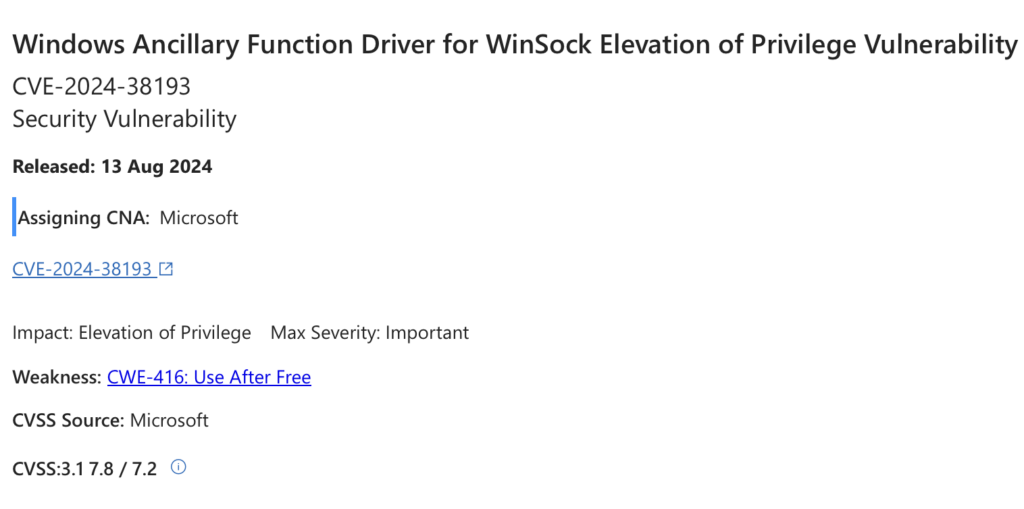
A newly patched security vulnerability in Microsoft Windows has been actively exploited by the Lazarus Group, a notorious state-sponsored hacking group associated with North Korea. The flaw, identified as CVE-2024-38193 and rated with a CVSS score of 7.8, is a privilege escalation bug in the Windows Ancillary Function Driver (AFD.sys) for WinSock.
CVE-2024-38193 Explained
A newly patched security vulnerability in Microsoft Windows has been actively exploited by the Lazarus Group, a notorious state-sponsored hacking group associated with North Korea. The flaw, identified as CVE-2024-38193 and rated with a CVSS score of 7.8, is a privilege escalation bug in the Windows Ancillary Function Driver (AFD.sys) for WinSock.
This critical vulnerability allows attackers to gain SYSTEM-level privileges, providing unauthorized access to sensitive areas of a compromised system. Microsoft addressed this flaw as part of its monthly Patch Tuesday update, highlighting the importance of regularly updating systems to mitigate security risks.
Researchers from Gen Digital, including Luigino Camastra and Milánek, are credited with discovering and reporting the flaw. Gen Digital, known for owning popular security brands such as Norton, Avast, Avira, AVG, ReputationDefender, and CCleaner, noted that the vulnerability was exploited as early as June 2024. The vulnerability enabled attackers to bypass standard security measures and access restricted system components that are typically off-limits to both users and administrators.
The attacks exploiting this vulnerability were notable for the deployment of a rootkit known as FudModule, which is designed to evade detection. While the technical specifics of the attacks remain unclear, this method of exploitation is similar to a previous vulnerability, CVE-2024-21338, which Microsoft patched in February 2024. That vulnerability, a Windows kernel privilege escalation flaw in the AppLocker driver (appid.sys), was also leveraged by the Lazarus Group to install the FudModule rootkit.
These attacks are significant because they extend beyond the typical Bring Your Own Vulnerable Driver (BYOVD) tactics. Rather than using a driver introduced by the attacker, the Lazarus Group exploited flaws in existing drivers already present on Windows hosts. This method provides an efficient way to bypass security protocols, making it more challenging for security solutions to detect and prevent these intrusions.
Further investigation into these attacks revealed that the FudModule rootkit is typically delivered via a remote access trojan (RAT) called Kaolin RAT. According to previous research by Avast, the Lazarus Group uses FudModule selectively, deploying it only under specific conditions to avoid unnecessary exposure.
With the Lazarus Group continuing to target critical vulnerabilities, it remains essential for organizations and individuals to stay vigilant and apply security patches promptly.
This critical vulnerability allows attackers to gain SYSTEM-level privileges, providing unauthorized access to sensitive areas of a compromised system. Microsoft addressed this flaw as part of its monthly Patch Tuesday update, highlighting the importance of regularly updating systems to mitigate security risks.
Researchers from Gen Digital, including Luigino Camastra and Milánek, are credited with discovering and reporting the flaw. Gen Digital, known for owning popular security brands such as Norton, Avast, Avira, AVG, ReputationDefender, and CCleaner, noted that the vulnerability was exploited as early as June 2024. The vulnerability enabled attackers to bypass standard security measures and access restricted system components that are typically off-limits to both users and administrators.
CVE-2024-21338-Based Attacks
The attacks exploiting this vulnerability were notable for the deployment of a rootkit known as FudModule, which is designed to evade detection. While the technical specifics of the attacks remain unclear, this method of exploitation is similar to a previous vulnerability, CVE-2024-21338, which Microsoft patched in February 2024. That vulnerability, a Windows kernel privilege escalation flaw in the AppLocker driver (appid.sys), was also leveraged by the Lazarus Group to install the FudModule rootkit.
These attacks are significant because they extend beyond the typical Bring Your Own Vulnerable Driver (BYOVD) tactics. Rather than using a driver introduced by the attacker, the Lazarus Group exploited flaws in existing drivers already present on Windows hosts. This method provides an efficient way to bypass security protocols, making it more challenging for security solutions to detect and prevent these intrusions.
Further investigation into these attacks revealed that the FudModule rootkit is typically delivered via a remote access trojan (RAT) called Kaolin RAT. According to previous research by Avast, the Lazarus Group uses FudModule selectively, deploying it only under specific conditions to avoid unnecessary exposure.
With the Lazarus Group continuing to target critical vulnerabilities, it remains essential for organizations and individuals to stay vigilant and apply security patches promptly.


