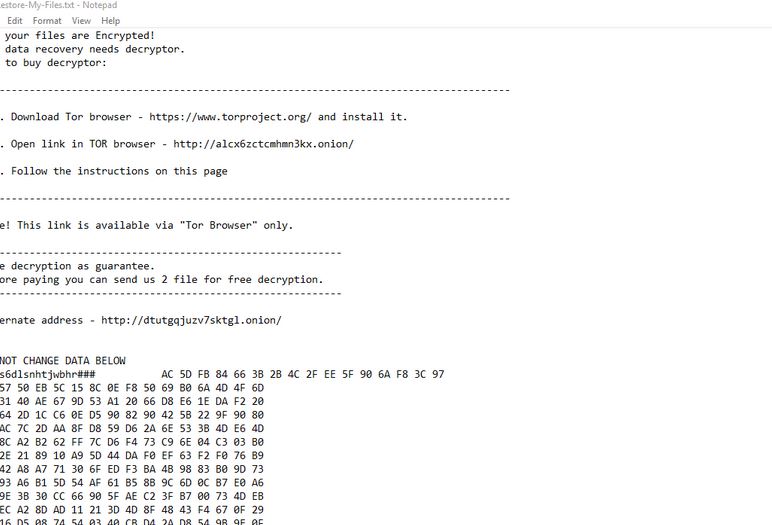
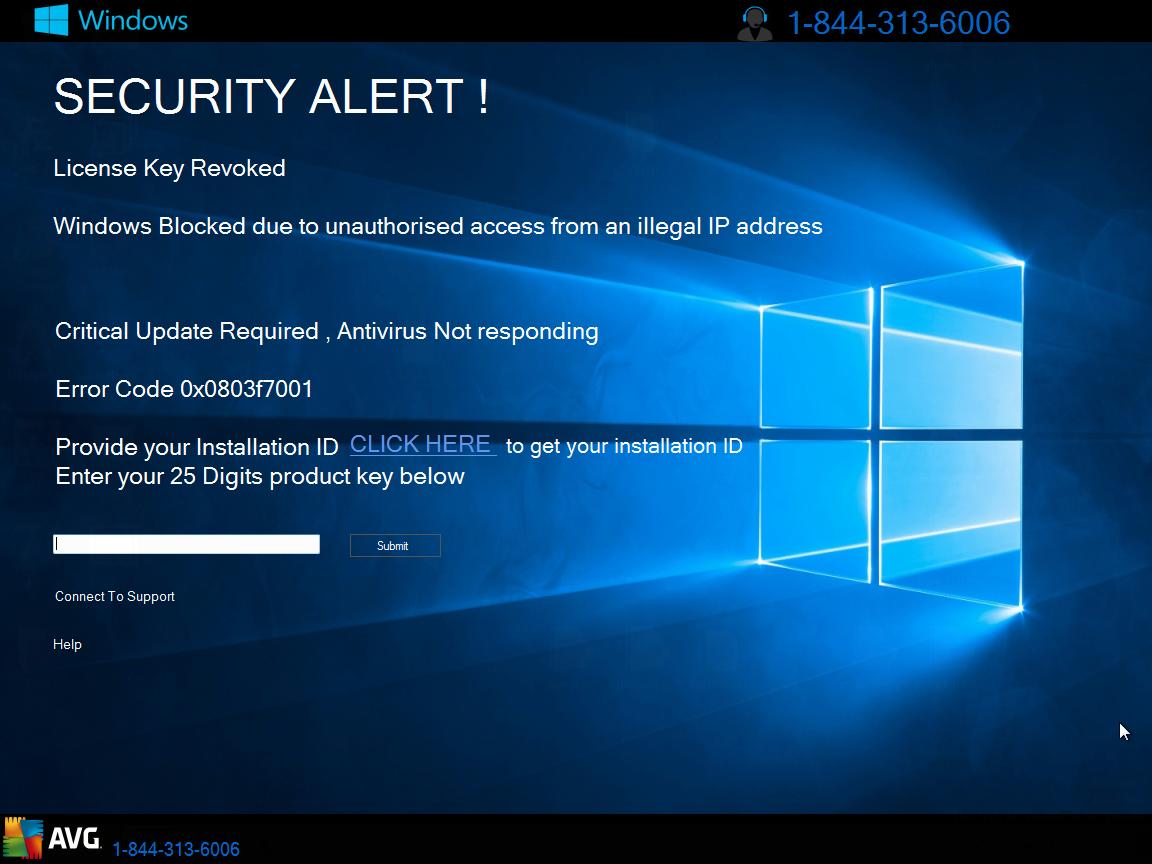
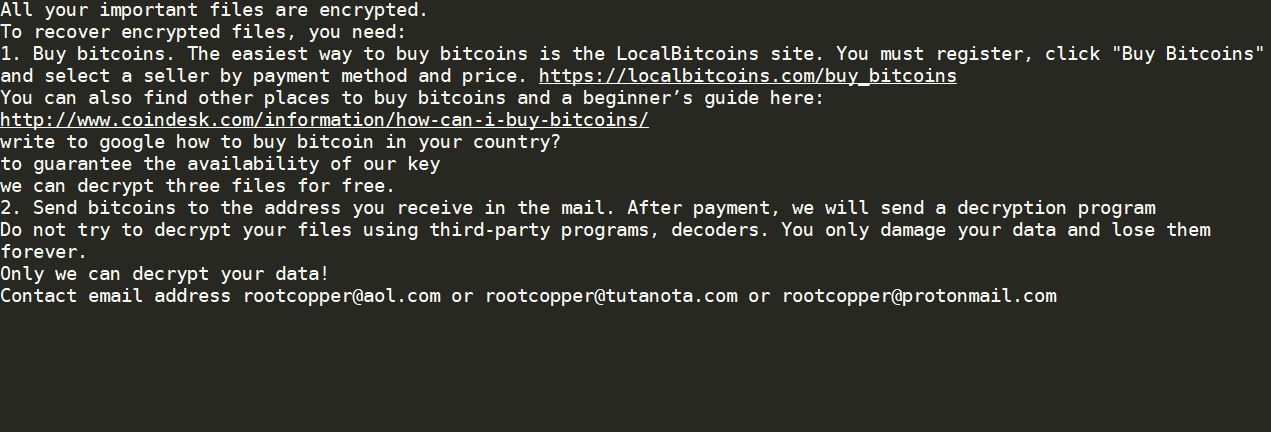
