How safe are my credit card data and credentials? Because cyber crooks are continually working towards improving their methods, this is a question that deserves addressing on a daily basis.
New Scam Combines Phishing and Infection of Legitimate Pages to Steal Credit Card Details
A new research by security firm Sucuri proves that online users should be both worried and alert when it comes to their login and credit card details. The team has uncovered a new scamming tactic that mixes the established method of compromising e-commerce checkout pages and the employment of phishing sites.
The employment of phishing pages that imitate either the login or the checkout page of PayPal and other payment and e-commerce services has been known to researchers for a substantial amount of time. As has been the injection of malicious code into e-commerce portals to capture the victim’s credit card details.
Related: Vishing, Smishing and Phishing Are after Your Information and Money
This is perhaps the first time when phishing and infection of legitimate pages are employed together. Phishers didn’t infect legitimate pages, they used emails and fake websites, Sucuri notes.
The firm has observed attacks where crooks are using malicious JavaScript on e-commerce websites with the purpose to redirect the potential victim to a bad checkout page.
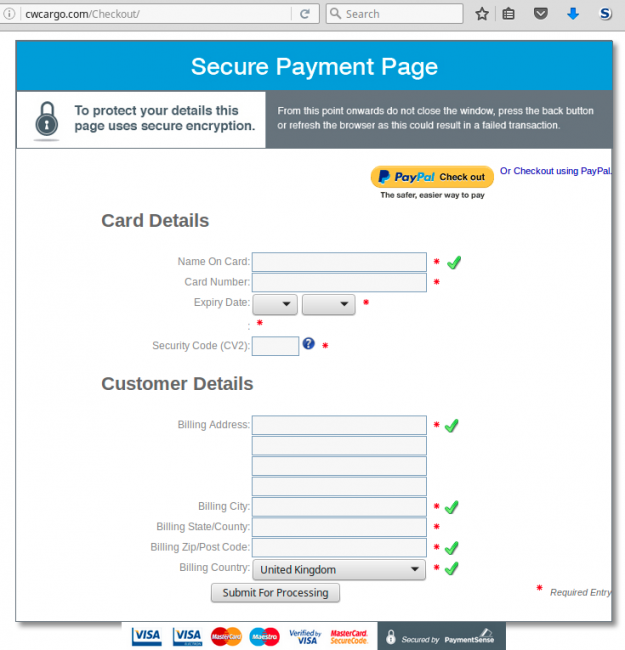
Here’s how it works. When a customer is ready to pay for selected products they open a site’s “checkout” page, but instead of the site’s own checkout page, they end up on a checkout page on a third party site.
As visible, the page above looks like nothing out of the ordinary. If the user is not paying attention and doesn’t look at the address bar, they will not notice on what page they’re about to type in their banking details. This method may be even more successful than the average phishing scam because the victim is just about to shop and enter their credit card number, personal and billing information. The result is bad for both the shopper and the site owner – the victim loses their credit card credentials and the e-commerce site owner loses the sale.
According to Sucuri, this new technique has been used on stores running WordPress WooCommerce and Prestashop. A similar phishing page was detected when trying to pay with PayPal.
This attack doesn’t target credit cards only. At the top of the order form you can see that they also accept PayPal. If you click on the PayPal button you’ll see the PayPal login page. Again, on the cwcargo site instead of paypal.com.
The worst thing is that, according to Sucuri, the real number of affected sites could be much bigger than originally thought because it is almost impossible to identify infected websites.
How to Stay Protected against Phishing and Infected Pages
Security researchers’ advice is being extra cautious during every step of online shopping. Follow these simple steps:
- Inspect the URLs in the address bar;
- Check whether the order form mentions what you’re paying for, your order amount and the name of the seller;
- If you notice something irregular, resume your shopping activities and navigate away from that page;
- If you’re a webmaster of an e-commerce platform, employ integrity control on your site files so that you can detect unwanted changes immediately.