As we all know and are aware, most phishing hacker attacks are being performed by automated bot machines instead of living humans. A statistics in a recent study on the subject Google released shows that the so-called ‘manual hijacking‘ might be more successful for hackers than the automated one though.
The detailed results of the research on these manual attacks can be found in Google’s report and show that never mind it takes much more efforts to profile the victims and perform for hackers, nine of one million phishing attacks per day are manual.
‘Manual Hijacking’ an Ordinary Job?
It looks like these manual attacks might be just an ordinary every-day job for some people. Google researchers found that the attacks start approximately in the same time during the day, notch up a drop around noon and end at approximately the same time of the day. They are not very active during weekends as well.
Here’s what is observed by the researchers:
- The individuals seemed to work according to a tight daily schedule. They started around the same time every day and had a synchronized, one-hour lunch break. They were largely inactive over the weekends.
- All individuals followed the same daily timetable, defining when to process the newly gathered password lists, and how to divide time between ongoing scams and new victims.
- They were operating from different IPs, on different victims, and in parallel with each other, but the tools and utilities they used were the same. They also shared certain resources such as phone numbers.
Moreover, even if they have different IP addresses (which can be due to proxy servers or VPN networks actually) they use the same tools, even some shared recourses like phone numbers. Google tried to locate the hackers by IP addresses and noticed that most of them seem to be located in China and Malaysia but based on the above these results might be controversial.
On the other hand, tracking of the phone numbers showed that two major groups might be doing the phishing – one in Nigeria and one on the Ivory Coast. Based on the most spread language for each country it seems that the Nigeria group is focused on English-speaking countries, while the Ivory Coast – on French-speaking ones.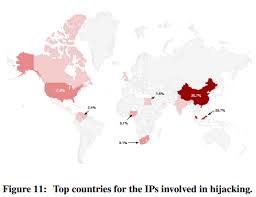
Great Challenge for the Researchers
Unfortunately still, the ‘manual hijacking’ is very hard to identify as the volume of these attacks is very small, and the crooks vary.
‘In our experience the greatest challenges in detecting manual hijacking is that it is extremely low volume, that hijackers are very versatile, and that it is difficult to strike the right balance between false positives (challenging legitimate users) and false negative (letting a hijacker in) when it come to’Google researchers write.
They also advise that the most efficient way of protecting the data remains the 2-step verification process introduced by Google. ‘SMS verification, which has an over 80% success rate, is the most reliable recovery option for multiple reasons. First, users tend to keep their phone number up-to-date, which make non-existent phone numbers a non-issue. Secondly, it provides a very good user experience. Users find it easy to type in the code they receive via SMS. Finally, it is hard to fake’, they think.

