A relatively new research recently uncovered that there is a hidden patch gap in Android devices. Researchers spent two years analyzing 1,200 Android phones and presenting the results during the Hack in the Box conference in Amsterdam. Now, new research has added more trouble to the Android ecosystem.
Apparently, a total of 274 flaws were detected among the top 50 Android mobile shopping apps. All of them contained security risks. The research is serious proof of Android weak security – the apps were tested across 34 security testing categories.

Related Story: Check Your Phone: Researchers Find Hidden Patch Gap in Android
More about the Research
Security researchers from Appknox and SEWORKS just published the results of their joint efforts focused on assessing the security of the top 50 Android shopping apps on Google Play. Their report is titled “Security Status in m-commerce”. It revealed that at least 84% of these shopping apps have at least three high-level security vulnerabilities.
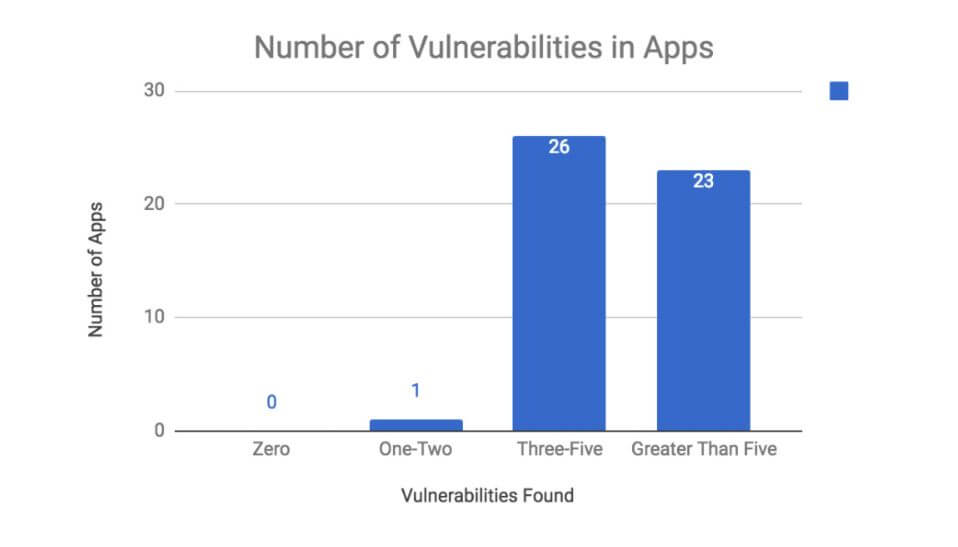
More particularly, among the 50 apps, the researchers analyzed, there is no app that does not have security risks. 49 apps have at least three or more security vulnerabilities, while 28% have critical security issues, and 84% have three or more high-level issues. Given the popularity of the apps, the results are concerning, the report notes.
How Were the Apps Tested?
The research team used the Common Vulnerability Scoring System (CVSSv3.0) to rate vulnerabilities. CVSS is the industry standard for assessing the severity of computer system security vulnerabilities. CVSS assigns severity scores that enables experts to prioritize responses according to the particular threat.
The metrics that are deployed for the assessment of security risks are the following:
- Attack vector;
- Attack complexity;
- Required privileges;
- User interaction;
- Scope;
- Confidentiality impact;
- Integrity impact;
- Availability impact.
What is mostly concerning is that almost all of the apps, or 94% of them, were affected with unprotected export receivers. What does mean? Android apps export receivers, which respond to external broadcast announcements and communicate with other apps, the report explains. For example, when Receivers are unprotected hackers can modify the apps’ behavior to their likings, and also insert data that doesn’t belong to the apps.
Furthermore, 64% of the apps were affected with “App Extending WebView Client.” What does this mean? When WebView Clients are not correctly protected in-app extensions, hackers can trick users into inputting sensitive personal information in fake or copied apps, which typically results in loss of user data, damages, and SSL compromises.
Related Story: Over 700,000 Malicious Apps Removed from Google Play in 2017
To avoid any security risks, app developers should follow the security researchers’ advices:
- Developers should stay compliant with industry standards;
- Developers should implement security into the development cycle;
- Automated mobile app security testing should be implemented;
- Manual assessment should be done regularly;
- Developers should strategize with mobile app security experts.
For further details, you can download the report.