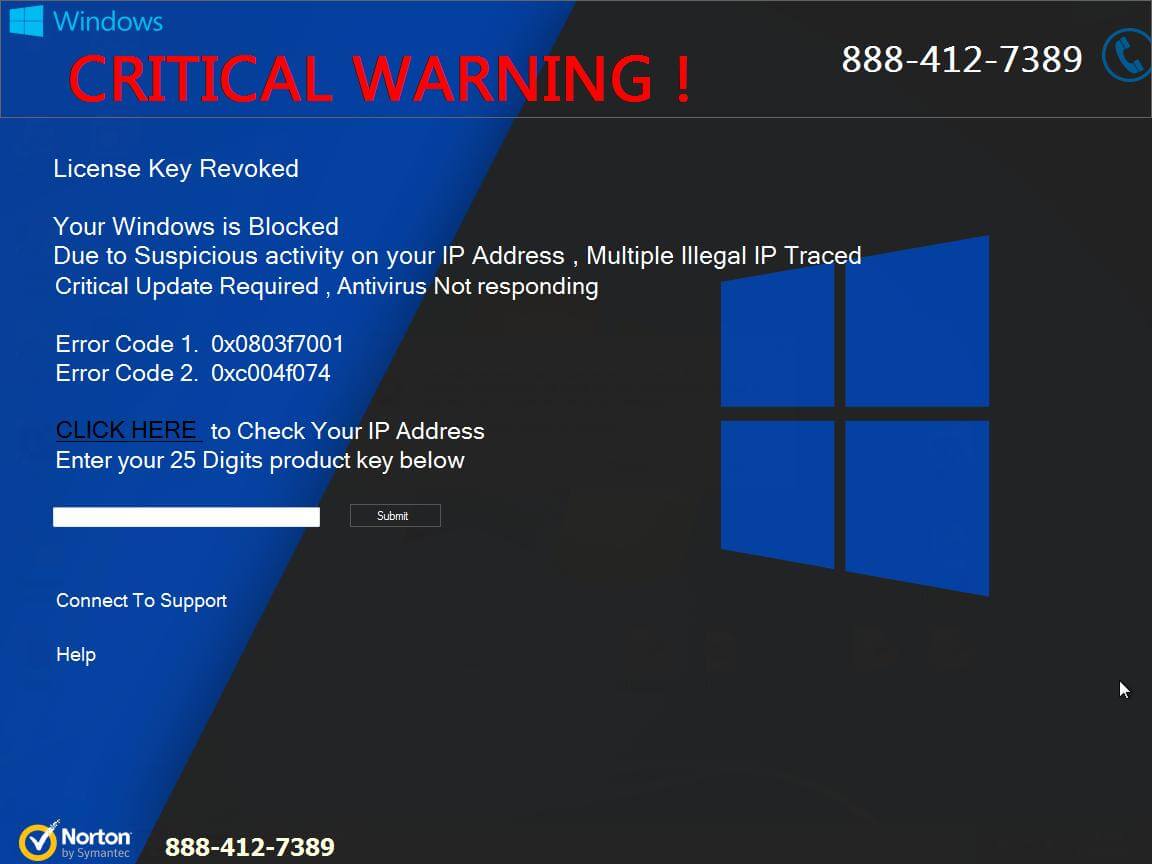
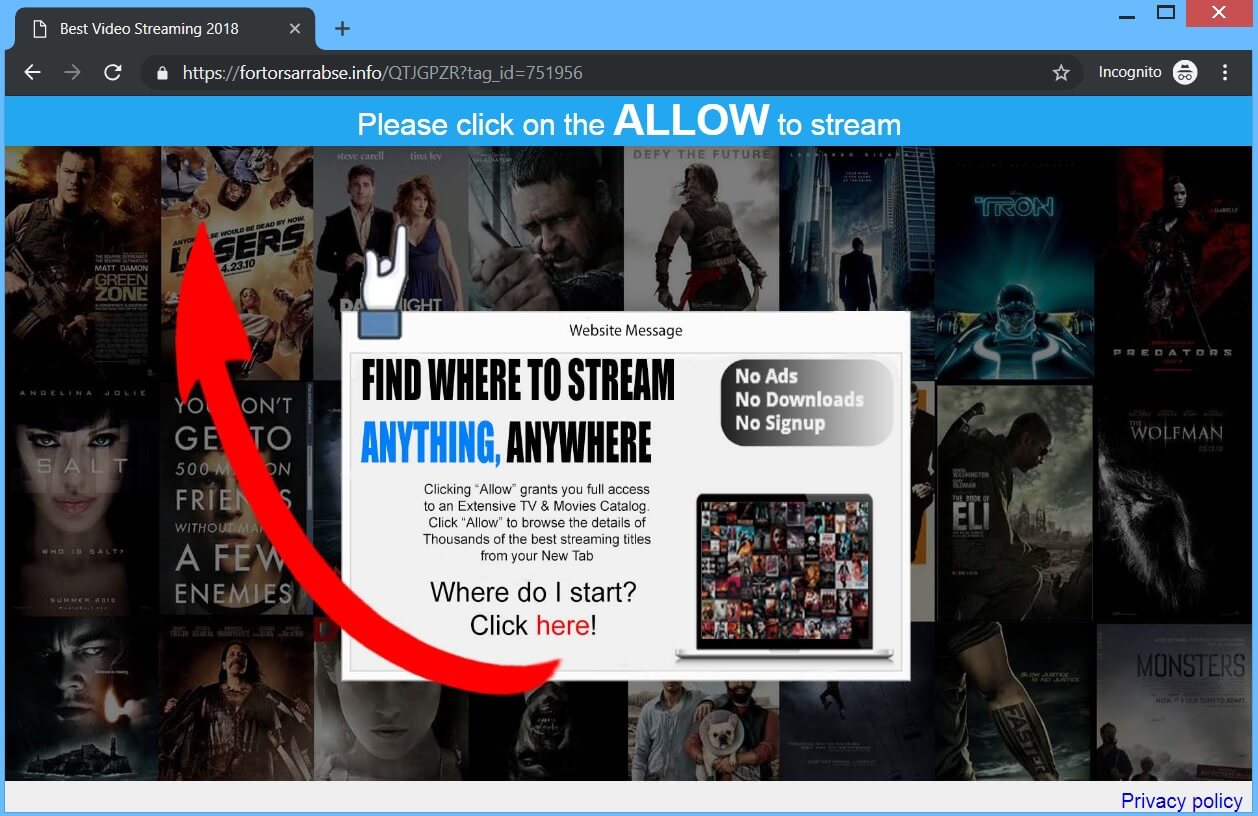
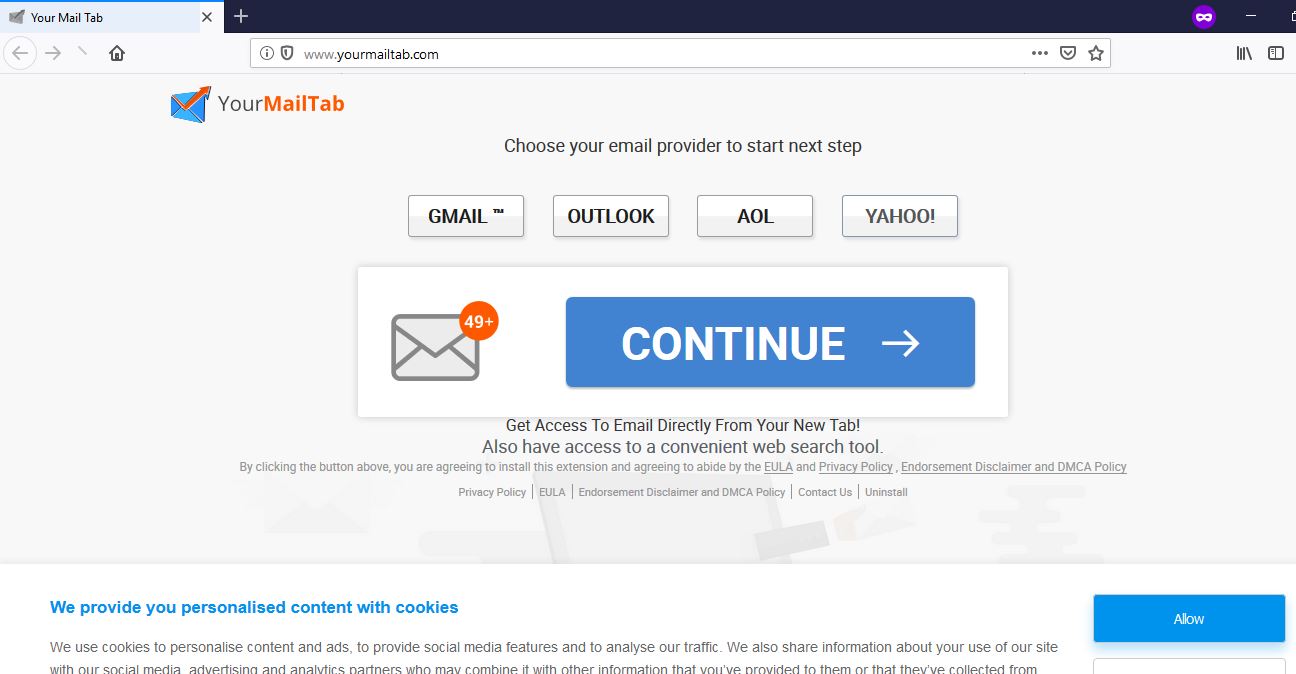
