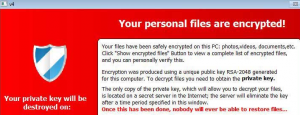
 TeslaCrypt ransomware has turned many users into victims. However, this ransomware story may be coming to its foreseeable end. According to an ESET researcher, the vicious file-encryption operation is now shut down. A free decryption key is available to anyone who wants to unlock their files.
TeslaCrypt ransomware has turned many users into victims. However, this ransomware story may be coming to its foreseeable end. According to an ESET researcher, the vicious file-encryption operation is now shut down. A free decryption key is available to anyone who wants to unlock their files.
TeslaCrypt Operators Make Master Decryption Key Public
The researcher says he made contact with the virus operators via the support channel on their website hosted on the Dark Web. The threat actors said they were shutting down TeslaCrypt. They even agreed to offer a master decryption key for victims.
The decryption key has been posted on the Dark Web page which was available for victims’ payments. The following message is attached to it:
Project closed. Master key for decrypt [KEY] Wait for other people make universal decrypt software. We are sorry!
Luckily, the master decryption key is suitable with TeslaCrypt version 3 and 4. Those versions are known to append a secondary file extension to encrypted files – .xxx, .ttt, .micro, .mp3.
For more information, visit our security forums
More about ESET TeslaCrypt Decrypter
Even though the master decryption key has been made public, ESET has already created a TeslaCrypt Decrypter.
Furthermore, BloodyDolly’s TeslaDecoder has also been upgraded to work with the decryption master key. According to multiple security researchers, TeslaCrypt’s infections have started to fade away. The intensity of spam campaigns spreading the virus has declined, too.
One logical question to be asked here is what led to the diminishment of the threat. It’s simple – the ransomware operators switched to developing another ransomware. CryptXXX.
From TeslaCrypt to CryptXXX
According to BC’s Lawrence Abrams, the cybercriminal group has shifted to CryptXXX. As to why – CryptXXX may have appeared to be the more profitable ransomware strain to “nurture”. However, it’s already been cracked by Kaspersky not once but twice (CryptXXX 1.0 and CryptXXX 2.0).
Here’s how to remove CryptXXX
In addition, white hats have been continuously working towards the breakdown of multiple ransomware families, such as Locky, which was recently “hacked” to distribute antivirus files instead of ransomware.
If the end is near for TeslaCrypt, CryptXXX, and Locky, what could be next?


