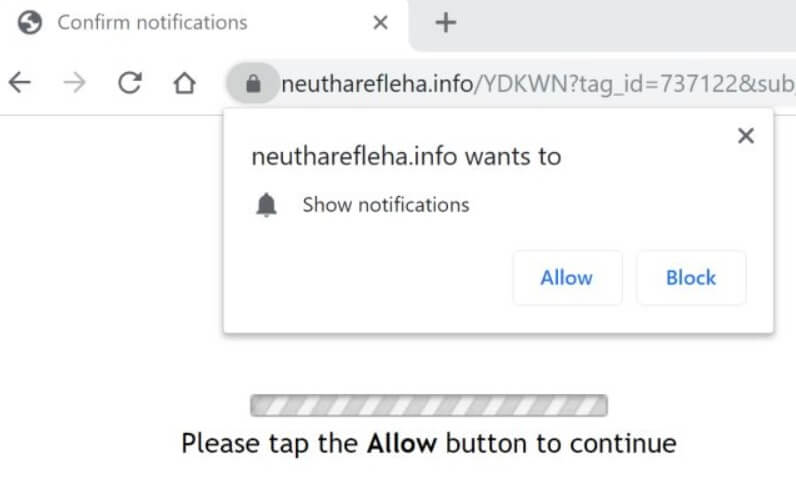
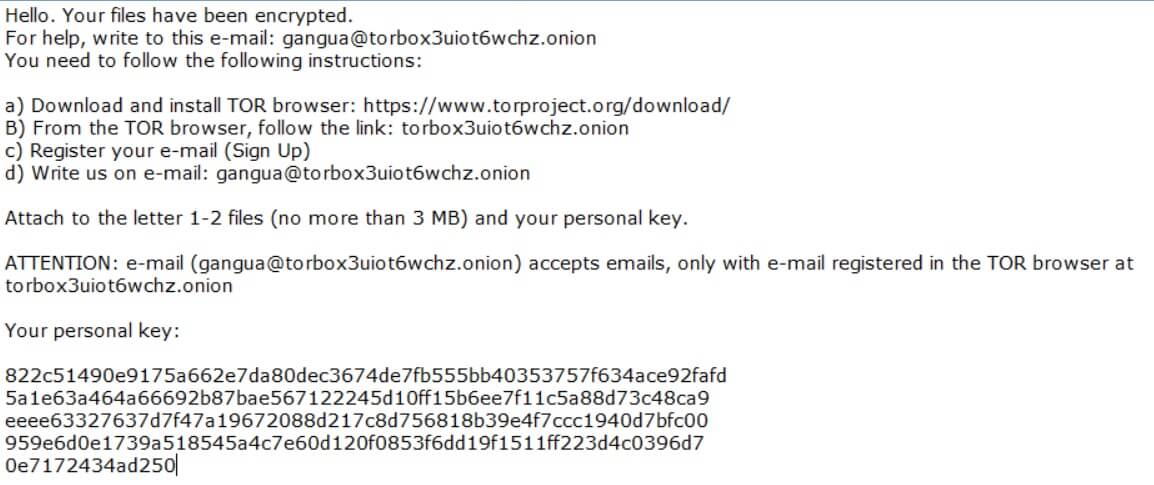
TestForSpeed.com is the official website of the browser hijacker TestForSpeed. Mindspark Interactive Network (now Ask Applications) developed this hijacker few years ago, and it seems to be affecting users in 2019 as well. Read the article carefully to know how…