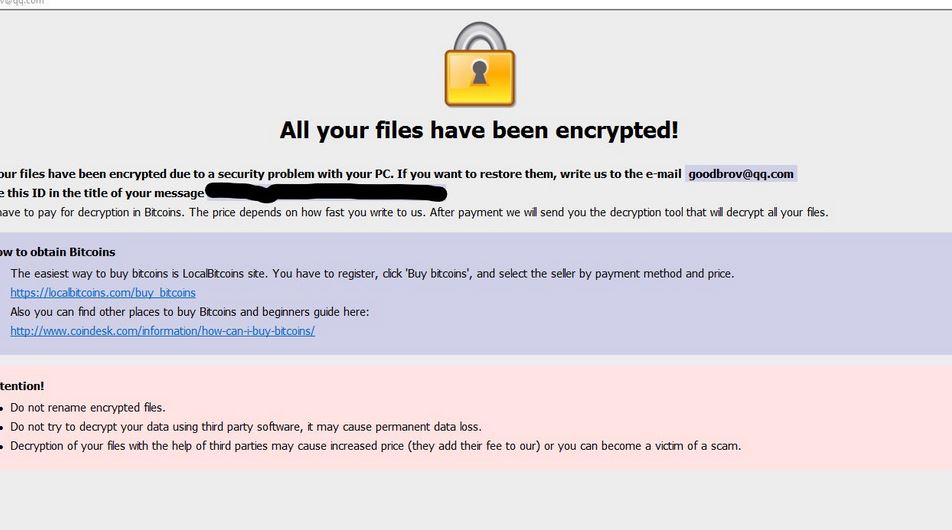
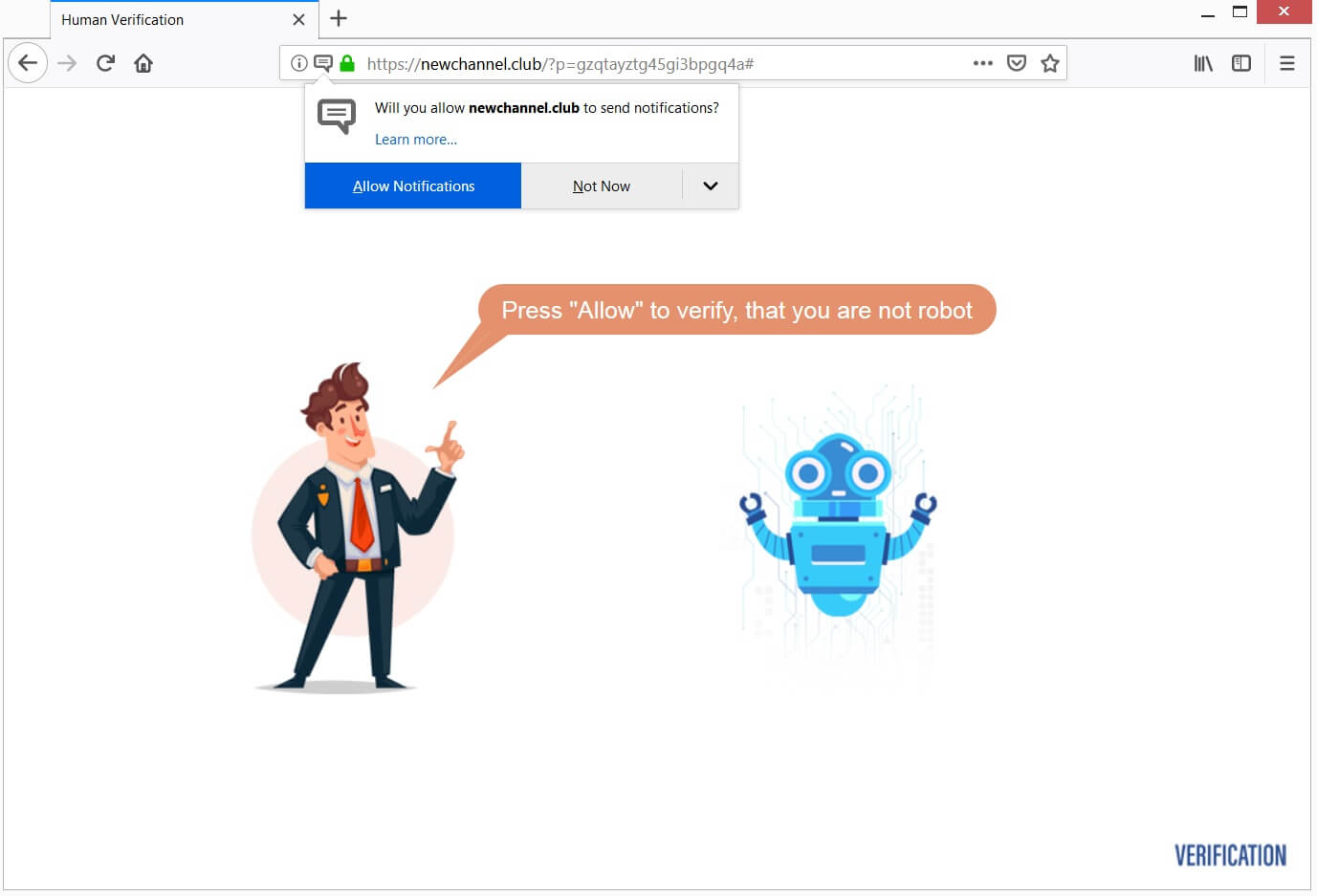
Remove Search.terraarcade.com Browser Hijacker
What is Search.terraarcade.com? Does Search.terraarcade.com show ads? Does Search.terraarcade.com redirect you? Search.terraarcade.com is the main page that will show up when you open a new tab page if you have the related browser hijacker redirect installed on your computer machine.…